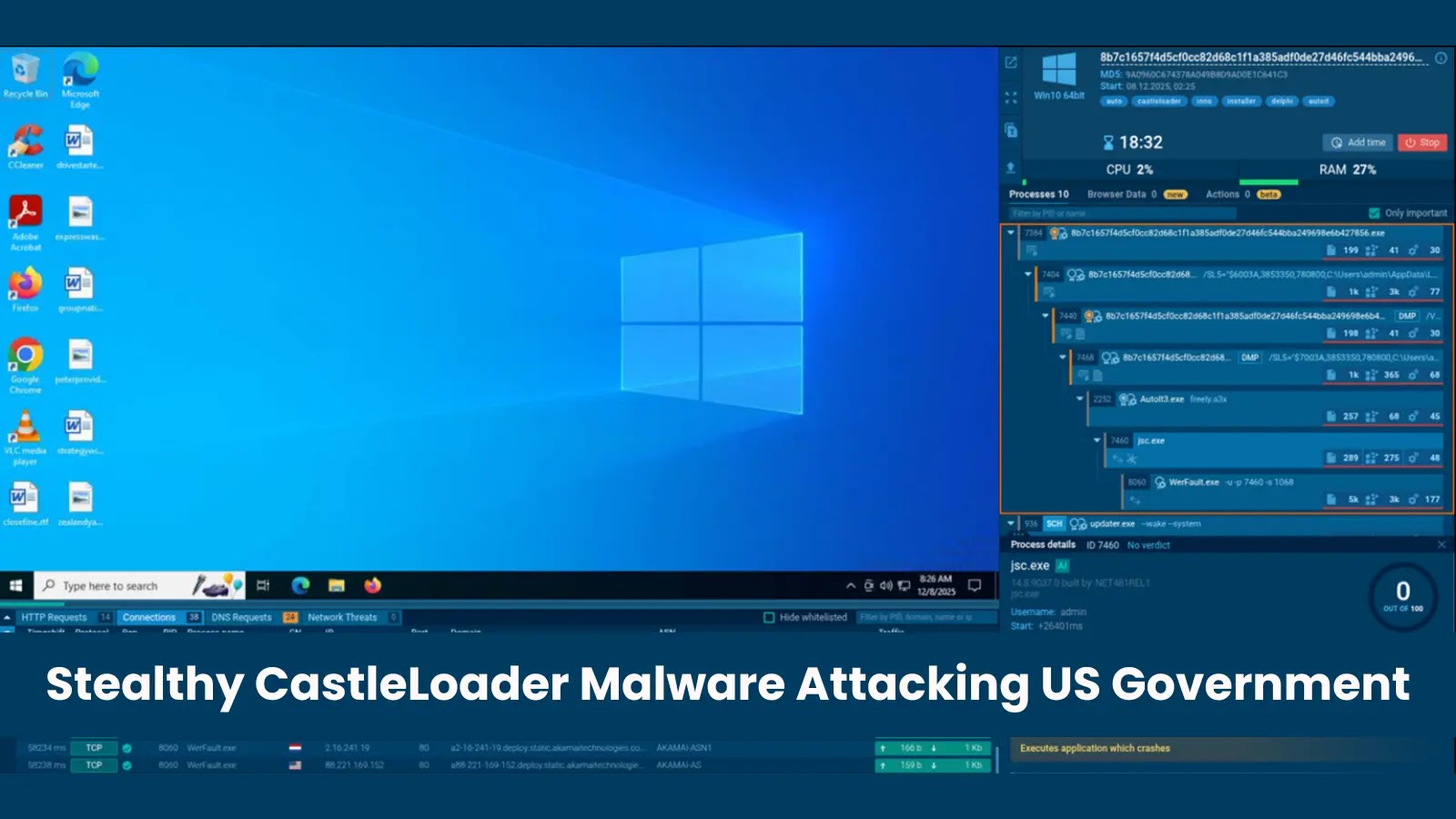
CastleLoader Malware: A Stealthy Threat to U.S. Government Agencies In early 2025, cybersecurity experts identified a sophisticated malware loader named CastleLoader, which has since emerged […]
Archives
Top 11 Single Sign-On Solutions for 2026: Boosting Security and User Experience
Top 11 Single Sign-On (SSO) Solutions for 2026: Enhancing Security and User Experience In today’s digital landscape, organizations are increasingly adopting Single Sign-On (SSO) solutions […]
AI-Driven Game-Theoretic Framework G-CTR Boosts Cybersecurity Attack and Defense Efficiency
Revolutionizing Cybersecurity: Game-Theoretic AI Enhances Attack and Defense Strategies In a significant advancement for cybersecurity, researchers from Alias Robotics and Johannes Kepler University Linz have […]
DragonForce Ransomware Analysis Reveals Decryption Tool for Windows and VMware Victims
Unveiling DragonForce Ransomware: A Comprehensive Analysis and Decryption Guide DragonForce has rapidly ascended in the cybercriminal hierarchy, evolving from obscure forum discussions to a full-fledged […]
One-Click Exploit in Microsoft Copilot Personal Revealed: Reprompt Vulnerability Exposed Sensitive Data
Reprompt Exploit: The One-Click Vulnerability in Microsoft Copilot Personal Exposing Sensitive Data A recently discovered vulnerability in Microsoft Copilot Personal, dubbed Reprompt, has raised significant […]
Critical DoS Vulnerability Found in Palo Alto Firewalls; Urgent Patch Required
Critical DoS Vulnerability in Palo Alto Networks Firewalls: Immediate Action Required Palo Alto Networks has recently addressed a critical denial-of-service (DoS) vulnerability, identified as CVE-2026-0227, […]
Top 12 OSINT Tools Enhancing Penetration Testing in 2026
Top 12 Open Source Intelligence (OSINT) Tools for Effective Penetration Testing in 2026 In the realm of cybersecurity, Open Source Intelligence (OSINT) tools have become […]
North Korean Hackers Target Developers with Sophisticated ‘Contagious Interview’ Malware Campaign
North Korean Hackers Exploit Code Abuse Tactics in ‘Contagious Interview’ Campaign North Korean cyber operatives have initiated a sophisticated social engineering campaign, dubbed Contagious Interview, […]
Critical Microsoft SQL Server Vulnerability CVE-2026-20803 Allows Remote Privilege Escalation
Critical Vulnerability in Microsoft SQL Server Allows Remote Privilege Escalation On January 13, 2026, Microsoft released security updates to address a significant elevation of privilege […]
AI-Powered Ransomware: Large Language Models Transform Cybercrime Efforts Globally
AI-Powered Ransomware: How Large Language Models Are Revolutionizing Cyber Attacks The advent of Large Language Models (LLMs) has significantly transformed the landscape of ransomware operations. […]