Cybercriminals Exploit Fake Windows Update Screens to Deploy Stealthy Malware
A sophisticated cyberattack campaign has emerged, leveraging counterfeit Windows Update screens and advanced steganography techniques to infiltrate systems with information-stealing malware such as LummaC2 and Rhadamanthys. This method, known as a ClickFix attack, manipulates users into executing malicious commands, initiating a covert, multi-stage infection process that often evades traditional security measures.
Understanding ClickFix Attacks
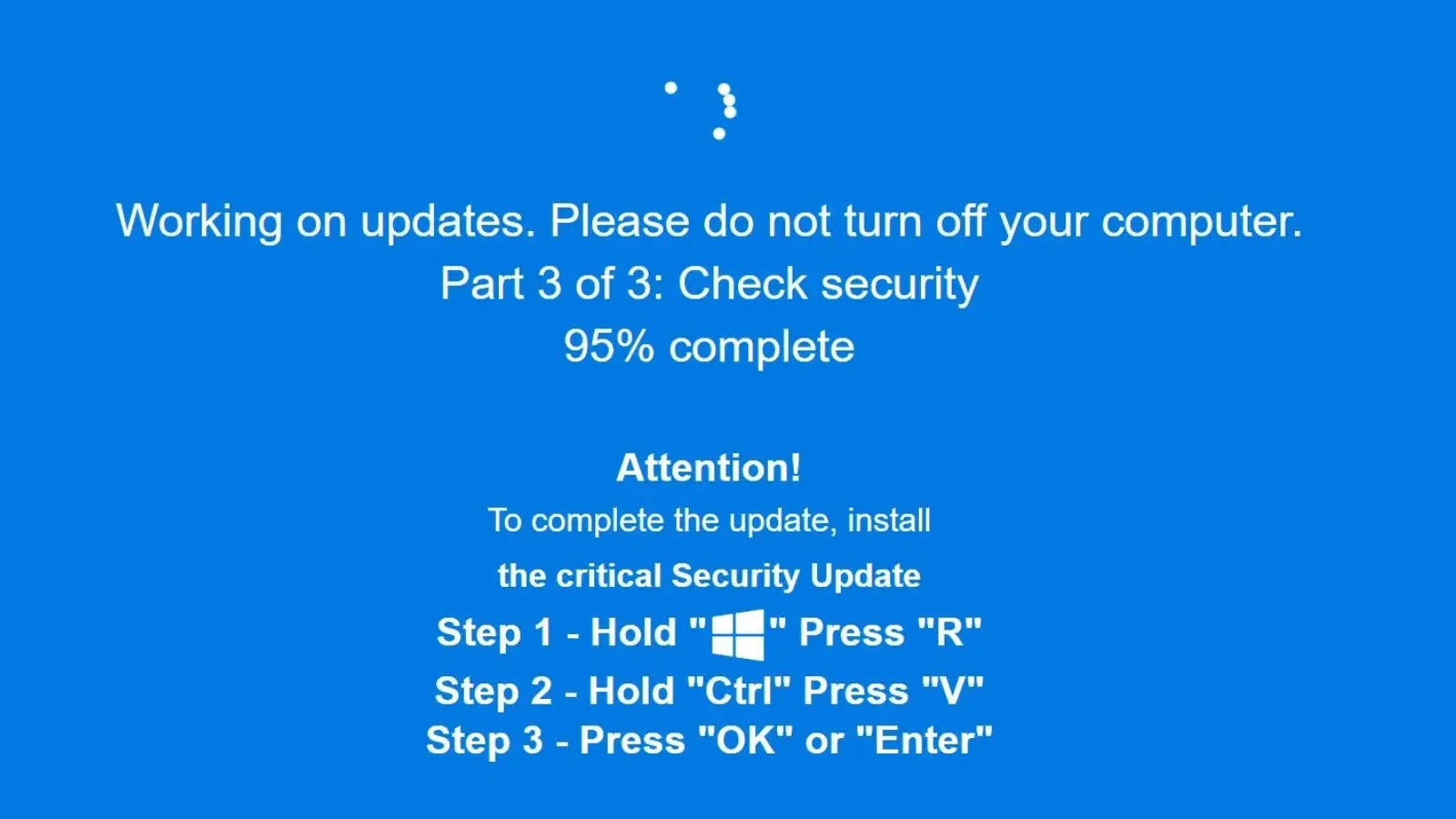
ClickFix attacks are a form of social engineering where deceptive web pages prompt users to press the Windows key and ‘R’ simultaneously, paste a pre-copied command from their clipboard, and execute it. This tactic exploits user trust and familiarity with routine system operations to deploy malware.
Initially, these attacks presented as simple Human Verification prompts. However, recent iterations have evolved to display full-screen, blue Windows Update-like interfaces, complete with realistic progress indicators. Once the fake update appears to complete, users are instructed to follow the familiar pattern of executing a command via the Run dialog box.
The Infection Chain
The malicious command typically launches ‘mshta.exe’ with a URL containing a hex-encoded IP address, initiating a sequence that downloads obfuscated PowerShell scripts and .NET loaders. This method relies on legitimate Windows utilities, often referred to as living off the land binaries, to blend malicious activities with normal system operations, thereby reducing the likelihood of detection.
Steganography: Concealing Malware in Images
A notable aspect of this campaign is its use of steganography to hide malicious code within PNG image files. The attack employs a .NET steganographic loader that decrypts an embedded PNG resource, extracts raw bitmap data, and reconstructs shellcode from specific color channels using a custom XOR-based routine. This shellcode is then injected into processes like ‘explorer.exe’ through dynamically compiled C# code that utilizes standard Windows APIs such as ‘VirtualAllocEx’, ‘WriteProcessMemory’, and ‘CreateRemoteThread’.
In observed instances, this final payload has delivered information-stealing malware like LummaC2 and Rhadamanthys.
Campaign Infrastructure and Persistence
Security researchers have been monitoring these ClickFix campaigns since early October, noting consistent use of the IP address 141.98.80[.]175 and varying paths like ‘/tick.odd’, ‘/gpsc.dat’, and ‘/one.dat’ for the initial ‘mshta.exe’ stage. Subsequent PowerShell stages have been hosted on domains such as ‘securitysettings[.]live’ and ‘xoiiasdpsdoasdpojas[.]com’, all linking back to the same backend infrastructure.
These campaigns continued even after Operation Endgame 3.0, which targeted Rhadamanthys’ infrastructure in mid-November, disrupting servers and seizing domains associated with the stealer. Despite the takedown, active domains still served the Windows Update ClickFix lure, though the Rhadamanthys payload itself appeared to be unavailable.
Mitigation Strategies
Given that this attack relies on user interaction with the Run dialog, one effective countermeasure is to disable the Windows Run box via Group Policy or registry settings, such as configuring the ‘NoRun’ policy under the Explorer key.
Security teams should also monitor Endpoint Detection and Response (EDR) telemetry for instances where ‘explorer.exe’ spawns ‘mshta.exe’, ‘powershell.exe’, or other scripting binaries with suspicious command lines.
User education is crucial: employees should be informed that legitimate CAPTCHA checks or Windows Update processes will never require pasting commands into the Run prompt from a web page.
During investigations, analysts can further validate potential ClickFix abuse by reviewing the ‘RunMRU’ registry key, which records recent commands executed via the Run dialog.
Conclusion
The evolution of ClickFix attacks underscores the increasing sophistication of cyber threats that exploit user trust and system functionalities. By combining realistic fake Windows Update screens with steganography, attackers can deploy malware stealthily, often bypassing traditional security defenses. Organizations must adopt a multi-layered security approach, including technical controls, vigilant monitoring, and comprehensive user education, to effectively mitigate these threats.