Google Messages Enhances User Experience with Integrated Photo Picker Google Messages has recently integrated Android’s new embedded photo picker, significantly enhancing the user experience by […]
Archives
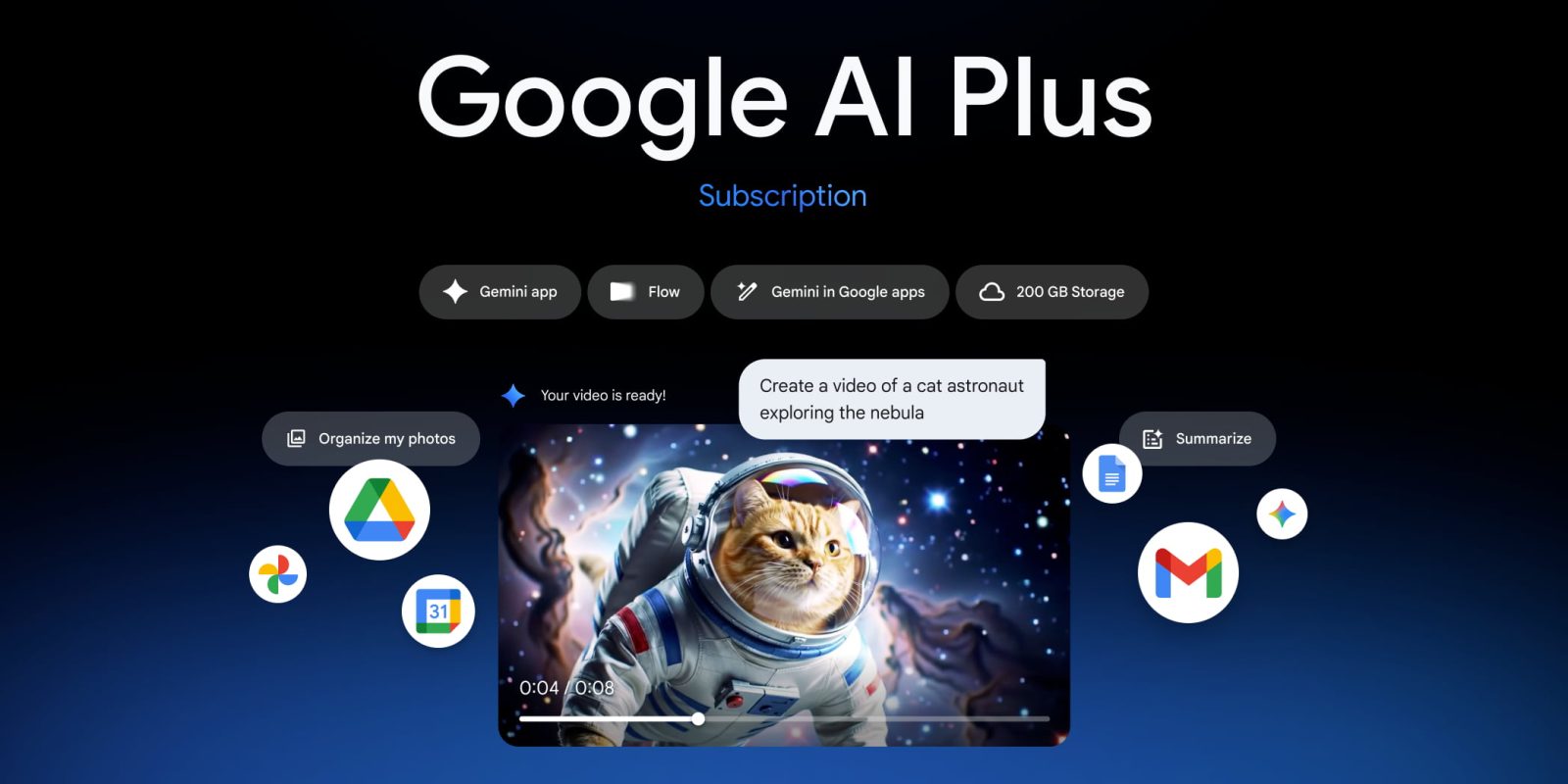
Google Expands AI Plus to US and 35 Countries, Offering Advanced Features and Storage for $7.99/Month
Google AI Plus Launches in the US: Enhanced AI Features and Storage at $7.99/Month Google has expanded its AI Plus subscription service to 35 additional […]
Google’s Gemini 3 Flash Unveils ‘Agentic Vision’ for Enhanced Image Analysis and Accuracy
Gemini 3 Flash Introduces ‘Agentic Vision’ for Enhanced Image Analysis Google’s Gemini 3 Flash model has unveiled a groundbreaking feature named ‘Agentic Vision,’ designed to […]
Samsung Launches $2,899 Galaxy Z TriFold in U.S. on January 30 with Dual Hinge Design
Samsung’s Galaxy Z TriFold Arrives in the U.S. on January 30 for $2,899 Samsung is set to launch its groundbreaking Galaxy Z TriFold smartphone in […]
Google’s Android Desktop Interface Leak Reveals Future Mobile-Desktop Integration
Android’s Desktop Interface Unveiled: A Glimpse into the Future of Mobile Computing In a recent development, Google’s ongoing efforts to transform Android into a versatile […]
iPhone 15 in 2026: A Cost-Effective Option Amid New Models Despite Outdated Features
Is the iPhone 15 Still a Smart Purchase in 2026? Released in late 2023, the iPhone 15 was Apple’s flagship device, boasting cutting-edge technology and […]
WhatsApp Boosts Security with Strict Account Settings and Rust Integration to Combat Cyber Threats
WhatsApp has unveiled two significant security enhancements aimed at bolstering user privacy and safeguarding against sophisticated cyber threats. These updates introduce the Strict Account Settings […]
Apple Launches watchOS 26.3 Public Beta 3 with Enhanced AirTag Integration
Apple Releases watchOS 26.3 Public Beta 3 with Enhanced AirTag Support Apple has recently unveiled the third public beta of watchOS 26.3, marking a significant […]
Apple Unveils visionOS 26.3 Public Beta 3 for Vision Pro with Stability and Bug Fixes
Apple Releases visionOS 26.3 Public Beta 3 for Vision Pro Users Apple has recently unveiled the third public beta of visionOS 26.3, designated as build […]
Tech Leaders, Including Tim Cook, Attend White House Screening of Melania Documentary
Tim Cook Joins Tech Leaders at White House Premiere of ‘Melania’ Documentary Apple CEO Tim Cook recently attended a private screening at the White House […]