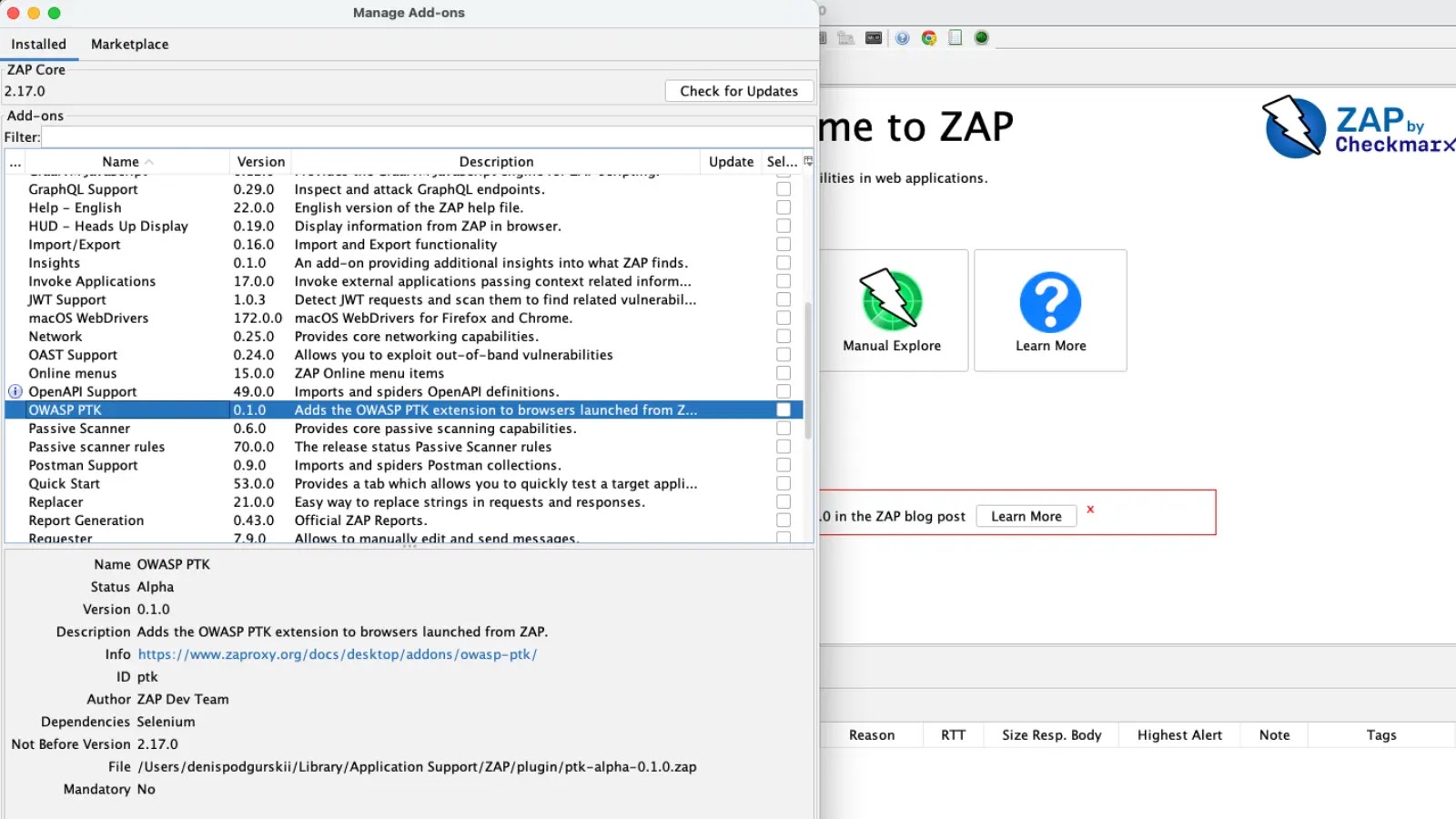
The Zed Attack Proxy (ZAP) team has unveiled the OWASP Penetration Testing Kit (PTK) add-on, version 0.2.0 alpha, marking a significant advancement in application security testing. This integration embeds the PTK browser extension directly into browsers launched via ZAP, streamlining the testing process by combining various security tools into a unified platform.
Seamless Integration for Enhanced Testing
The OWASP PTK add-on is accessible through the ZAP Marketplace. Once installed, it pre-configures the PTK extension in Chrome, Edge, and Firefox browsers initiated through ZAP. This setup eliminates the need for manual configurations, allowing security professionals to focus on testing rather than setup procedures.
Comprehensive Security Tools at Your Fingertips
The PTK add-on offers a suite of tools designed to address various aspects of application security:
– Dynamic Application Security Testing (DAST): This feature enables real-time scanning during regular browsing sessions. Users can initiate a scan, navigate through critical application flows such as form submissions and administrative pages, and then halt the scan to review the findings. This approach is particularly beneficial for Single Page Applications (SPAs) that rely heavily on user interactions. To maintain system stability, especially in production environments, it’s advisable to adjust the requests per second and concurrency settings appropriately. Limiting the scan scope to specific domains can also reduce extraneous data. The findings from DAST can be integrated with ZAP for further analysis and re-testing.
– Interactive Application Security Testing (IAST): IAST monitors the application’s runtime behavior by injecting agents during scans to detect issues beyond standard response analysis. Users can start monitoring, navigate through authenticated routes, and then assess any detected issues related to Document Object Model (DOM) mutations and client-side rendering. This feature is particularly useful for applications with UI states dependent on user interactions, providing immediate context for penetration testers within the browser workflow.
– Static Application Security Testing (SAST): SAST analyzes both inline and external scripts loaded in the production environment to identify potential vulnerabilities without requiring access to the source code repository. Users can run analyses on the current pages and correlate the findings with DAST and IAST results for validation. This is especially advantageous for assessing third-party scripts in SPAs.
– Software Composition Analysis (SCA): SCA identifies risks associated with dependencies by reviewing the packages used within the application. It provides context on how these packages are loaded and their potential impact on security.
Additional Functionalities for In-Depth Analysis
Beyond the core testing tools, the PTK add-on includes several features to facilitate thorough security assessments:
– Request Builder: This tool allows for rapid iteration by enabling users to edit traffic from ZAP’s history, replay attacks, clone requests as cURL commands, or manipulate headers.
– JWT Tools: Users can decode JSON Web Tokens (JWTs), modify claims or algorithms, and test enforcement mechanisms such as expiration times or weak HMAC signatures. These tokens can then be replayed via ZAP to observe response differences.
– Cookie Tools: This feature enables editing, blocking, or exporting cookies to reproduce sessions, aiding in the assessment of session management vulnerabilities.
Optimized Workflow for Security Professionals
A recommended workflow utilizing the PTK add-on involves:
1. Initiating a ZAP-Proxied Browser Session: Launch a browser through ZAP to ensure all traffic is captured and managed effectively.
2. Performing DAST and IAST: Use the PTK tools to conduct dynamic and interactive testing during typical user interactions with the application.
3. Conducting SAST and SCA: Analyze static code and software components to identify potential vulnerabilities.
4. Validating JWTs and Cookies: Assess the security of session management and token-based authentication mechanisms.
This integrated approach leverages ZAP as the central proxy hub while utilizing PTK for targeted browser-based testing, enhancing coverage for modern web applications. It’s crucial to emphasize permission-based active scans and adopt conservative settings to minimize potential disruptions during testing.
A Milestone in Application Security Testing
The release of the OWASP PTK add-on, announced on January 19, 2026, signifies a significant milestone in the collaboration between ZAP and PTK. Developed with contributions from Denis Podgurskii, this integration offers penetration testers an efficient, context-aware solution for assessing authenticated and dynamic applications.
Stay Informed
For the latest updates in cybersecurity, follow us on Google News, LinkedIn, and X. If you have stories to share, feel free to contact us.