1. Executive Summary This report analyzes 124 distinct cyber incidents recorded within a 24-hour window, primarily on January 8, 2026. The threat landscape is characterized […]
Archives
[January-07-2026] Daily Cybersecurity Threat Report
This report summarizes a series of cyber incidents detected on January 7, 2026. The data indicates a global wave of cyber activity ranging from critical […]
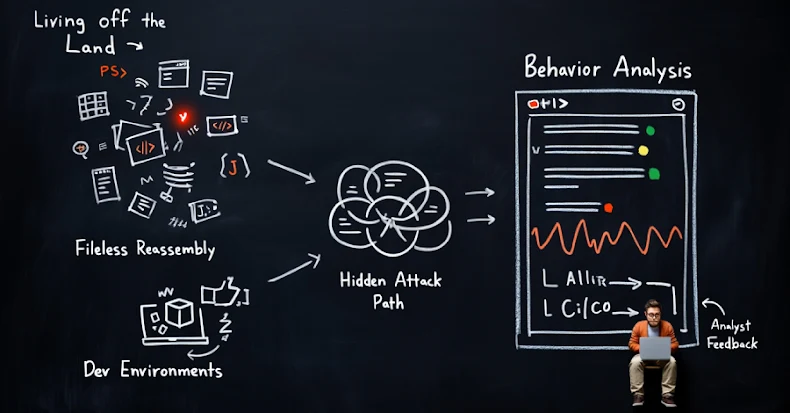
AI-Powered Zero Trust Security Enhances Detection of Stealthy Fileless Cyber Threats
Unveiling AI-Powered Zero Trust: Detecting Stealthy Cyber Threats Without Traditional Indicators In the ever-evolving landscape of cybersecurity, traditional defense mechanisms are increasingly being outmaneuvered by […]
Veeam Issues Critical Update for Remote Code Execution Vulnerabilities in Backup Software
Veeam Releases Critical Security Updates to Address Remote Code Execution Vulnerabilities Veeam, a leading provider of backup and replication solutions, has recently issued security updates […]
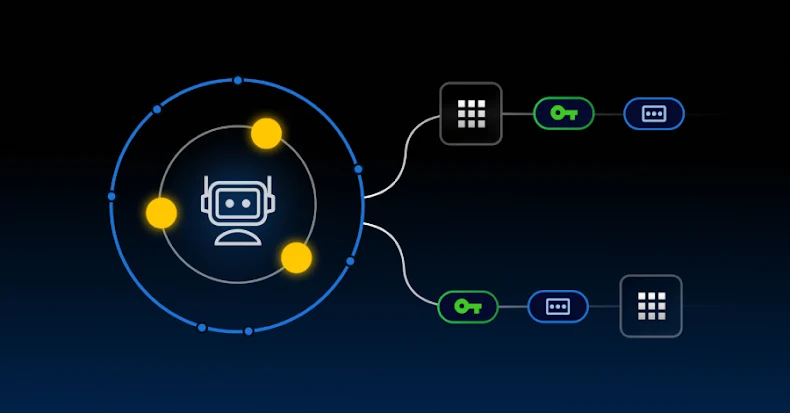
Zero-Trust Strategies Urged as Non-Human Identities Rise in Cybersecurity
Embracing Non-Human Employees: The Future of Cybersecurity As organizations increasingly integrate Artificial Intelligence (AI) and cloud automation into their operations, the presence of Non-Human Identities […]
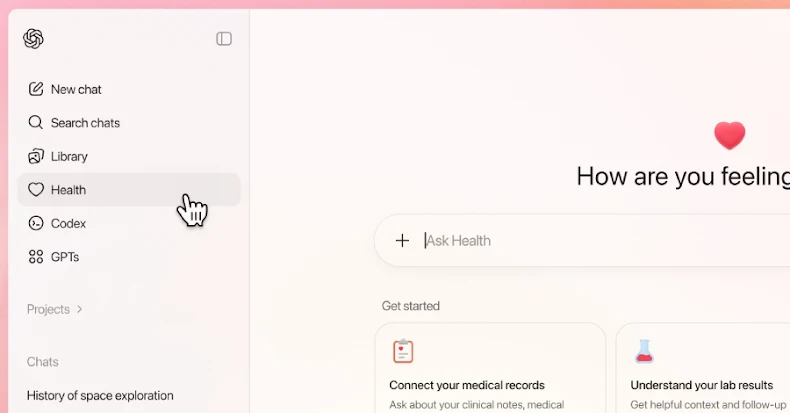
OpenAI Launches ChatGPT Health for Personalized Wellness Insights and Secure Medical Data Integration
OpenAI has unveiled ChatGPT Health, a specialized platform designed to assist users with health-related inquiries. This new feature allows individuals to securely connect their medical […]
Critical Flaw in n8n Allows Remote Code Execution; Update to Version 1.121.3 Immediately
Critical Security Flaw in n8n Poses Remote Code Execution Risk n8n, the open-source workflow automation platform, has identified a critical security vulnerability that could allow […]
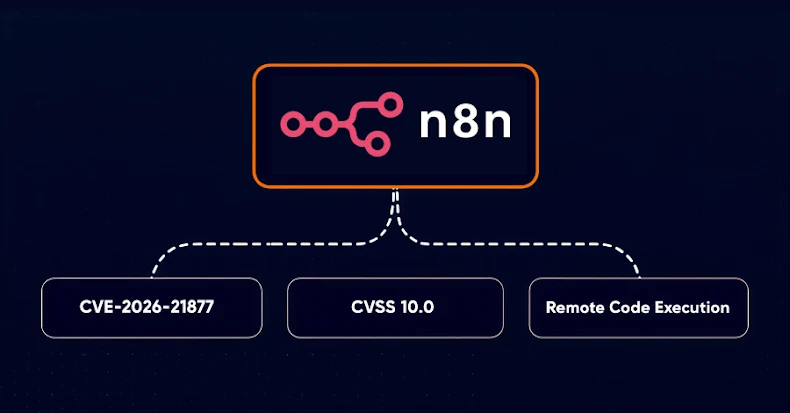
Critical n8n Vulnerability (CVE-2026-21858) Allows Full System Compromise; Users Urged to Update Immediately
Critical n8n Vulnerability (CVSS 10.0) Allows Unauthenticated Attackers to Take Full Control A critical security vulnerability has been identified in n8n, a widely-used open-source workflow […]
CISA Flags Critical Vulnerabilities in Microsoft Office and HPE OneView, Urges Immediate Patching
The U.S. Cybersecurity and Infrastructure Security Agency (CISA) has recently identified and added two significant security vulnerabilities affecting Microsoft Office and Hewlett Packard Enterprise (HPE) […]
Black Cat Cybercrime Group Uses SEO Poisoning to Spread Malware via Fake Software Sites
Black Cat Cybercrime Group Exploits SEO to Distribute Malware via Fake Software Downloads A sophisticated cybercrime group known as Black Cat has been identified as […]
![[January-08-2026] Daily Cybersecurity Threat Report](https://thedailytechfeed.com/wp-content/uploads/2025/04/s1.jpg)