OpenAI’s ChatGPT has recently introduced a significant enhancement by integrating advanced image generation capabilities into its platform. This feature, powered by the DALL·E 3 model, […]
Month: March 2025
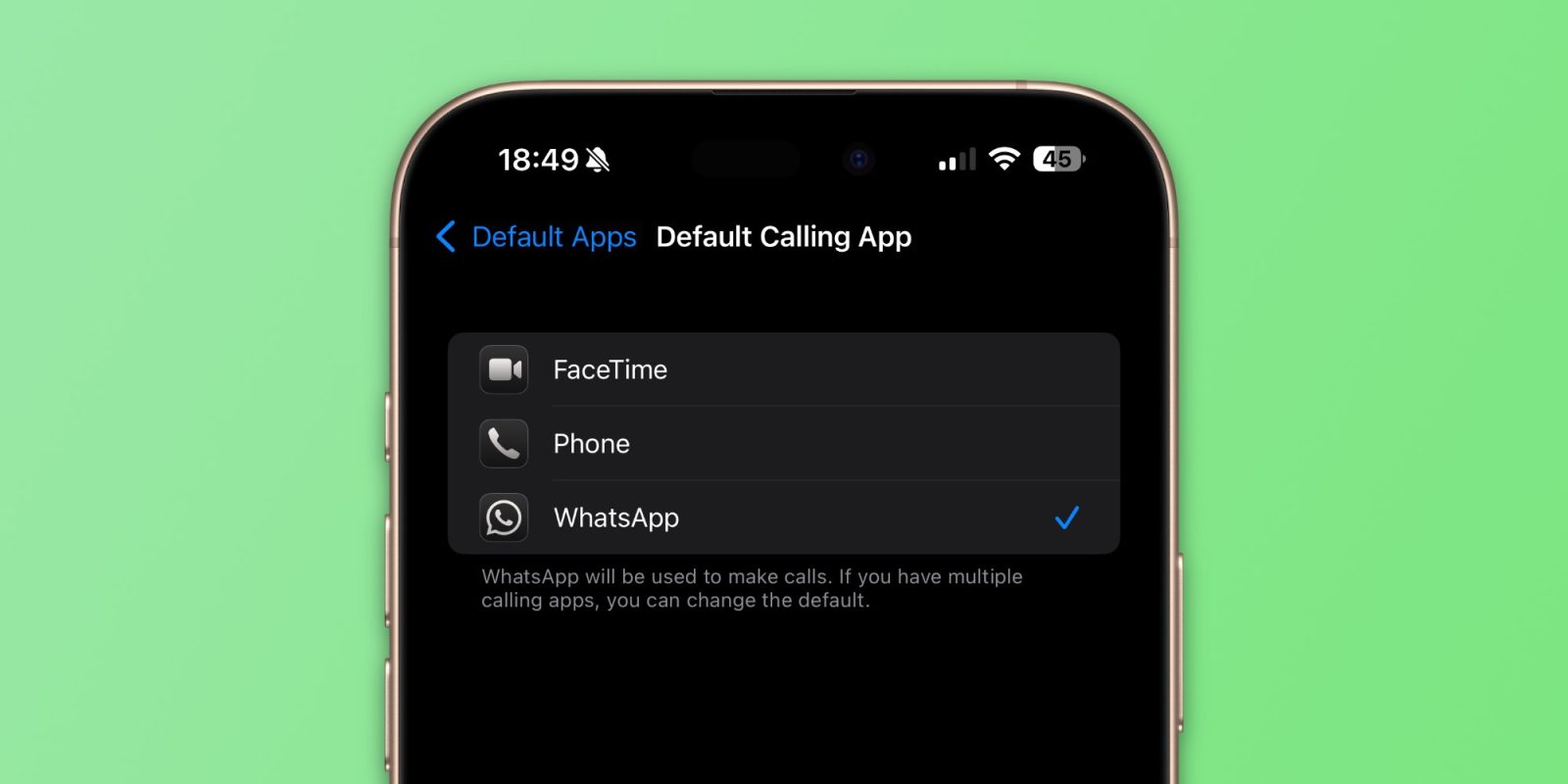
WhatsApp Now Available as Default Calling and Messaging App on iPhone
In a significant update with iOS 18.2, Apple has introduced the capability for iPhone users to designate third-party applications as their default for calls and […]
Instagram Introduces Fast-Forward Feature for Reels Videos
Instagram has unveiled a new feature that allows users to fast-forward through Reels videos, enhancing the viewing experience on its platform. This update enables users […]
EU to Impose Minimal Fines on Apple to Mitigate Tensions with U.S. Administration
The European Union (EU) is poised to levy fines on Apple for non-compliance with the Digital Markets Act (DMA), with an official announcement expected next […]
Apple’s Foldable iPhone: Bridging the Gap Between Smartphone and Tablet
Apple is poised to make a significant entry into the foldable device market with its anticipated iPhone Fold, slated for a fall 2026 release. This […]
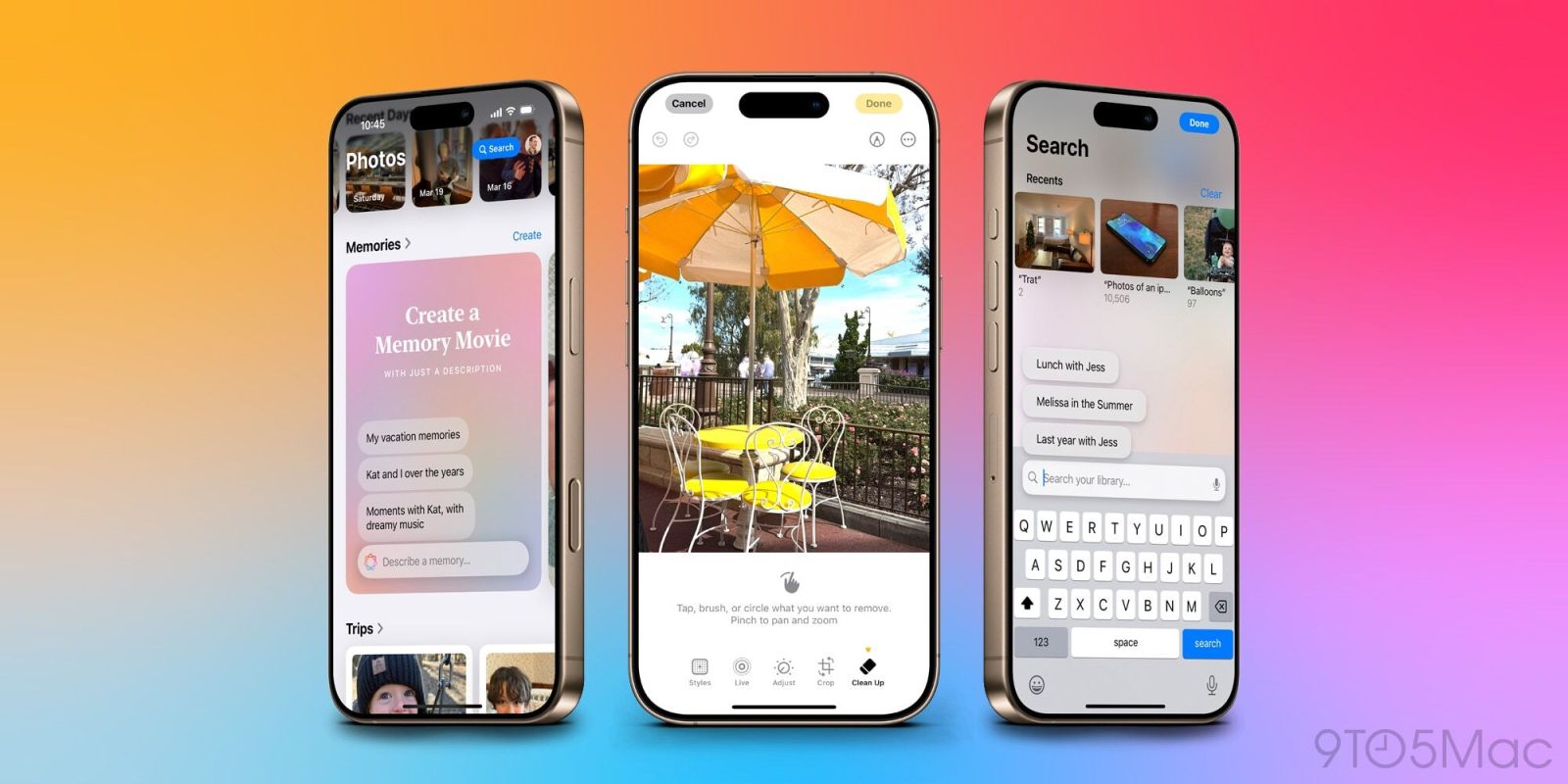
Apple’s Photos App: Unveiling Three AI Features Enhancing User Experience
In the rapidly evolving landscape of artificial intelligence (AI), Apple has seamlessly integrated advanced AI capabilities into its Photos app, significantly enhancing user experience. These […]
Emergence of OrpaCrab: A Sophisticated Linux Backdoor Targeting Operational Technology Systems
In January 2024, cybersecurity researchers identified a new Linux-based backdoor named “OrpaCrab,” posing a significant threat to operational technology (OT) systems, particularly those managing gas […]
Critical Remote Code Execution Vulnerability Discovered in Ingress-NGINX Controllers
A critical remote code execution (RCE) vulnerability, identified as CVE-2025-1974, has been discovered in Kubernetes Ingress-NGINX controllers. This flaw, uncovered by security researchers at Wiz, […]
Dark Web Marketplace B1ack’s Stash Releases 4 Million Stolen Credit Card Details
In a significant development within the cybercrime landscape, the dark web marketplace known as B1ack’s Stash has announced the release of 4 million stolen credit […]
Hackers Exploit COM Objects for Fileless Malware Lateral Movement
In March 2025, cybersecurity researchers uncovered a sophisticated attack technique where malicious actors exploit Component Object Model (COM) objects to execute fileless malware, facilitating lateral […]