Everest Ransomware Group Claims Massive Data Breach at McDonald’s India In a significant cybersecurity incident, the Everest ransomware group has alleged a substantial data breach […]
Category: Cybersecurity News
Stay informed about the ever-evolving world of digital threats and defenses with our Cyber Security News category. Here, you’ll find the latest breaking news, in-depth analysis, and expert insights on everything related to cybersecurity. From data breaches and ransomware attacks to emerging threats and innovative security solutions, we cover the critical issues impacting individuals, businesses, and governments worldwide. Keep up-to-date on the latest vulnerabilities, best practices, and trends shaping the future of online security.
Hacker Guilty of Breaching Supreme Court Systems, Sharing Data on Instagram; Faces Prison
Hacker Admits to Breaching Supreme Court Systems and Sharing Sensitive Data on Instagram In a significant cybersecurity breach, Nicholas Moore, a 24-year-old from Springfield, Tennessee, […]
Gootloader Malware Returns with Advanced Evasion Techniques, Threatening Global Cybersecurity
Gootloader Resurfaces with Advanced Evasion Tactics, Bypassing Modern Security Measures After a period of dormancy, the Gootloader malware has reemerged in November 2025, showcasing enhanced […]
CISA Releases BRICKSTORM Malware Report with New YARA Rules for Protecting VMware vSphere Systems
CISA Unveils BRICKSTORM Malware Report: New YARA Rules for VMware vSphere Protection The Cybersecurity and Infrastructure Security Agency (CISA) has released a comprehensive analysis of […]
Critical Azure Flaw Exposes Key Services to Potential DoS Attacks Due to DNS Issues in Private Endpoint Deployments
Critical Flaw in Azure Private Endpoint Deployments Exposes Resources to Potential DoS Attacks A significant architectural vulnerability has been identified in Microsoft Azure’s Private Endpoint […]
Fortinet Vulnerability Exploited, VoidLink Malware Targets Linux, RedLineCyber Hijacks Crypto, NTLM Hash Cracking Advances
Cybersecurity Weekly Recap: Fortinet Exploits, RedLine Clipjack, NTLM Crack, Copilot Attack & More In the ever-evolving landscape of cybersecurity, the boundary between routine updates and […]
Researchers Uncover XSS Vulnerability in StealC Malware Panel, Exposing Cybercriminal Operations
Exploiting a Security Flaw in StealC Malware Panel: A Deep Dive into Cybercriminal Operations In a significant development within the cybersecurity landscape, researchers have uncovered […]
AMD SEV-SNP Protections Compromised by StackWarp Vulnerability Across Zen 1-5 Processors
StackWarp Vulnerability Undermines AMD SEV-SNP Protections Across Zen 1–5 CPUs A recent study by researchers at the CISPA Helmholtz Center for Information Security in Germany […]
The Costly Impact of DevOps SaaS Downtime on Cloud-First Enterprises: Financial and Operational Risks Explored
The Hidden Costs of DevOps SaaS Downtime: A Wake-Up Call for Cloud-First Businesses In the digital era, cloud services have become the backbone of modern […]
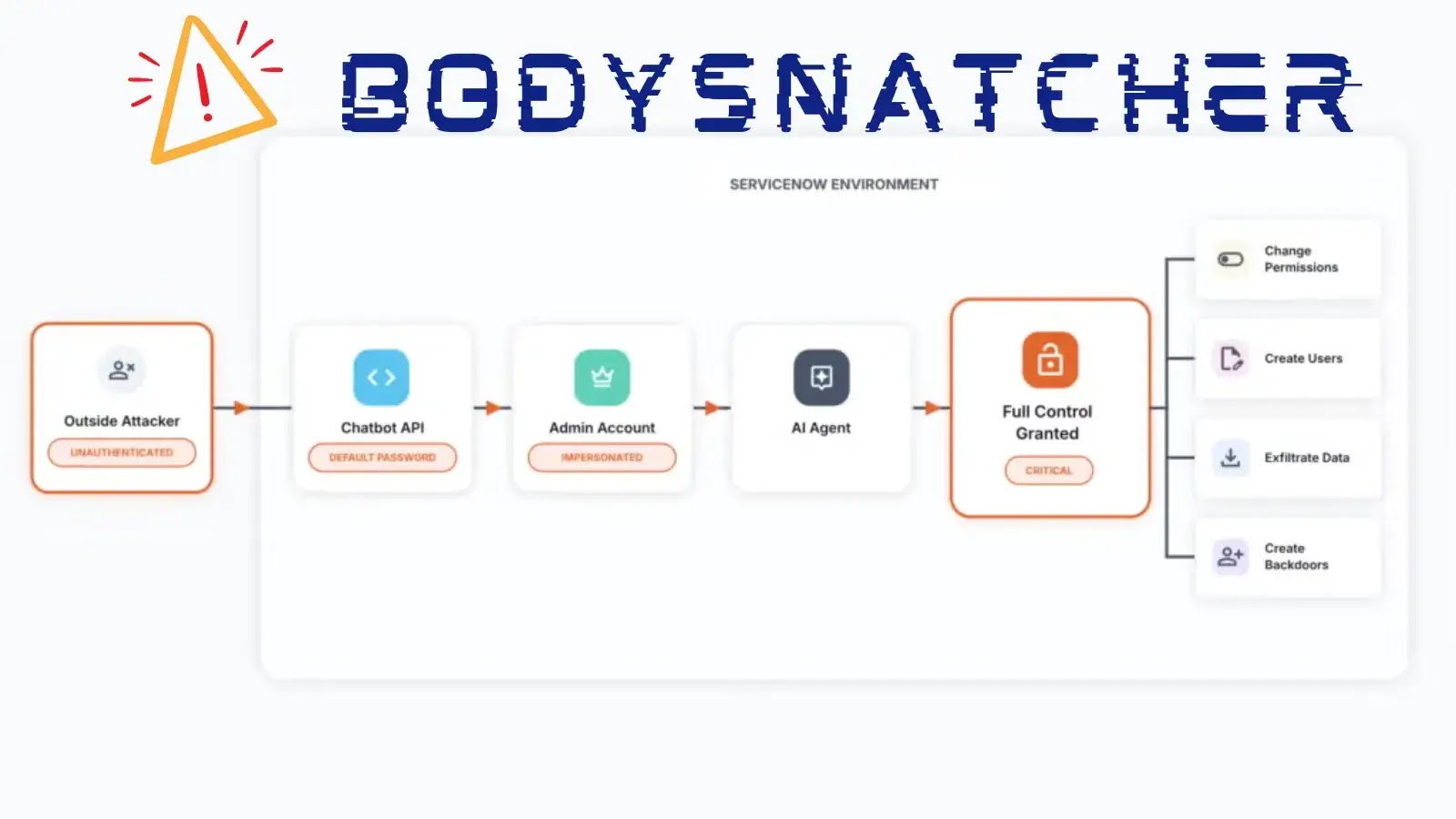
BodySnatcher Vulnerability in ServiceNow Lets Attackers Impersonate Users, Bypass MFA
BodySnatcher Vulnerability: Unauthenticated Attackers Can Impersonate Any ServiceNow User A critical security flaw, designated as CVE-2025-12420 and dubbed BodySnatcher, has been identified in ServiceNow’s Virtual […]