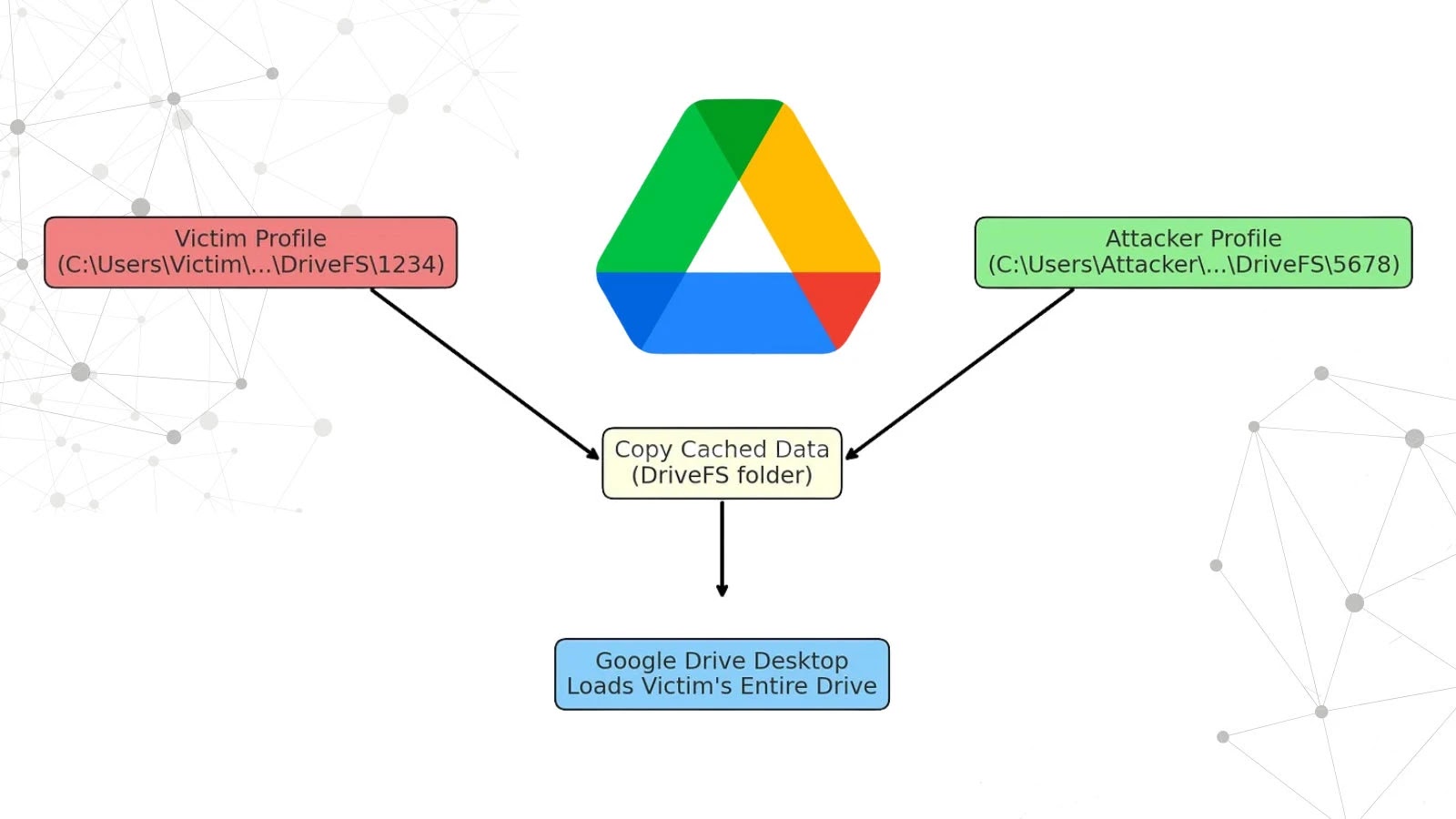
A significant security flaw has been identified in the Google Drive Desktop application for Windows, allowing users on shared computers to access each other’s Drive files without requiring authentication. This vulnerability arises from inadequate isolation of cached data within the application’s local caching system, known as DriveFS.
Understanding the Vulnerability
Google Drive Desktop caches synchronized files in a local directory called `DriveFS`. Due to improper isolation between user profiles on a Windows system, an attacker can access another user’s cached `DriveFS` folder, copy its contents, and replace their own `DriveFS` folder with the victim’s data. Upon restarting the application, Google Drive loads the victim’s entire drive, including My Drive and Shared Drives, as if it belonged to the attacker, without any re-authentication prompts.
Security Implications
This exploit directly contravenes fundamental security principles:
– Zero Trust: The application incorrectly trusts the copied cache without verifying the user identity.
– Encryption at Rest: Cached files are not individually encrypted for each user, allowing them to be reused across different accounts.
– Re-authentication: The application does not require a password or any form of re-login when a different user’s cache is loaded.
This vulnerability presents a classic insider threat scenario, particularly dangerous in environments with shared workstations like offices, universities, or co-working spaces. An employee or any user on a shared system can covertly copy another person’s Drive cache, gaining access to sensitive files such as contracts, financial records, HR documents, or proprietary source code.
Potential Consequences
The potential for data exfiltration, modification, or deletion is substantial, posing risks of privacy violations, compliance failures under regulations like GDPR and HIPAA, and significant reputational damage. Insider threats are a known and costly problem, accounting for 22% of security breaches according to the 2024 Verizon DBIR and costing companies an average of $15.38 million annually, as reported by a 2022 Ponemon/IBM study.
Non-Compliance with Security Standards
The vulnerability places the Google Drive Desktop app out of alignment with major global security standards like NIST SP 800-53, ISO 27001, and SOC 2. These frameworks mandate strict data isolation, least privilege access, encryption of data at rest, and robust session management—all of which are compromised by this flaw.
Google’s Response
The researcher who discovered the issue reported it to Google’s vulnerability program but was told, This is not considered a security bug. This response is concerning, as the flaw represents a failure to adhere to Zero Trust principles and leaves users exposed to significant risks.
Recommendations for Users
Until Google addresses this issue, users and organizations are advised to take precautions:
– Avoid Shared Computers: Refrain from using Google Drive Desktop on shared or multi-user computers.
– Enforce Strict Permissions: Implement strict permissions on separate Windows user profiles.
– Use Dedicated Endpoints: Utilize the application only on dedicated and managed endpoints to minimize insider threat risks.
Ultimately, the responsibility for securing user data lies with the service provider. Users should remain vigilant and implement best practices to protect their sensitive information.