OpenAI Introduces Ads in ChatGPT for U.S. Users on Free and Go Plans In a significant shift in its business model, OpenAI has announced plans […]
Category: Cybersecurity News
Stay informed about the ever-evolving world of digital threats and defenses with our Cyber Security News category. Here, you’ll find the latest breaking news, in-depth analysis, and expert insights on everything related to cybersecurity. From data breaches and ransomware attacks to emerging threats and innovative security solutions, we cover the critical issues impacting individuals, businesses, and governments worldwide. Keep up-to-date on the latest vulnerabilities, best practices, and trends shaping the future of online security.
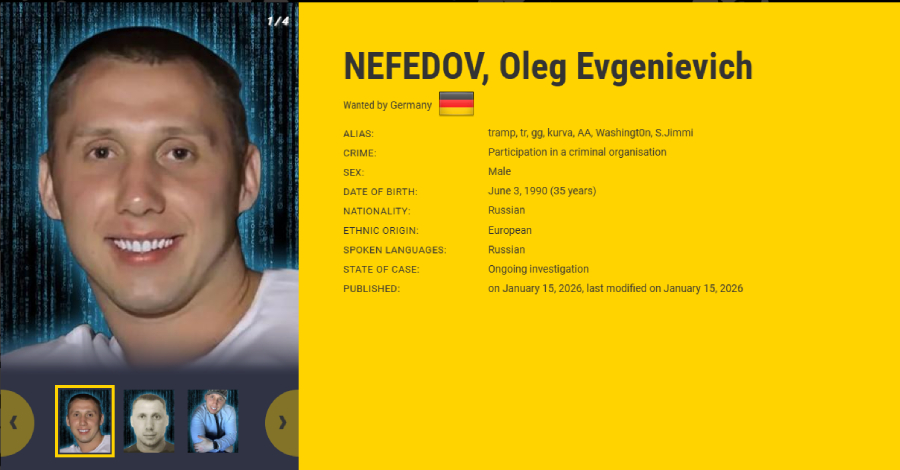
International Manhunt for Black Basta Leader Intensifies as EU, INTERPOL Issue Red Notices
International Manhunt Intensifies for Black Basta Ransomware Leader In a significant escalation of international efforts to combat cybercrime, Ukrainian and German law enforcement agencies have […]
Researchers Infiltrate StealC Malware Network, Unmask Operator ‘YouTubeTA’ in Major Cybersecurity Breakthrough
Researchers Infiltrate StealC Malware Infrastructure, Unmasking Operator In a significant breakthrough, cybersecurity experts have successfully penetrated the command-and-control (C2) systems of StealC, a notorious information-stealing […]
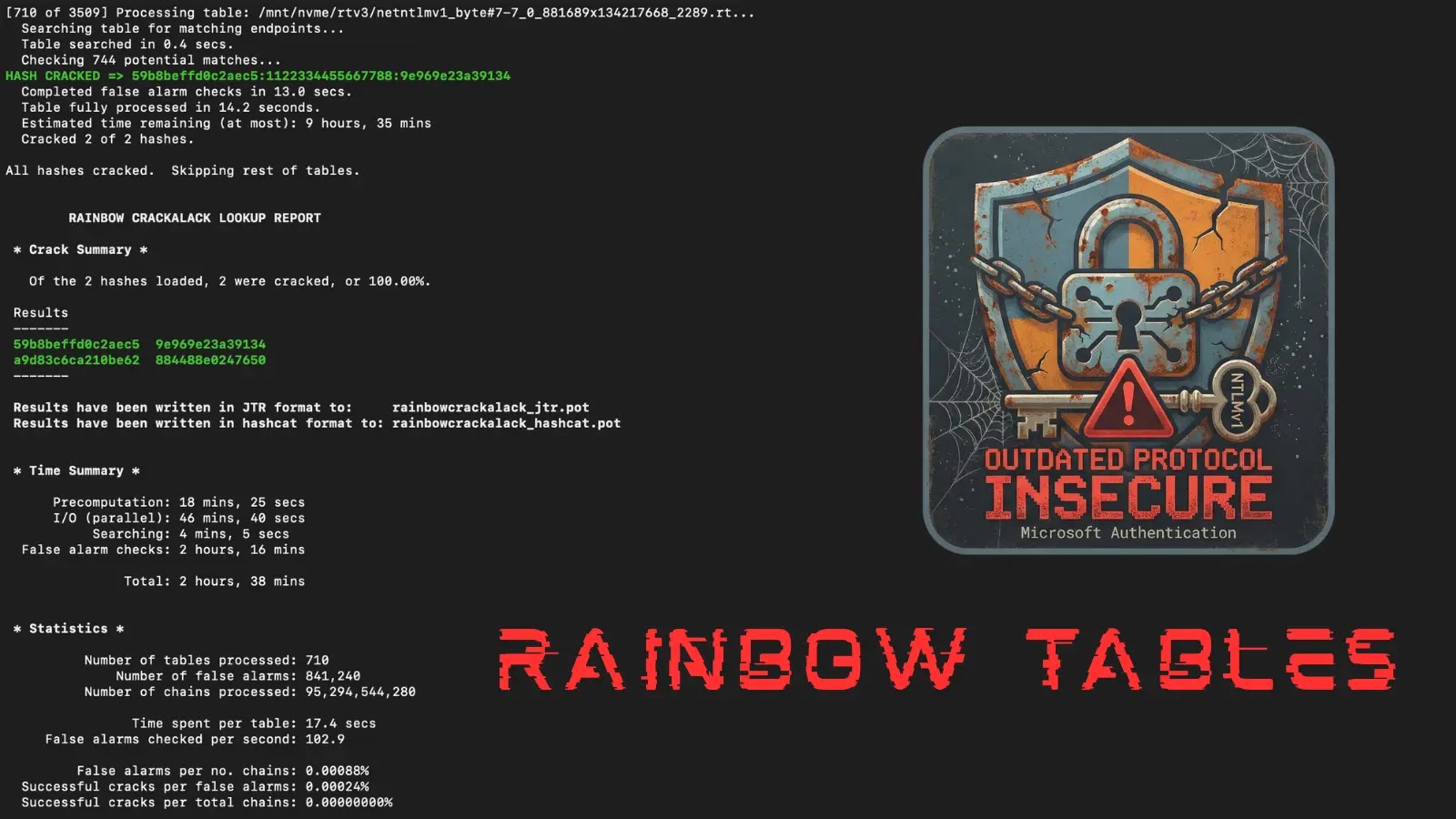
Mandiant Releases NTLMv1 Rainbow Tables, Urging Firms to Abandon Outdated Security Protocols
Mandiant’s Release of NTLMv1 Rainbow Tables Highlights Urgent Security Risks In a significant move to underscore the vulnerabilities of outdated authentication protocols, Mandiant, a subsidiary […]
Let’s Encrypt Launches 6-Day IP-Based TLS Certificates to Boost Security and Flexibility
Let’s Encrypt Introduces 6-Day IP-Based TLS Certificates for Enhanced Security In a significant advancement for internet security, Let’s Encrypt, a leading provider of free TLS […]
Critical Security Flaw in Google’s Vertex AI Enables Privilege Escalation, Posing Threat to Organizations
Critical Vulnerability in Google’s Vertex AI Allows Privilege Escalation A significant security vulnerability has been identified in Google’s Vertex AI platform, enabling users with minimal […]
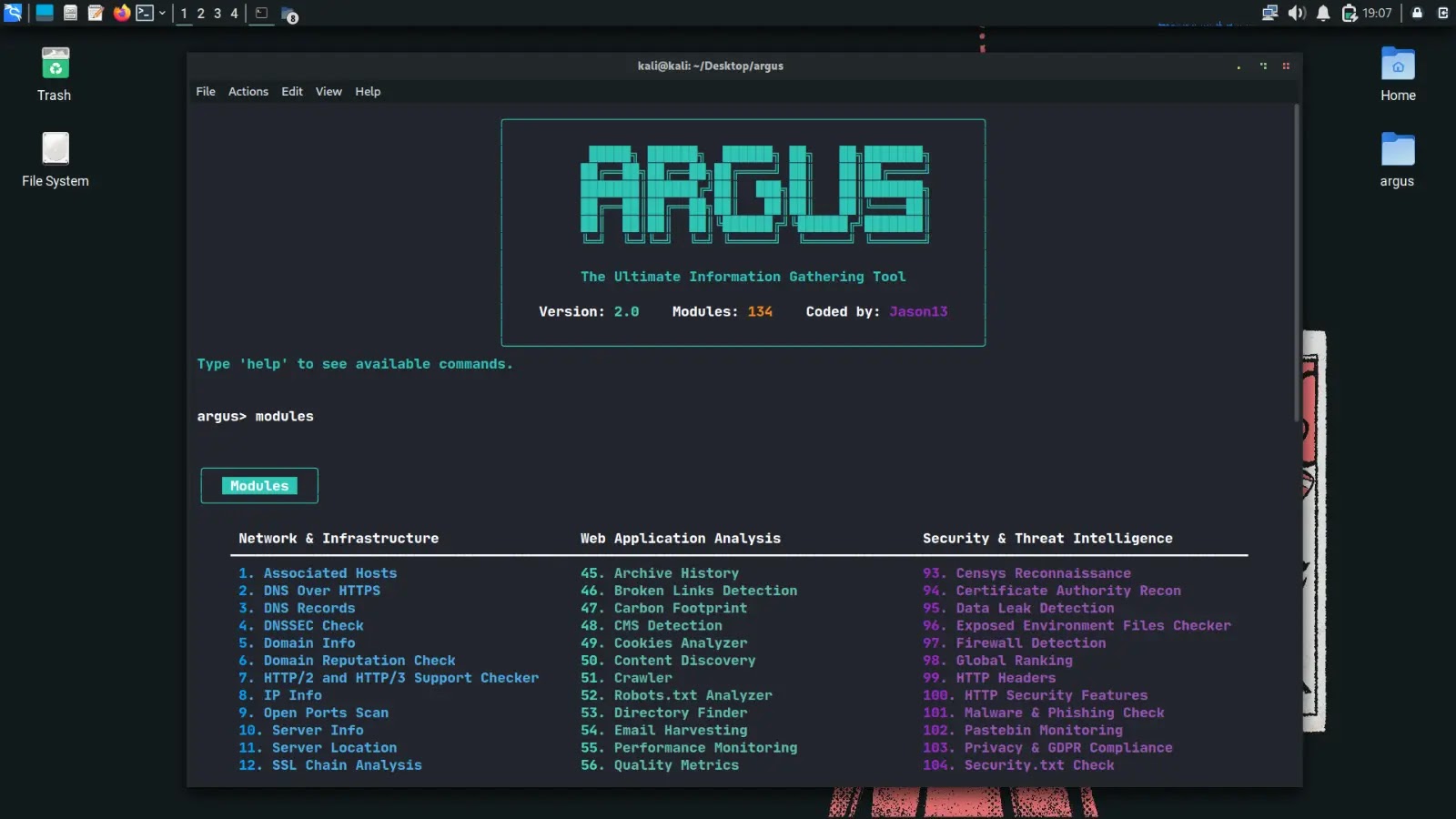
Argus 2.0: Enhanced Python Toolkit Unveiled for Comprehensive Cybersecurity Reconnaissance
Argus 2.0: The Ultimate Python Toolkit for Comprehensive Cybersecurity Reconnaissance In the ever-evolving landscape of cybersecurity, the need for robust and versatile tools is paramount. […]
Safeguard Your Personal Data: Tips for Online Privacy Protection and Safety
Protecting Your Privacy: How to Safeguard Your Personal Information Online In today’s digital age, safeguarding your personal information is as crucial as locking your doors […]
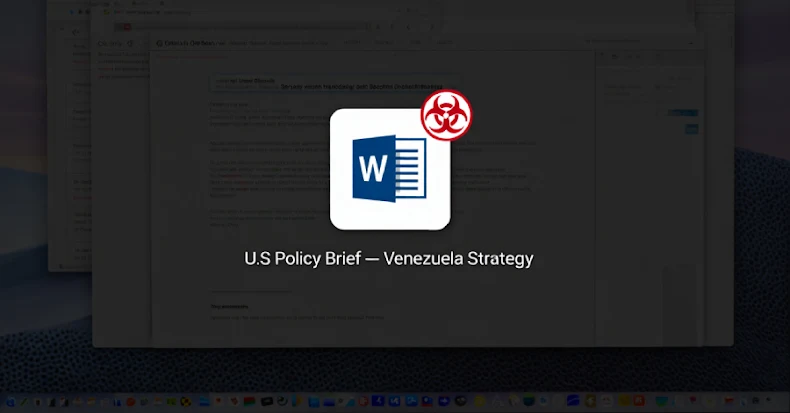
Chinese Cyber Group Uses LOTUSLITE Backdoor Against US Policy Experts in Venezuela-Themed Phishing Campaign
Chinese Cyber Espionage Group Targets U.S. Policy Experts with LOTUSLITE Backdoor via Venezuela-Themed Phishing In a recent cybersecurity development, U.S. government and policy entities have […]
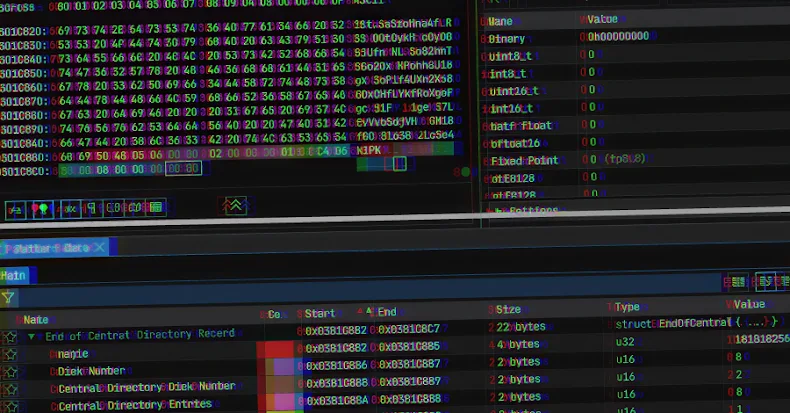
GootLoader Malware Uses Advanced ZIP Techniques to Evade Detection
GootLoader Malware Employs Advanced ZIP Archive Techniques to Evade Detection GootLoader, a JavaScript-based malware loader, has recently adopted sophisticated methods to bypass security measures, notably […]