Cybercriminals Disguise Remcos RAT as VeraCrypt Installers to Steal User Credentials A sophisticated cyberattack campaign has been identified, primarily targeting South Korean users by distributing […]
Category: Cybersecurity News
Stay informed about the ever-evolving world of digital threats and defenses with our Cyber Security News category. Here, you’ll find the latest breaking news, in-depth analysis, and expert insights on everything related to cybersecurity. From data breaches and ransomware attacks to emerging threats and innovative security solutions, we cover the critical issues impacting individuals, businesses, and governments worldwide. Keep up-to-date on the latest vulnerabilities, best practices, and trends shaping the future of online security.
Pulsar RAT: New Stealth Malware Poses Global Threat to Windows Systems
Pulsar RAT: The Stealthy Malware Redefining Remote Access Threats In the ever-evolving landscape of cyber threats, a new and sophisticated malware known as Pulsar RAT […]
Kerberos Vulnerability Exploits DNS CNAME, Poses Security Threat to Windows Environments
Critical Kerberos Relay Attack Exploits DNS CNAME to Bypass Security Measures A significant vulnerability has been identified in Windows Kerberos authentication, expanding the potential for […]
Leaks Expose Hidden Ransomware Infrastructures and Key Players, Prompting Global Sanctions
Unveiling the Shadows: Leaks Reveal the Hidden Infrastructure of Ransomware Operations The clandestine world of cybercrime thrives on secrecy and intricate networks. However, internal discord […]
Google Gemini Flaw Risks Private Calendar Data via Malicious Invites Exploiting AI Vulnerability
Google Gemini Vulnerability Exposes Private Calendar Data Through Malicious Invites A critical security flaw within Google’s ecosystem has been uncovered, allowing attackers to circumvent Google […]
OpenAI Launches ChatGPT Go: Affordable Ad-Supported AI Plan Sparks Privacy Concerns
OpenAI’s ChatGPT Go: Affordable AI with Ad-Supported Model Raises Privacy Concerns OpenAI has introduced ChatGPT Go, a budget-friendly subscription plan priced at $8 USD per […]
Attackers Exploit WSL2 to Bypass Windows Security, Remain Hidden
Cybercriminals Exploit WSL2 to Evade Detection in Windows Environments The Windows Subsystem for Linux 2 (WSL2) was designed to provide developers with a robust Linux […]
Critical RCE Vulnerability Found in Apache bRPC; Urgent Upgrade to 1.15.0 Advised
Critical Remote Command Injection Vulnerability Discovered in Apache bRPC A critical security vulnerability has been identified in Apache bRPC’s built-in heap profiler service, affecting all […]
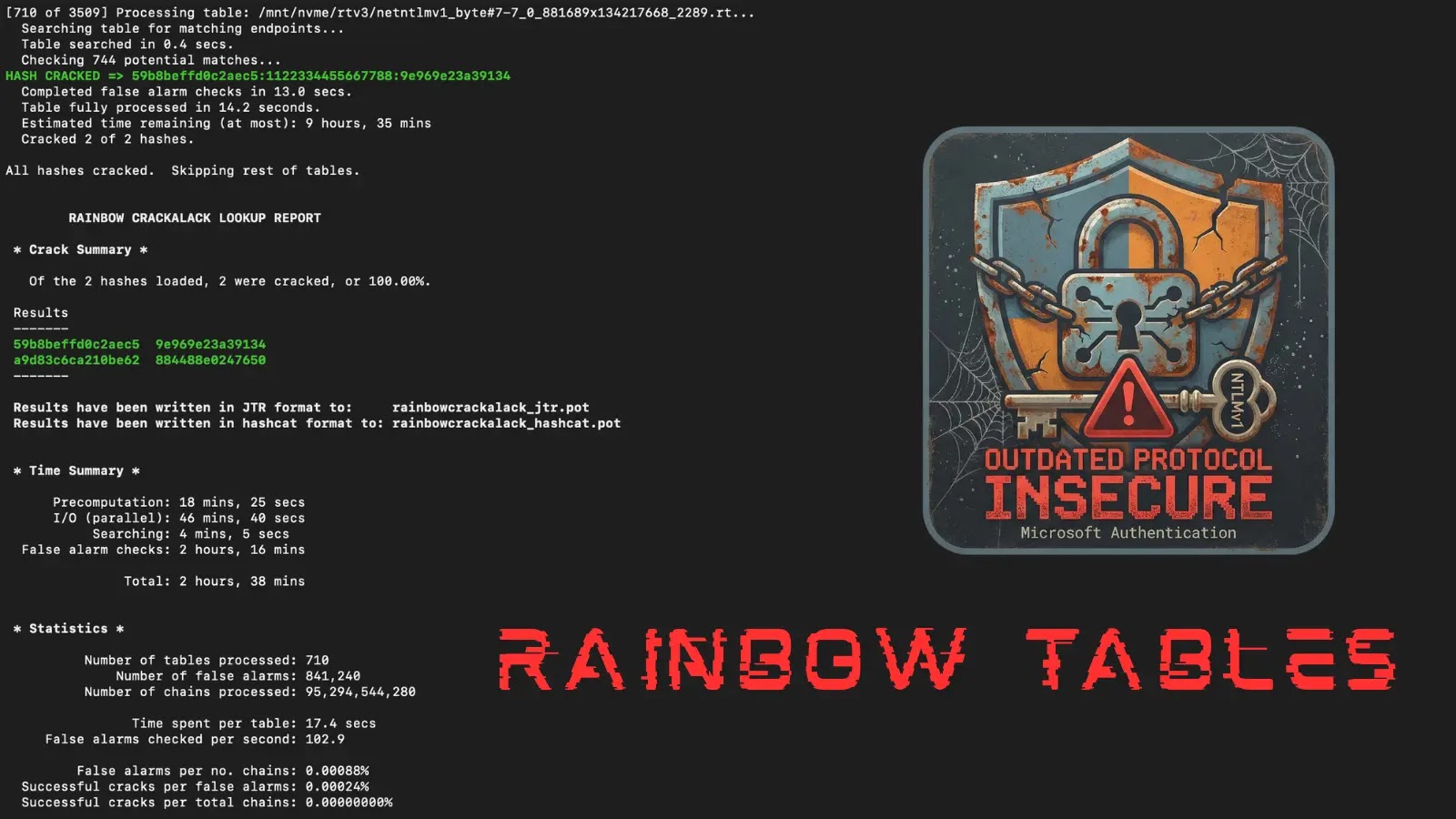
Mandiant Reveals NTLMv1 Rainbow Tables, Amplifying Urgency to Upgrade Insecure Protocols
Mandiant’s Release of Rainbow Tables Exposes Critical NTLMv1 Vulnerabilities In a significant move to highlight the vulnerabilities of outdated authentication protocols, Mandiant, a subsidiary of […]
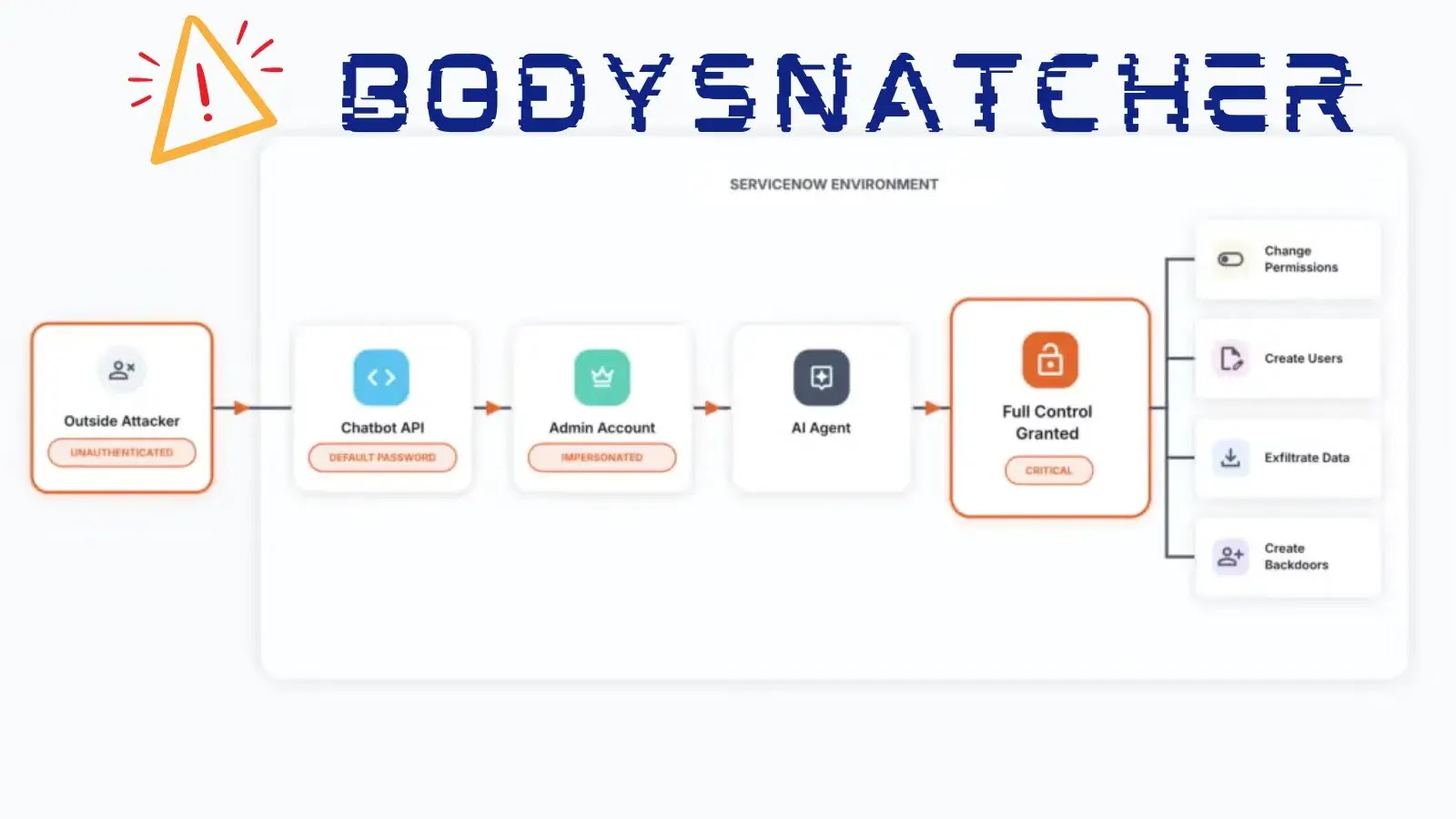
BodySnatcher’ Vulnerability in ServiceNow Lets Attackers Impersonate Users; Patch Released
Critical ‘BodySnatcher’ Vulnerability in ServiceNow Allows Unauthenticated User Impersonation A significant security flaw, designated as CVE-2025-12420 and dubbed BodySnatcher, has been identified in ServiceNow’s Virtual […]