Revolutionizing MSSP Operations: Leveraging AI to Enhance Margins with Reduced Workforce In the rapidly evolving cybersecurity landscape of 2026, Managed Security Service Providers (MSSPs) are […]
Archives
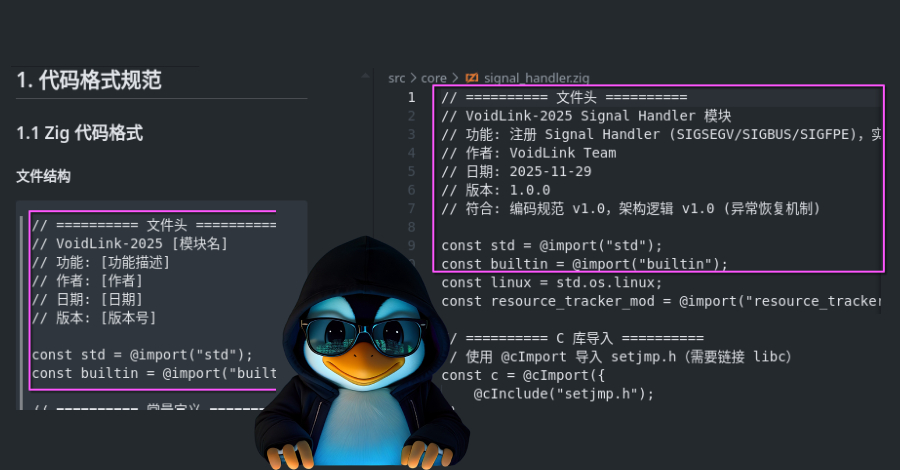
AI-Powered VoidLink Malware Framework Poses New Threat to Linux Systems
AI-Generated VoidLink Malware Framework Emerges as a New Threat to Linux Systems In a groundbreaking development within the cybersecurity landscape, researchers have uncovered VoidLink, a […]
North Korean Group PurpleBravo Exploits Job Interviews in Global Cyber Espionage Campaign
In a sophisticated cyber espionage campaign, North Korean threat actors, identified as PurpleBravo, have targeted over 3,000 IP addresses across multiple sectors and regions. This […]
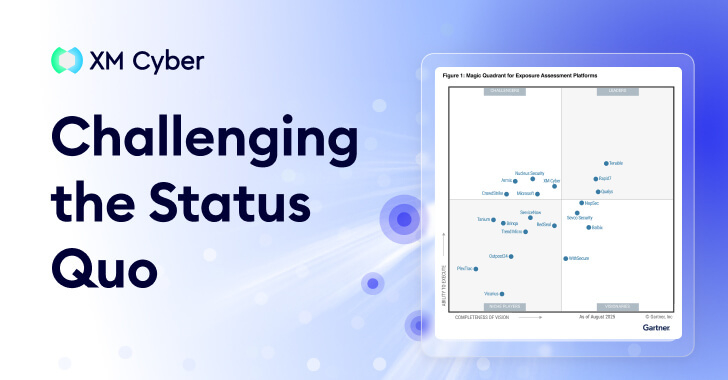
Exposure Assessment Platforms Transform Cybersecurity by Prioritizing Real Risks
Revolutionizing Cybersecurity: The Rise of Exposure Assessment Platforms In the ever-evolving landscape of cybersecurity, traditional vulnerability management (VM) approaches are increasingly proving inadequate. The sheer […]
Cisco Issues Critical Patches for Active Zero-Day Vulnerability in Unified Communications, Webex Platforms
Cisco Addresses Critical Zero-Day Vulnerability in Unified Communications and Webex Platforms Cisco has recently released critical patches to address a significant security vulnerability, identified as […]
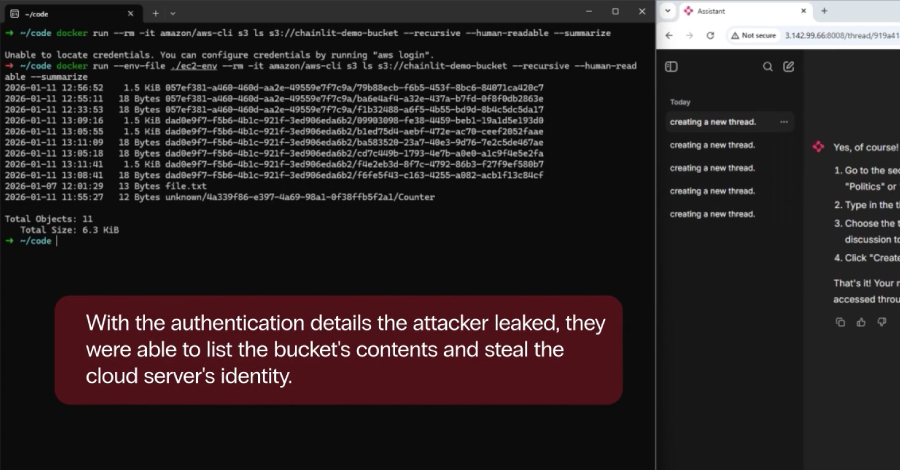
Critical Vulnerabilities in Chainlit AI Framework Enable Data Breaches; Update Urgently Needed
Critical Vulnerabilities in Chainlit AI Framework Expose Sensitive Data to Potential Theft Recent security assessments have identified significant vulnerabilities within Chainlit, a widely utilized open-source […]
Critical Vulnerability in binary-parser Library Allows Remote Code Execution in Node.js Apps
Critical Vulnerability in binary-parser Library Exposes Node.js Applications to Remote Code Execution A significant security flaw has been identified in the widely-used JavaScript library, binary-parser, […]
Automated Attacks Exploit FortiCloud SSO Weakness, Targeting FortiGate Devices with Critical Security Risks
Automated Attacks Target FortiGate Devices via FortiCloud SSO Vulnerability Cybersecurity firm Arctic Wolf has identified a new wave of automated attacks targeting Fortinet’s FortiGate devices. […]
Zipline Secures $600M for U.S. Drone Delivery Expansion, Targets Houston and Phoenix in 2026
Zipline’s $600 Million Boost: Pioneering the Future of Drone Delivery in the U.S. Zipline, a leader in autonomous drone delivery and logistics, has secured over […]
YouTube Unveils AI-Generated Likeness for Creators in Shorts to Boost Creative Expression
YouTube Empowers Creators with AI-Generated Likeness for Shorts In a groundbreaking move, YouTube is set to revolutionize content creation by enabling creators to produce Shorts […]