A critical zero-day vulnerability, identified as CVE-2025-31324, has been discovered in SAP NetWeaver systems, affecting over 400 devices worldwide. This flaw allows unauthenticated attackers to […]
Day: April 28, 2025
Cybersecurity Firm CEO Arrested for Allegedly Installing Malware on Hospital Computers
On April 14, 2025, Jeffrey Bowie, the Chief Executive Officer of Veritaco, a cybersecurity firm, was arrested on two counts of violating Oklahoma’s Computer Crimes […]
Enhancing Incident Response Through Digital Forensics: A Guide for Security Leaders
In today’s rapidly evolving cyber threat landscape, the integration of digital forensics into incident response strategies has become imperative for organizations aiming to bolster their […]
Navigating Cybersecurity Frameworks: A Comprehensive Guide for CISOs
In today’s digital era, the role of the Chief Information Security Officer (CISO) has become increasingly vital. Organizations are confronted with a rapidly evolving threat […]
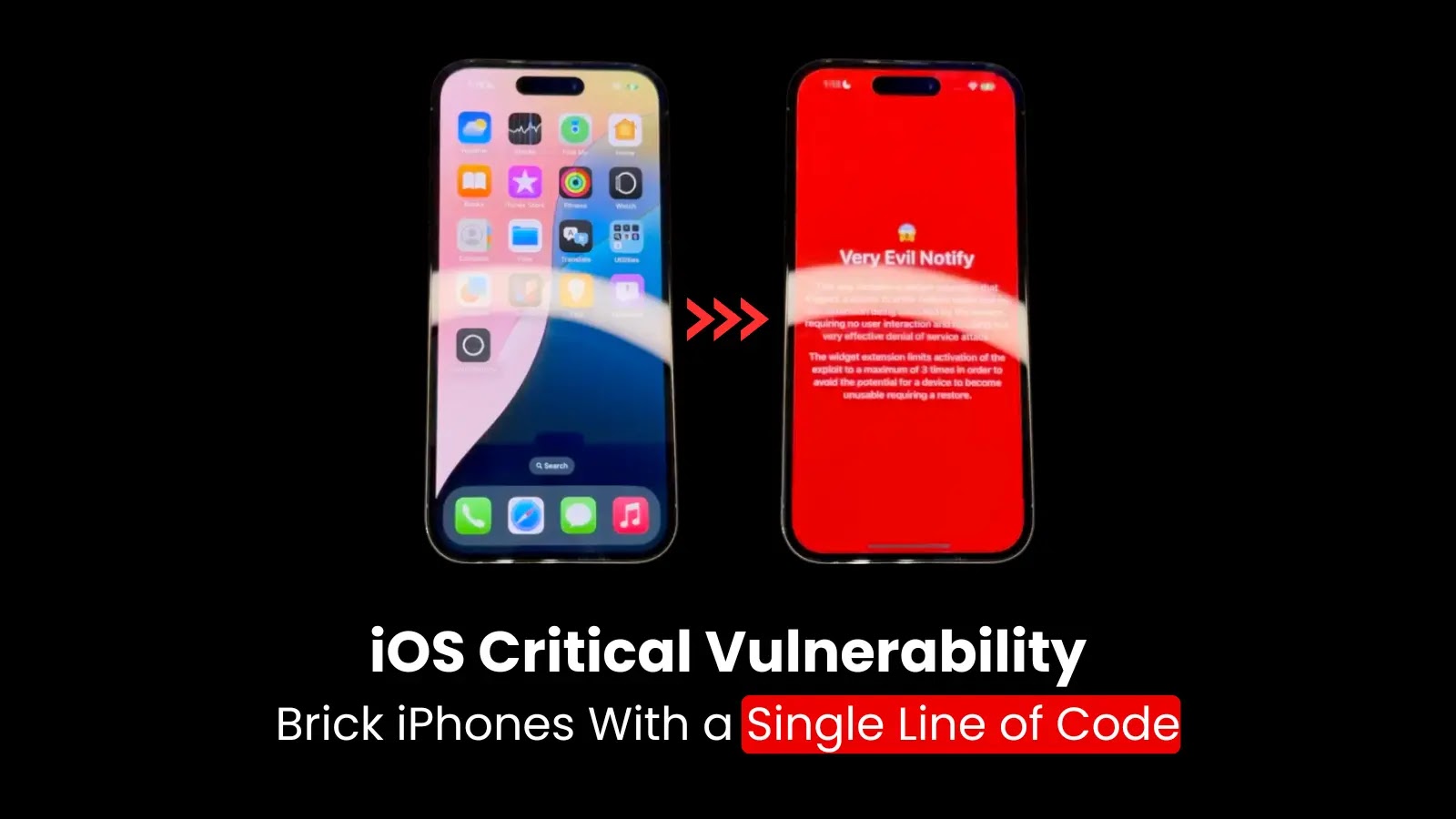
Critical iOS Vulnerability Allows Malicious Apps to Brick iPhones with a Single Line of Code
A recently discovered critical vulnerability in Apple’s iOS operating system, identified as CVE-2025-24091, enables malicious applications to render iPhones inoperable using just a single line […]
Critical IXON VPN Vulnerabilities Expose Windows and Linux Systems to Potential Attacks
Recent security evaluations have identified three critical vulnerabilities within the IXON VPN client, posing significant risks to both Windows and Linux systems. These vulnerabilities, designated […]
Securing IoT Devices: A Comprehensive Guide for CISOs
The Internet of Things (IoT) has revolutionized organizational operations, offering unprecedented efficiencies and insights across various industries. From healthcare to manufacturing, billions of connected devices […]
Unveiling Fog Ransomware’s Arsenal: A Deep Dive into Active Directory Exploitation Tools
In December 2024, cybersecurity researchers uncovered an open directory linked to the Fog ransomware group, providing an unprecedented glimpse into the tools and methodologies employed […]
Proactive Strategies for CISOs to Reduce Cyber Insurance Costs
In today’s digital landscape, cyber threats are escalating in both frequency and sophistication, leading to a significant rise in cyber insurance premiums. For Chief Information […]
Storm-1977 Exploits AzureChecker to Hijack Over 200 Containers for Crypto Mining in Educational Cloud Environments
A sophisticated cybercriminal group, identified as Storm-1977, has orchestrated a series of attacks targeting cloud infrastructures within the education sector. Utilizing a custom Command Line […]