Coordinated Malicious Chrome Extensions Compromise Enterprise HR and ERP Systems A sophisticated cyber threat has emerged, involving five malicious Chrome extensions designed to infiltrate and […]
Archives
CIRO Data Breach Exposes Info of 750,000 Canadian Investors in Phishing Attack
CIRO Data Breach Exposes Sensitive Information of 750,000 Canadian Investors In a significant cybersecurity incident, the Canadian Investment Regulatory Organization (CIRO) has confirmed that approximately […]
Ukrainian and German Agencies Break Up Major Russian Ransomware Group, Issue Interpol Warrant
Ukrainian and German Authorities Dismantle Russian Ransomware Syndicate In a significant blow to international cybercrime, Ukrainian and German law enforcement agencies have successfully disrupted a […]
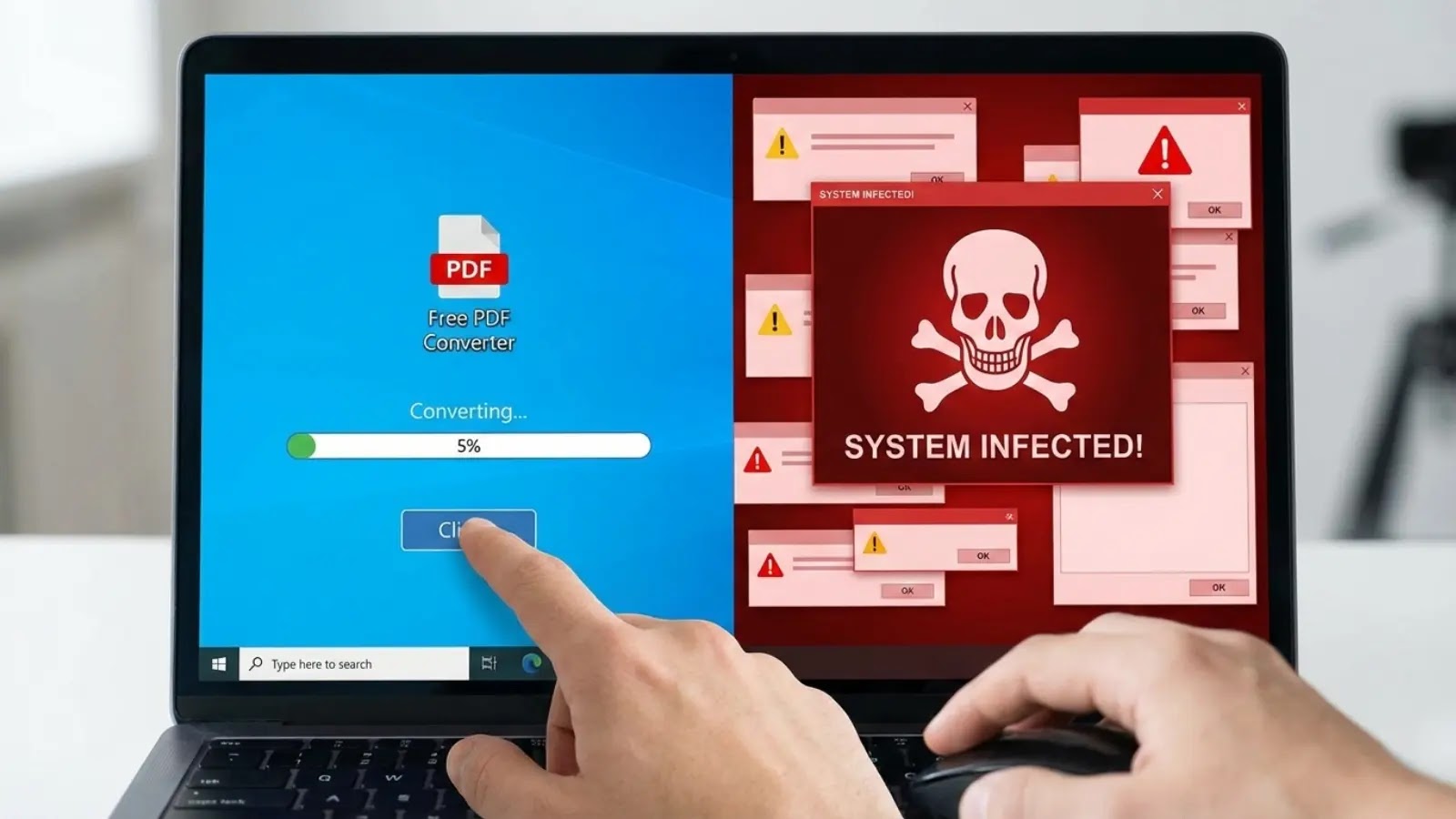
Free Converter Apps Hide Trojans, Compromise System Security with RATs
Beware: Free Converter Apps May Infect Your System in Seconds In the digital age, the convenience of free file converter applications is undeniable. However, recent […]
Cloudflare Fixes Zero-Day Flaw Allowing WAF Bypass via ACME Protocol Exploit
Cloudflare, a leading provider of web security and performance services, recently addressed a critical zero-day vulnerability that allowed attackers to bypass its Web Application Firewall […]
Cybercriminals Exploit Google Ads to Spread EndRAT Malware in Operation Poseidon
Operation Poseidon: Cybercriminals Exploit Google Ads to Deploy EndRAT Malware A sophisticated cyberattack campaign, dubbed Operation Poseidon, has recently surfaced, leveraging Google’s advertising infrastructure to […]
Cybercriminals Exploit VS Code Extensions to Deploy Sophisticated Multistage Malware
Cybercriminals Exploit Visual Studio Code Extensions to Deploy Multistage Malware In a concerning development, cybercriminals are increasingly targeting developers by exploiting Visual Studio Code (VS […]
Cybercriminals Use Fake VeraCrypt Installers to Deploy Remcos RAT, Target South Korean Users
Cybercriminals Disguise Remcos RAT as VeraCrypt Installers to Steal User Credentials A sophisticated cyberattack campaign has been identified, primarily targeting South Korean users by distributing […]
Pulsar RAT: New Stealth Malware Poses Global Threat to Windows Systems
Pulsar RAT: The Stealthy Malware Redefining Remote Access Threats In the ever-evolving landscape of cyber threats, a new and sophisticated malware known as Pulsar RAT […]
Kerberos Vulnerability Exploits DNS CNAME, Poses Security Threat to Windows Environments
Critical Kerberos Relay Attack Exploits DNS CNAME to Bypass Security Measures A significant vulnerability has been identified in Windows Kerberos authentication, expanding the potential for […]