A sophisticated multi-stage malware campaign is currently targeting organizations worldwide, utilizing the PhantomVAI Loader to distribute various information-stealing malware. This campaign poses a significant threat to sectors such as manufacturing, education, healthcare, technology, utilities, and government.
Evolution of PhantomVAI Loader
Initially identified as Katz Stealer Loader, this malware has evolved to deliver multiple infostealer variants, including AsyncRAT, XWorm, FormBook, and DCRat. This evolution underscores its versatility and the increasing complexity of cyber threats.
Infection Chain and Techniques
The attack begins with phishing emails that contain malicious attachments disguised as legitimate business communications. These emails often use social engineering themes such as sales inquiries, payment notifications, and legal matters to entice recipients into opening archived JavaScript or VBS files.
A notable aspect of these attacks is the use of homograph techniques, where attackers replace Latin characters with visually similar Unicode characters. This method effectively bypasses email security filters, increasing the likelihood of successful infection.
Multi-Stage Infection Process
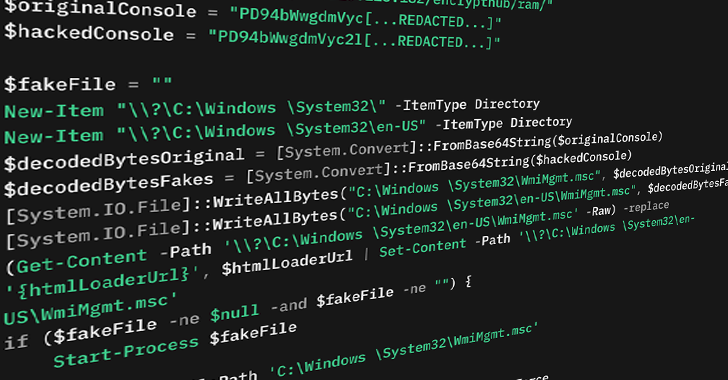
Once the malicious attachment is opened, heavily obfuscated scripts execute Base64-encoded PowerShell commands. These commands download what appears to be an innocuous GIF or image file from attacker-controlled servers. However, these image files conceal the loader payload using steganography techniques, embedding Base64-encoded DLL files within the image data between specific delimiter strings such as `<
Evasion and Persistence Mechanisms
The PowerShell script extracts and decodes the embedded text, loading the PhantomVAI Loader DLL written in C#. The loader executes a method called VAI, which performs several critical functions before deploying the final payload.
To evade detection, the loader conducts comprehensive virtual machine detection checks, examining system attributes like computer information, BIOS details, hard disk characteristics, and Windows services. If it detects a virtualized environment, the loader immediately terminates.
For persistence, the loader establishes scheduled tasks that execute PowerShell commands to download and run files from attacker-controlled URLs or creates Windows Registry Run keys.
Payload Deployment
The final payload is downloaded from a command-and-control server and injected into legitimate system processes using process hollowing, most commonly targeting MSBuild.exe in the .NET Framework directory. This technique allows the malware to operate undetected while executing its information-stealing capabilities.
Implications and Recommendations
The PhantomVAI Loader campaign highlights the increasing sophistication of cyber threats and the need for robust cybersecurity measures. Organizations are advised to enhance email security protocols, educate employees on recognizing phishing attempts, and implement advanced threat detection systems to mitigate the risk posed by such multi-stage malware attacks.