New MacSync Stealer Exploits Signed macOS Apps to Evade Security and Exfiltrate Data Cybersecurity researchers have recently identified an advanced variant of the MacSync malware […]
Category: Cybersecurity News
Stay informed about the ever-evolving world of digital threats and defenses with our Cyber Security News category. Here, you’ll find the latest breaking news, in-depth analysis, and expert insights on everything related to cybersecurity. From data breaches and ransomware attacks to emerging threats and innovative security solutions, we cover the critical issues impacting individuals, businesses, and governments worldwide. Keep up-to-date on the latest vulnerabilities, best practices, and trends shaping the future of online security.
Massive Instagram Data Breach Exposes 17.5 Million Accounts, Sensitive Info Circulating on Dark Web
Massive Instagram Data Breach Exposes 17.5 Million User Accounts In a significant cybersecurity incident, approximately 17.5 million Instagram user accounts have been compromised, leading to […]
Europol-Assisted Operation Dismantles Black Axe Criminal Network in Spain, 34 Arrests Made
Europol-Backed Operation Dismantles Black Axe Criminal Network in Spain In a significant blow to international organized crime, the Spanish National Police, in collaboration with the […]
Massive Data Breach at Texas Gas Station Operator Exposes 377,000 Customers’ Information
Massive Data Breach at Texas Gas Station Operator Compromises Over 377,000 Customers’ Information In a significant cybersecurity incident, Gulshan Management Services, Inc., a gas station […]
BreachForums User Database Leaked: Over 323,000 Accounts Exposed in Major Dark Web Breach
BreachForums’ User Database Exposed: A Cybercriminal Haven Compromised In a striking development within the cybercrime community, a hacker identified as James has publicly released the […]
WhatsApp Worm Spreads Astaroth Banking Trojan in Brazil, Exploits Trusted Contacts for Rapid Malware Distribution
WhatsApp Worm Propagates Astaroth Banking Trojan Across Brazil Cybersecurity experts have recently uncovered a sophisticated campaign leveraging WhatsApp to disseminate the Astaroth banking trojan, primarily […]
Iranian Hackers Exploit Vulnerabilities, Target Israel, U.S. Agencies, and More in Week’s Cybersecurity News
Cybersecurity Weekly Recap: RustFS Vulnerability, Iranian Cyber Operations, and Emerging Threats In the ever-evolving landscape of cybersecurity, the past week has unveiled a series of […]
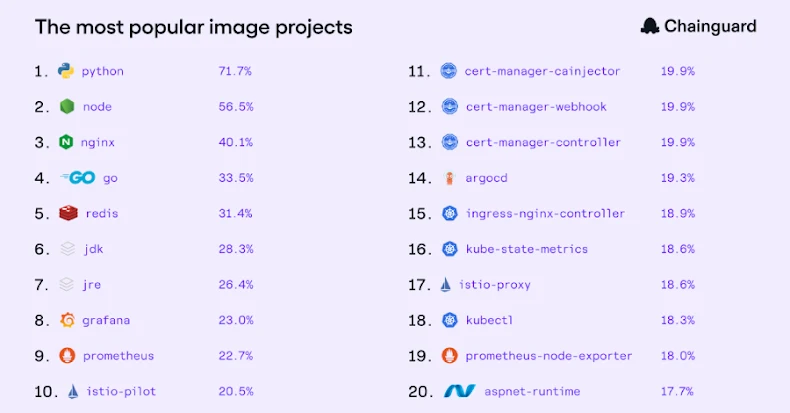
Chainguard Report Highlights Security Challenges in Diverse Open-Source Software Usage
Navigating the Complexities of Trusted Open Source: Insights from Chainguard’s Latest Report In the rapidly evolving landscape of open-source software, understanding how organizations utilize and […]
Malicious npm Packages Deploy NodeCordRAT to Target Cryptocurrency Enthusiasts
Unveiling NodeCordRAT: Malicious npm Packages Targeting Cryptocurrency Enthusiasts In a recent cybersecurity revelation, researchers have identified three malicious npm packages designed to deploy a previously […]
OpenAI Launches ChatGPT Health for Secure, Personalized Health Conversations
OpenAI Introduces ChatGPT Health: A Secure Platform for Personalized Health Conversations On January 8, 2026, OpenAI unveiled ChatGPT Health, a specialized platform designed to facilitate […]