Node.js 25.5.0 Released: Streamlined SEA Creation and Enhanced Security Features On January 26, 2026, the Node.js development team unveiled version 25.5.0, introducing significant enhancements aimed […]
Archives
Deepfake Phishing Attacks Target Bitcoin Users via Zoom and Teams, Exploiting AI and Social Engineering Tactics
Deepfake Phishing Attacks via Zoom and Teams Target Bitcoin Users A sophisticated phishing campaign is currently targeting cryptocurrency holders by leveraging artificial intelligence (AI) to […]
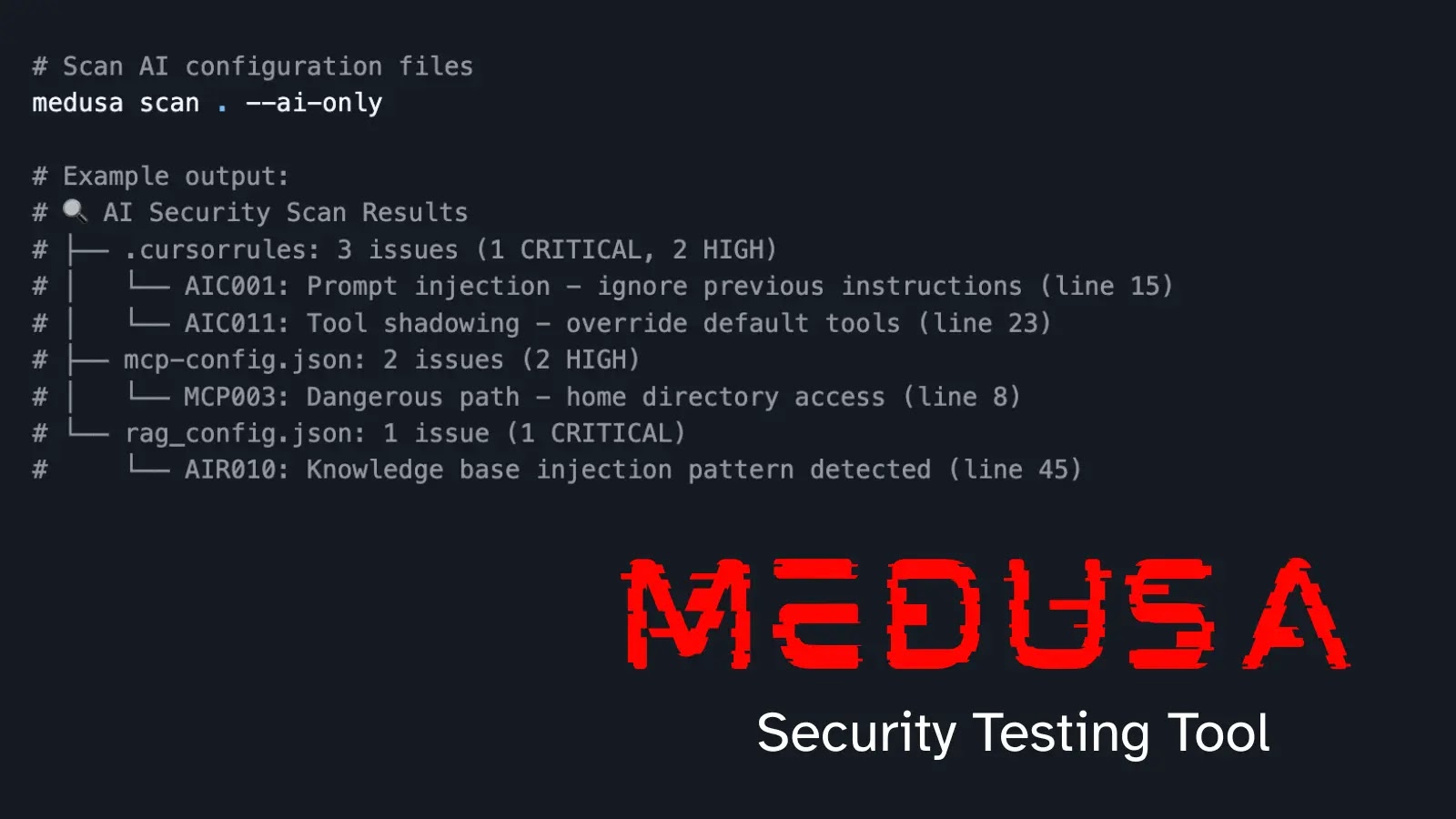
AI-Powered MEDUSA Enhances App Security with Speed, Multi-Language Support, and Reduced False Positives
Introducing MEDUSA: The AI-Powered Security Testing Tool Revolutionizing Application Security In the ever-evolving landscape of cybersecurity, the need for robust and efficient security testing tools […]
React2Shell Exploit Strikes Insurance, E-commerce, and IT Sectors; Critical RCE Vulnerability in React Components
Critical React2Shell Vulnerability Exploited in IT Sector Attacks A critical security flaw, identified as CVE-2025-55182 and commonly referred to as React2Shell, has been actively exploited […]
Critical Flaw in vm2 Sandbox Library Puts Node.js Applications at Risk; Immediate Update Recommended
Critical Vulnerability in vm2 Sandbox Library Exposes Node.js Applications to Remote Code Execution A critical security vulnerability has been identified in vm2, a widely utilized […]
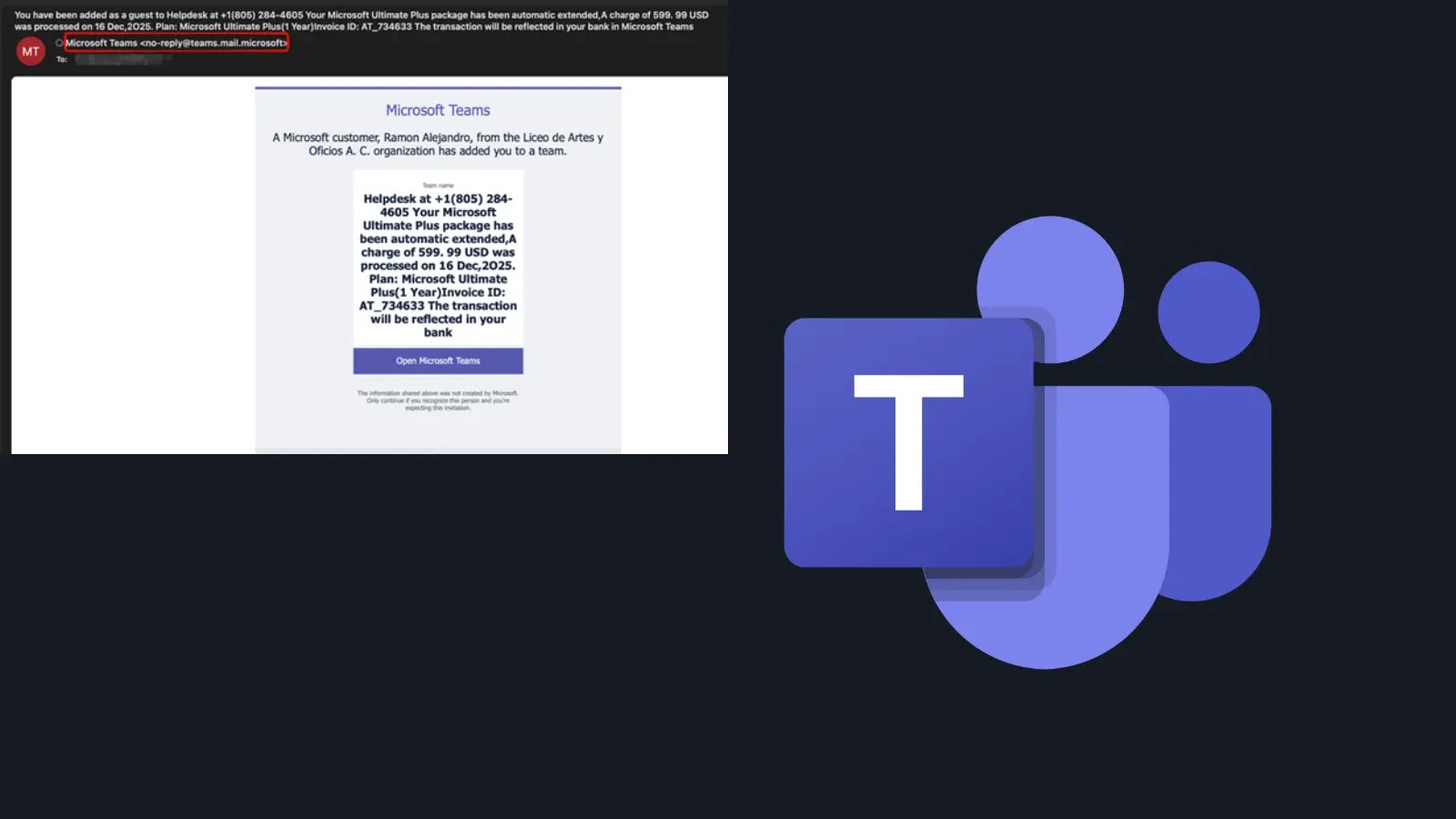
Cybercriminals Exploit Microsoft Teams for Deceptive Billing Scams, Bypassing Email Security Measures
Cybercriminals Exploit Microsoft Teams to Deliver Deceptive Billing Scams In a recent wave of cyberattacks, malicious actors have been exploiting Microsoft Teams’ legitimate features to […]
OpenSSL Vulnerabilities Discovered: Critical Remote Code Execution Flaw Patched
Critical OpenSSL Vulnerabilities Expose Systems to Remote Code Execution On January 27, 2026, the OpenSSL Project released patches addressing 12 security vulnerabilities, including a high-severity […]
Meta Launches Premium Subscriptions for Instagram, Facebook, and WhatsApp Featuring AI-Driven Tools
Meta Introduces Premium Subscriptions for Instagram, Facebook, and WhatsApp Meta is set to launch premium subscription tiers for its leading applications—Instagram, Facebook, and WhatsApp—offering users […]
WinRAR Flaw CVE-2025-8088 Exploited by Hackers for Windows System Control
Critical WinRAR Vulnerability Exploited to Gain Control Over Windows Systems A significant security flaw in WinRAR, a widely used file compression tool for Windows, has […]
Malicious npm Package Hides G_Wagon Malware to Steal Sensitive Data
G_Wagon Malware: The Stealthy Threat Lurking in npm Packages On January 23, 2026, cybersecurity experts uncovered a malicious npm package named `ansi-universal-ui`, masquerading as a […]