Critical WinRAR Vulnerability Exploited to Gain Control Over Windows Systems A significant security flaw in WinRAR, a widely used file compression tool for Windows, has […]
Category: Cybersecurity News
Stay informed about the ever-evolving world of digital threats and defenses with our Cyber Security News category. Here, you’ll find the latest breaking news, in-depth analysis, and expert insights on everything related to cybersecurity. From data breaches and ransomware attacks to emerging threats and innovative security solutions, we cover the critical issues impacting individuals, businesses, and governments worldwide. Keep up-to-date on the latest vulnerabilities, best practices, and trends shaping the future of online security.
Malicious Chrome Extensions Pose Threat by Stealing ChatGPT Session Tokens
Beware: Malicious Chrome Extensions Masquerading as ChatGPT Enhancements In a recent cybersecurity revelation, researchers have identified a coordinated campaign involving 16 malicious Chrome extensions designed […]
Fortinet Disables FortiCloud SSO Amid Active Zero-Day Threat Exploitation
Fortinet Temporarily Disables FortiCloud SSO Amid Active Exploitation of Zero-Day Vulnerability In response to the active exploitation of a zero-day authentication bypass vulnerability, Fortinet has […]
HoneyMyte Group Upgrades CoolClient Malware to Steal Browser Credentials in Asia and Europe
HoneyMyte Hacker Group Enhances CoolClient Malware to Steal Browser Credentials The HoneyMyte cyber espionage group, also known as Mustang Panda or Bronze President, has intensified […]
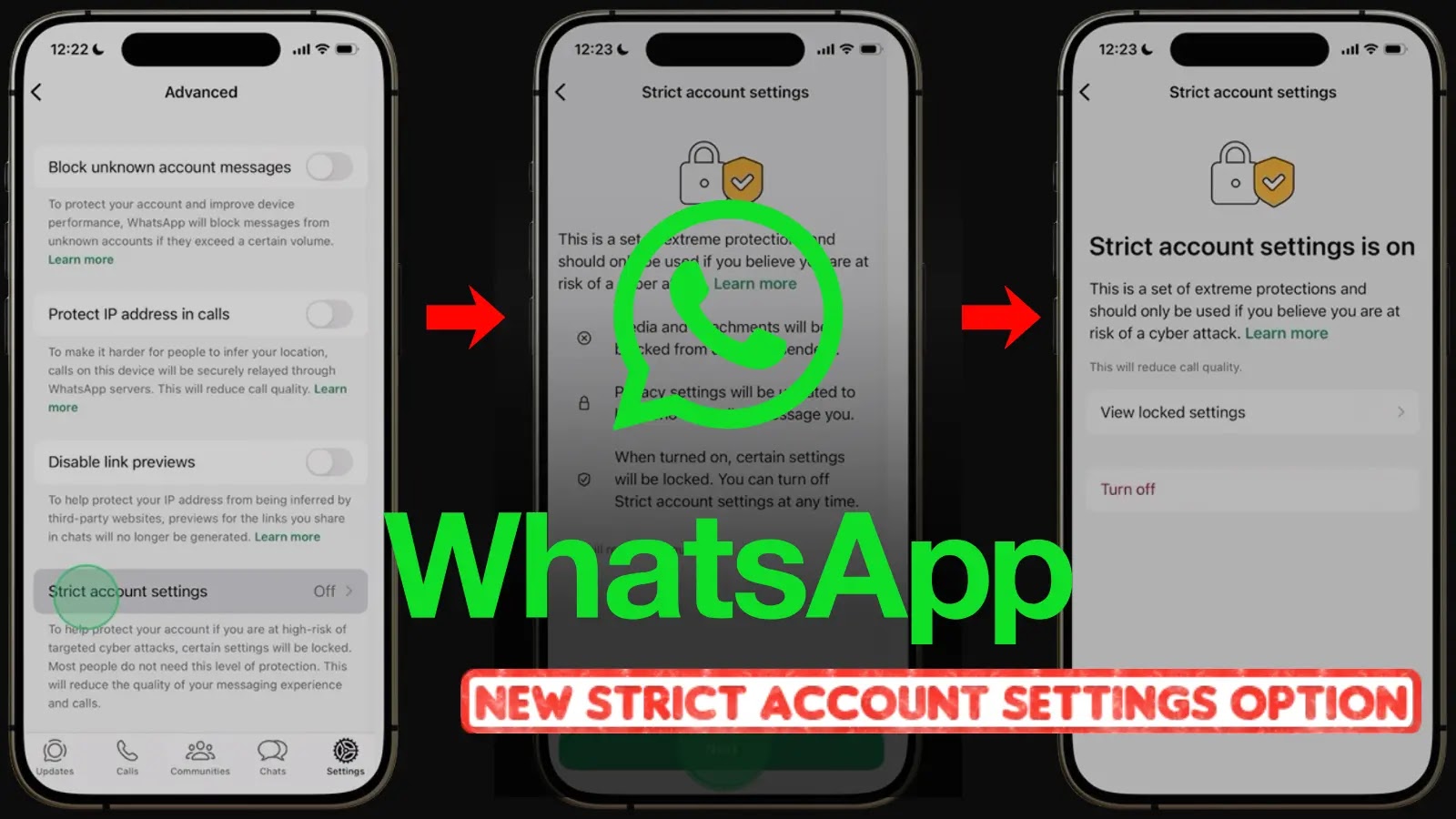
WhatsApp Enhances User Security with New ‘Strict Account Settings’ Feature
WhatsApp Introduces ‘Strict Account Settings’ to Fortify User Security In a significant move to bolster user security, WhatsApp has unveiled a new feature called ‘Strict […]
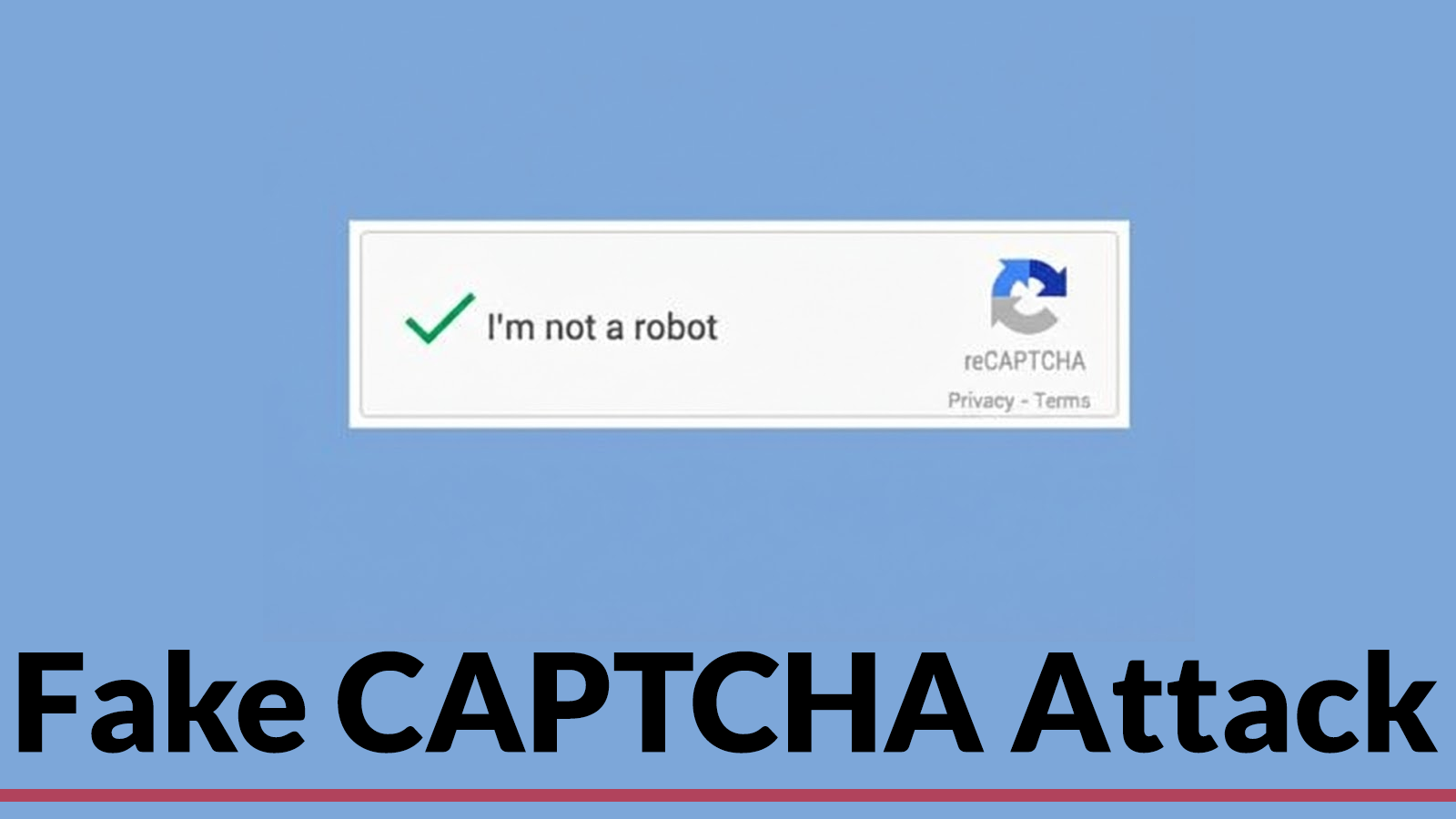
Cybercriminals Use Fake CAPTCHA, Microsoft App-V to Deploy Amatera Stealer Maliciously
Cybercriminals Exploit Fake CAPTCHA and Microsoft App-V to Deploy Amatera Stealer In a newly uncovered cyberattack campaign, threat actors are employing a sophisticated blend of […]
Chinese National Sentenced to 46 Months for $36.9M Crypto Fraud Targeting US Investors
Chinese National Sentenced to 46 Months for Laundering Millions Stolen from American Investors In a significant crackdown on international financial crime, Chinese national Jingliang Su […]
WhatsApp Denies Lawsuit Claims, Reaffirms Commitment to Encrypted Message Privacy
Article Title: WhatsApp Refutes Lawsuit Allegations, Affirms Message Privacy Through End-to-End Encryption WhatsApp, the globally renowned messaging platform, has recently come under legal scrutiny with […]
Memory Leak in ZAP’s JavaScript Engine Impacts Active Scanning, Urgent Fix Issued
Critical Memory Leak in ZAP’s JavaScript Engine Disrupts Active Scanning The Zed Attack Proxy (ZAP), a widely utilized open-source web application security scanner, has recently […]
Critical Vulnerability Found in TP-Link Archer MR600 v5 Routers; Urgent Firmware Update Advised
Critical Vulnerability in TP-Link Archer MR600 v5 Routers: Immediate Action Required A significant security flaw has been identified in TP-Link’s Archer MR600 v5 routers, potentially […]