Article Title: Fortinet Releases Critical Patch for FortiOS SSO Vulnerability Amid Active Exploitation Fortinet has issued critical security updates to address a severe vulnerability in […]
Category: Cybersecurity News
Stay informed about the ever-evolving world of digital threats and defenses with our Cyber Security News category. Here, you’ll find the latest breaking news, in-depth analysis, and expert insights on everything related to cybersecurity. From data breaches and ransomware attacks to emerging threats and innovative security solutions, we cover the critical issues impacting individuals, businesses, and governments worldwide. Keep up-to-date on the latest vulnerabilities, best practices, and trends shaping the future of online security.
Pakistan-Linked Cyber Espionage Targets Indian Government with Sophisticated Phishing Campaigns
Pakistan-Linked Cyber Espionage Campaigns Target Indian Government Entities In a series of sophisticated cyber espionage campaigns, threat actors linked to Pakistan have intensified their efforts […]
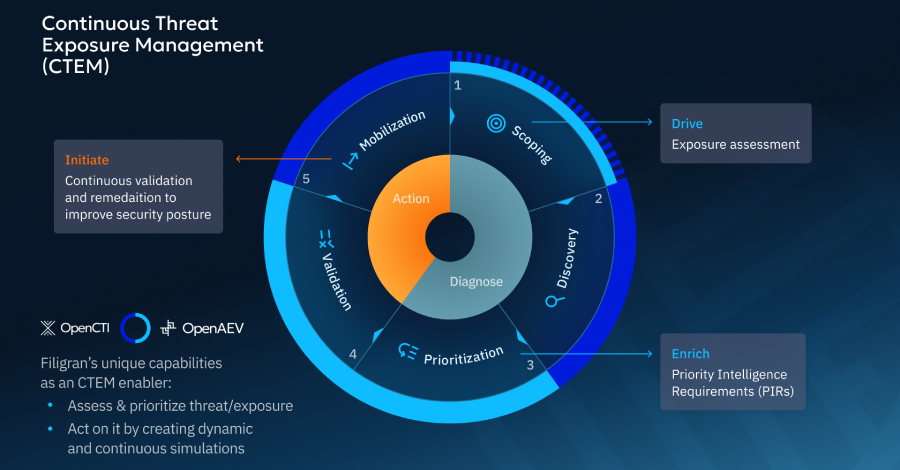
Continuous Threat Exposure Management Enhances Cybersecurity Strategy
Mastering Cybersecurity: Implementing Continuous Threat Exposure Management In the rapidly evolving landscape of cybersecurity, organizations are moving beyond isolated assessments of threats and vulnerabilities. The […]
Grist-Core’s Cellbreak Vulnerability Allows Remote Code Execution via Spreadsheet Formulas; Update Urged
Critical Grist-Core Vulnerability Exposes Systems to Remote Code Execution via Spreadsheet Formulas A significant security flaw has been identified in Grist-Core, an open-source, self-hosted relational […]
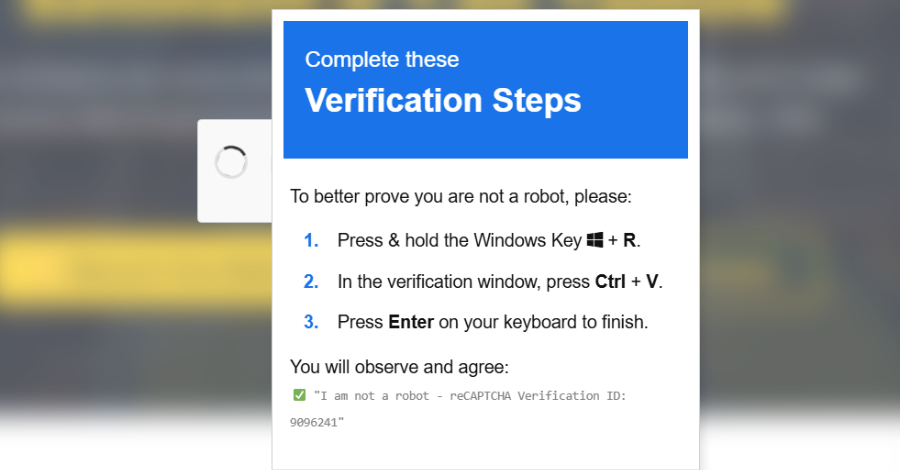
Cybercriminals Exploit Fake CAPTCHAs and Microsoft Scripts in Advanced ClickFix Attacks
Cybercriminals Enhance ClickFix Attacks with Fake CAPTCHAs and Trusted Web Services Cybersecurity experts have recently uncovered a sophisticated campaign that leverages the ClickFix social engineering […]
China-Linked APTs Exploit PeckBirdy JavaScript Framework in Advanced Cyber Attacks Across Asia
China-Linked Hackers Exploit PeckBirdy JavaScript Framework in Targeted Cyber Attacks Cybersecurity researchers have uncovered a sophisticated JavaScript-based command-and-control (C2) framework, dubbed PeckBirdy, actively utilized by […]
Pakistani APT Groups Launch Gopher Strike Cyber Assault on Indian Government with Sophisticated Tactics
Gopher Strike: Unveiling the Sophisticated Cyber Assault on Indian Government by Pakistani APT Groups In a significant escalation of cyber warfare, advanced persistent threat (APT) […]
Critical Flaw in Python PLY Library Allows Remote Code Execution; Urgent Mitigation Advised
Critical Vulnerability in Python PLY Library Enables Remote Code Execution A significant security flaw has been discovered in version 3.11 of the Python Lex-Yacc (PLY) […]
Caminho Loader Emerges: Malware-as-a-Service Uses Steganography to Evade Detection
Caminho Loader: A Stealthy Malware Delivery Service Leveraging Steganography In the ever-evolving landscape of cyber threats, a new and sophisticated malware delivery service known as […]
Critical Vulnerability in WD Discovery App Allows Code Execution; Users Urged to Update to Version 5.3
Critical Vulnerability in WD Discovery Desktop App Allows Arbitrary Code Execution A significant security flaw has been identified in Western Digital’s WD Discovery desktop application […]