Stanley Malware Toolkit: A New Threat Hijacking Browsers with Stealth In January 2026, cybersecurity researchers uncovered a sophisticated malware-as-a-service (MaaS) toolkit named Stanley, which poses […]
Category: Cybersecurity News
Stay informed about the ever-evolving world of digital threats and defenses with our Cyber Security News category. Here, you’ll find the latest breaking news, in-depth analysis, and expert insights on everything related to cybersecurity. From data breaches and ransomware attacks to emerging threats and innovative security solutions, we cover the critical issues impacting individuals, businesses, and governments worldwide. Keep up-to-date on the latest vulnerabilities, best practices, and trends shaping the future of online security.
Microsoft Urgently Patches Active Office Zero-Day Vulnerability CVE-2026-21509
Microsoft Releases Emergency Patch for Actively Exploited Office Zero-Day Vulnerability On January 26, 2026, Microsoft issued an urgent out-of-band security update to address a critical […]
Curl Ends Bug Bounty Program Due to AI-Generated Low-Quality Reports Surge
Article Title: Curl Ends Bug Bounty Program Amid Surge of Low-Quality AI-Generated Reports In January 2026, the curl project announced the termination of its bug […]
Clawdbot Vulnerability Exposes 900 Instances: API Keys and Private Chats at Risk
Clawdbot Vulnerability Exposes API Keys and Private Chats: Over 900 Instances at Risk Clawdbot, an open-source AI agent gateway, has recently come under scrutiny due […]
Top VPN Services of 2026: Evaluating Security, Speed, and Affordability for Enhanced Online Privacy
Top 10 VPN Services of 2026: Secure, Fast, and Affordable Options In today’s digital era, safeguarding your online privacy and security is more crucial than […]
Critical Flaw in GNU InetUtils Exposes 800K Telnet Servers to Root Access Exploits
Critical Vulnerability in GNU InetUtils Exposes 800,000 Telnet Servers to Remote Code Execution A severe security flaw has been identified in the telnetd component of […]
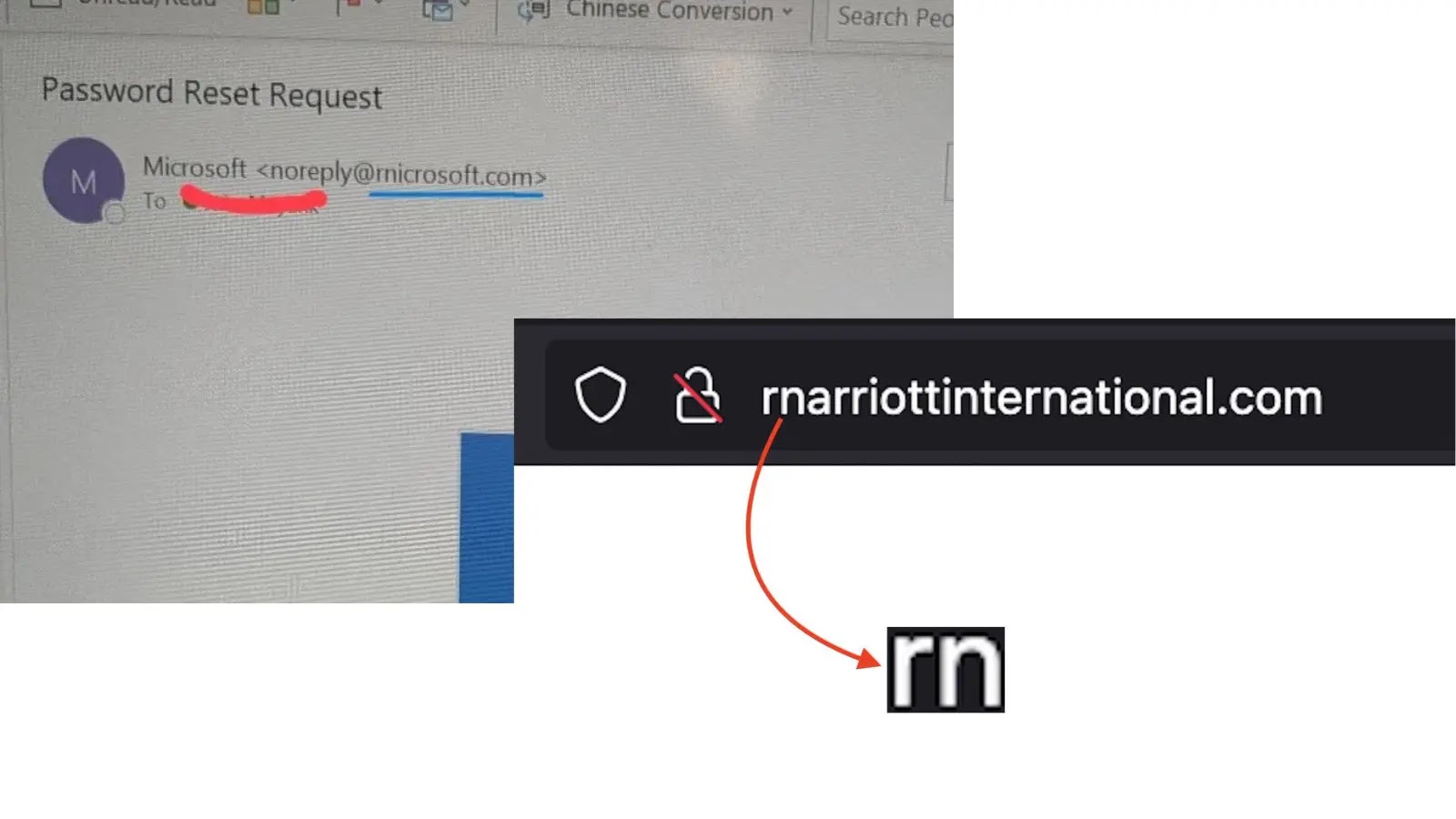
Cybercriminals Use ‘rn’ Typo to Impersonate Microsoft and Marriott in Phishing Attacks
Cybercriminals Exploit ‘rn’ Typo to Mimic Microsoft and Marriott in Sophisticated Phishing Attacks In a recent wave of cyberattacks, threat actors have employed a deceptive […]
Windows 11 Update KB5074109 Causes Critical Boot Failures and System Instabilities
Microsoft is urgently investigating critical stability issues stemming from the January 2026 security update for Windows 11. The update, designated as KB5074109, was intended to […]
AI Agents Demand New Security Models as Enterprise Risks Escalate
Rethinking AI Agent Access: Navigating the New Frontiers of Enterprise Security Artificial Intelligence (AI) agents are revolutionizing workplace efficiency by autonomously scheduling meetings, accessing data, […]
Sandworm’s DynoWiper Attack on Poland’s Energy Sector Thwarted, Gov’t Tightens Cybersecurity Measures
Unveiling DynoWiper: Sandworm’s Unsuccessful Cyber Assault on Poland’s Energy Infrastructure In late December 2025, Poland’s energy sector faced a significant cyber threat attributed to the […]