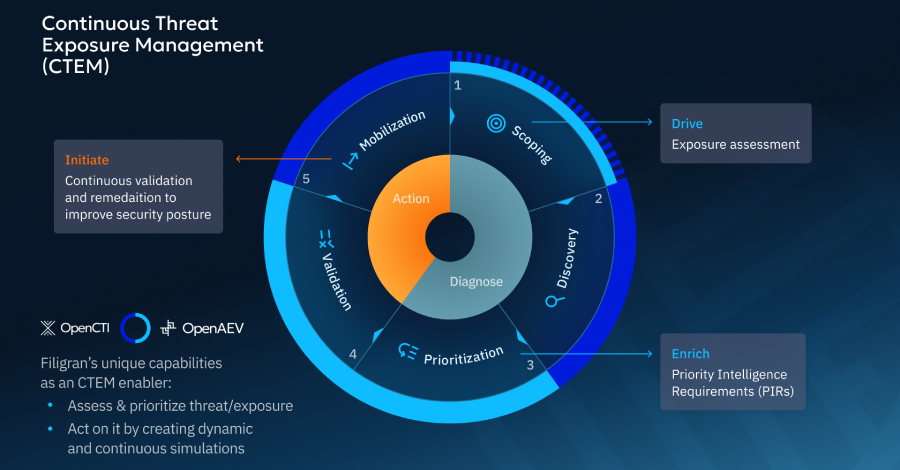
Mastering Cybersecurity: Implementing Continuous Threat Exposure Management In the rapidly evolving landscape of cybersecurity, organizations are moving beyond isolated assessments of threats and vulnerabilities. The […]
Archives
Grist-Core’s Cellbreak Vulnerability Allows Remote Code Execution via Spreadsheet Formulas; Update Urged
Critical Grist-Core Vulnerability Exposes Systems to Remote Code Execution via Spreadsheet Formulas A significant security flaw has been identified in Grist-Core, an open-source, self-hosted relational […]
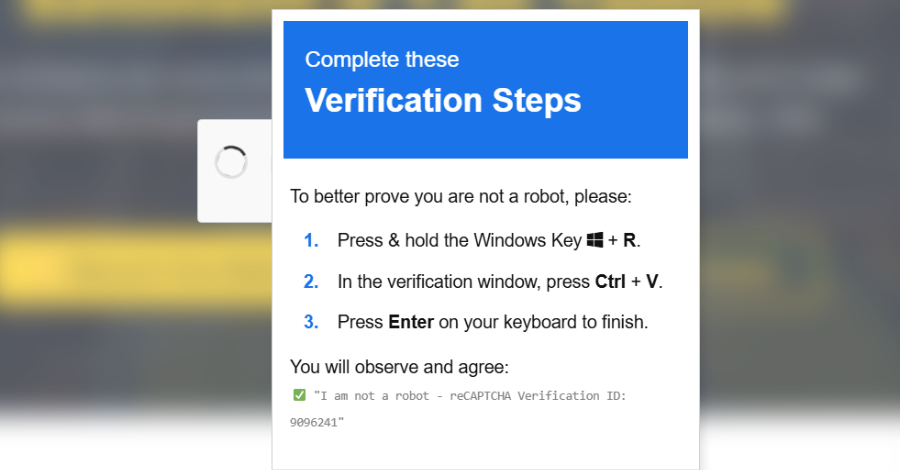
Cybercriminals Exploit Fake CAPTCHAs and Microsoft Scripts in Advanced ClickFix Attacks
Cybercriminals Enhance ClickFix Attacks with Fake CAPTCHAs and Trusted Web Services Cybersecurity experts have recently uncovered a sophisticated campaign that leverages the ClickFix social engineering […]
China-Linked APTs Exploit PeckBirdy JavaScript Framework in Advanced Cyber Attacks Across Asia
China-Linked Hackers Exploit PeckBirdy JavaScript Framework in Targeted Cyber Attacks Cybersecurity researchers have uncovered a sophisticated JavaScript-based command-and-control (C2) framework, dubbed PeckBirdy, actively utilized by […]
WhatsApp Launches Strict Account Settings to Boost User Security and Privacy
WhatsApp Introduces ‘Strict Account Settings’ to Enhance User Security In response to growing concerns over user privacy and security, WhatsApp has unveiled a new feature […]
TikTok Restructures US Operations with New Ownership to Address Data Privacy Concerns
Understanding the New Ownership Structure of TikTok in the U.S. In response to mounting concerns over data privacy and foreign influence, ByteDance, the Chinese parent […]
TikTok Works to Resolve U.S. Service Outage Amid Data Center Issues and Speculation
TikTok’s Ongoing Efforts to Restore U.S. Services Amid Infrastructure Challenges TikTok is actively working to restore its U.S. services following a significant data center outage […]
TikTok and Snap Settle Addiction Lawsuit; Meta and YouTube Head to Trial
TikTok and Snap Settle Social Media Addiction Lawsuit as Meta and YouTube Prepare for Trial In a significant development within the tech industry, TikTok has […]
Waymo Robotaxi Fares Near Parity with Uber and Lyft, Signaling Shift in Ride-Hailing Market
Waymo’s Robotaxi Rides Approach Parity with Uber and Lyft Pricing In the evolving landscape of urban transportation, the cost disparity between autonomous and traditional ride-hailing […]
Phia Secures $35M to Revolutionize Online Shopping with AI Innovations
Phia’s $35M Boost: Revolutionizing Online Shopping with AI In the rapidly evolving landscape of e-commerce, Phia, an innovative startup co-founded by Phoebe Gates and Sophia […]