In mid-September 2025, Microsoft is set to launch a pivotal administrative feature within Microsoft 365, empowering IT administrators to oversee organization-wide sharing permissions for user-created […]
Category: Cybersecurity News
Stay informed about the ever-evolving world of digital threats and defenses with our Cyber Security News category. Here, you’ll find the latest breaking news, in-depth analysis, and expert insights on everything related to cybersecurity. From data breaches and ransomware attacks to emerging threats and innovative security solutions, we cover the critical issues impacting individuals, businesses, and governments worldwide. Keep up-to-date on the latest vulnerabilities, best practices, and trends shaping the future of online security.
KorPlug Malware: Advanced Obfuscation Techniques and Analysis Challenges
KorPlug, a sophisticated malware strain, has recently emerged as a significant threat in the cybersecurity landscape. Employing advanced obfuscation techniques, it effectively evades detection and […]
Cybercriminals Exploit SendGrid to Harvest Login Credentials
A sophisticated credential harvesting campaign has recently emerged, exploiting the trusted reputation of SendGrid, a widely used cloud-based email service platform. By leveraging SendGrid’s legitimate […]
Apple’s Zero-Click RCE Vulnerability: A Deep Dive into CVE-2025-43300
A critical zero-click remote code execution (RCE) vulnerability, identified as CVE-2025-43300, has been discovered within Apple’s image processing infrastructure. This flaw resides in the JPEG […]
Emergence of Mac.c: A New macOS Stealer Offering Rapid Data Exfiltration on the Dark Web
A newly identified macOS-based information stealer, known as Mac.c, has recently appeared on darknet forums, offering rapid data exfiltration capabilities for a subscription fee of […]
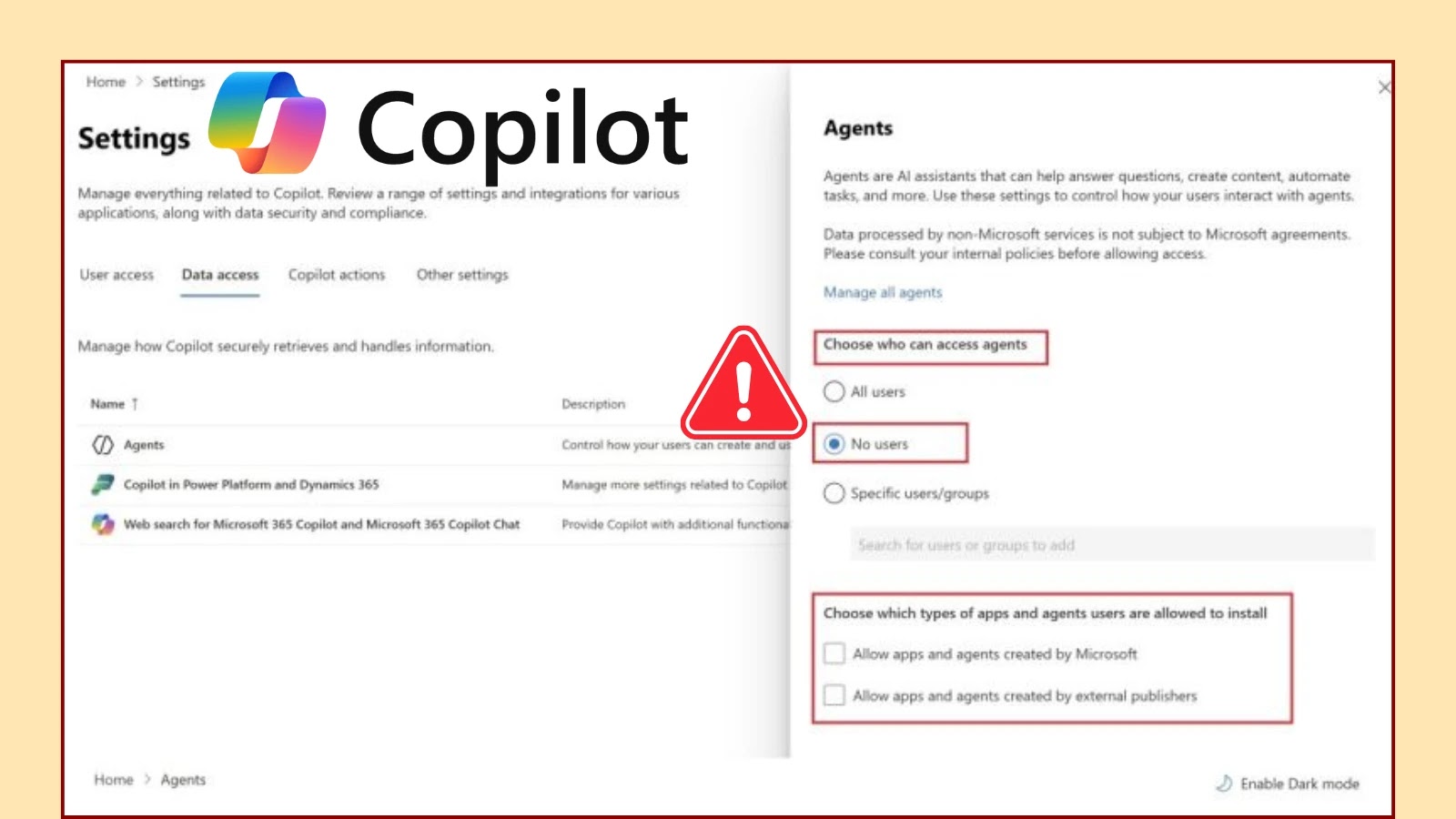
Microsoft Copilot Agent Policy Flaw Exposes AI Agents to Unauthorized Access
In May 2025, Microsoft introduced 107 Copilot Agents across Microsoft 365 tenants, aiming to enhance productivity through AI-driven assistance. However, security experts have identified a […]
Critical Vulnerabilities in Tableau Server Allow Malicious File Uploads and Remote Code Execution
A series of critical security vulnerabilities have been identified in Tableau Server, potentially allowing attackers to upload and execute malicious files, leading to full system […]
NIST Releases Ascon-Based Lightweight Cryptography Standard to Secure IoT Devices
In August 2025, the National Institute of Standards and Technology (NIST) unveiled Special Publication 800-232, introducing the Ascon family of algorithms as the new standard […]
Critical Vulnerabilities in Tableau Server Allow Malicious File Uploads and Remote Code Execution
Salesforce’s Tableau Server, a widely utilized data visualization tool, has been found to contain multiple critical security vulnerabilities that could allow attackers to upload and […]
Comparing EDR and MDR: Choosing the Right Cybersecurity Solution for Your Organization
In today’s rapidly evolving digital landscape, organizations face increasingly sophisticated cyber threats that necessitate robust security measures. Two prominent solutions have emerged to address these […]