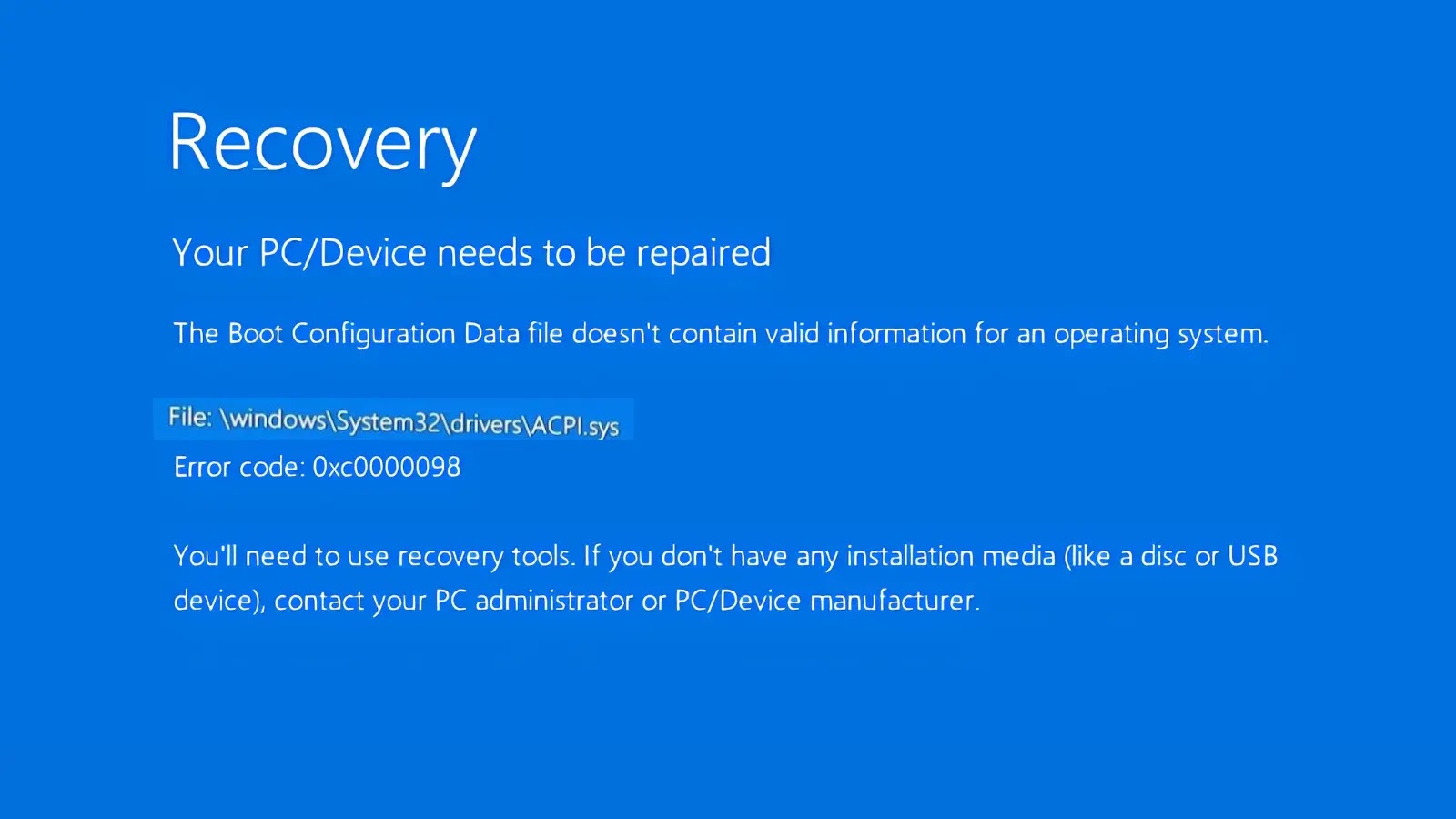
Microsoft’s recent Windows 11 security update, released on May 13, 2025, has led to significant boot failures in virtual machine environments, particularly affecting enterprise users. The cumulative update, identified as KB5058405, has triggered critical error code 0xc0000098 in the ACPI.sys file, rendering systems inoperable.
Impact on Virtual Environments
The issue predominantly affects Windows 11 versions 22H2 and 23H2 operating within virtualized settings, including Azure Virtual Machines, Azure Virtual Desktop, and on-premises systems hosted on Citrix or Hyper-V platforms. Microsoft has acknowledged that home users running Windows Home or Pro editions are unlikely to encounter this problem, as virtual machines are primarily utilized in IT environments.
Affected systems display the following recovery error message:
Your PC/Device needs to be repaired. The operating system couldn’t be loaded because a required file is missing or contains errors.
Enterprise IT administrators have reported widespread boot failures following the automatic installation of KB5058405, which was distributed as part of Microsoft’s May 2025 Patch Tuesday cycle. The issue has been observed on a small number of physical devices but is primarily impacting devices running in virtual environments, causing significant operational disruptions for organizations relying on virtualized Windows 11 deployments.
Root Cause Analysis
The root cause centers on the ACPI.sys file, a critical Windows system driver that enables the operating system to manage hardware resources and power states. ACPI.sys functions as the Windows Advanced Configuration and Power Interface driver, operating as a kernel-mode component essential for power management and device configuration on systems with ACPI BIOS.
When the update corrupts or conflicts with this driver, systems become unable to complete the boot process, displaying error code 0xc0000098. This specific error indicates that the operating system cannot load due to a missing or corrupted system file, effectively rendering affected virtual machines inaccessible until remediation steps are implemented.
Microsoft has noted that there are also reports of this same error occurring with a different file name, suggesting the issue may extend beyond ACPI.sys to other critical system components. The virtualization-specific nature of these failures points to potential compatibility issues between the security update and hypervisor environments.
Temporary Workarounds and Microsoft’s Response
Microsoft is actively developing solutions for affected enterprise customers, stating that it is working on a resolution for this issue, with plans to release an out-of-band update in the coming days.
For Azure customers experiencing immediate issues, Microsoft recommends utilizing self-help repair steps outlined in their support article: Repair a Windows VM using Azure Virtual Machine repair commands.
The timing of this issue is particularly challenging given that Windows 11 version 23H2 will continue receiving monthly security updates until November 11, 2025, for Home and Pro editions, while Enterprise and Education editions remain under mainstream support until November 10, 2026. Organizations may need to implement temporary workarounds, including system restore procedures or rolling back to previous system states, to maintain operational continuity until a permanent fix is deployed.
Broader Context of Windows Update Issues
This incident is part of a series of challenges Microsoft has faced with recent Windows updates. In April 2025, the company addressed a known issue causing erroneous 0x80070643 failure errors when installing Windows Recovery Environment (WinRE) updates. Although these errors were inaccurate and did not impact device functionality, they caused confusion among users. The affected updates included KB5057588 for Windows Server 2022 and KB5057589 for Windows 10 versions 22H2 and 21H2. Microsoft resolved this issue by ensuring that the incorrect error messages no longer appear after installing the updates.
In August 2024, Microsoft retired several Windows security updates released during the January 2024 Patch Tuesday that had been causing 0x80070643 errors when installing WinRE updates. The problematic updates, such as KB5034441 for Windows 10 21H2/22H2, KB5034440 for Windows 11 21H2, and KB5034439 for Windows Server 2022, were intended to fix a BitLocker encryption bypass flaw (CVE-2024-20666). However, they mistakenly displayed generic error messages due to insufficient disk space in the WinRE partition. After months of investigation, Microsoft decided not to provide an automated fix and instead asked users to manually resize their WinRE partitions by 250 MB to accommodate the new updates.
In July 2024, another issue emerged where some PCs booted into the BitLocker recovery screen after installing the July 2024 Windows security update. This problem affected Windows 11 versions 23H2, 22H2, and 21H2, as well as Windows 10 versions 22H2 and 21H2. Microsoft acknowledged the issue and advised users to enter their BitLocker recovery key to resume the boot process. The company worked on a fix, which was released in the following weeks.
In February 2024, Microsoft confirmed that the February 13 security update for Windows 11 might face installation issues, with the process failing at 96% and displaying a message: Something didn’t go as planned. No need to worry – undoing changes. Please keep your computer on. The issue affected Windows 11 versions 23H2 and 22H2. Microsoft provided a workaround involving the deletion of the hidden folder C:\$WinREAgent and promised a permanent fix in an upcoming release.
These incidents highlight the complexities involved in maintaining and updating modern operating systems, especially in diverse environments that include both physical and virtual machines. They also underscore the importance of thorough testing and prompt communication from software vendors to mitigate the impact of such issues on enterprise operations.