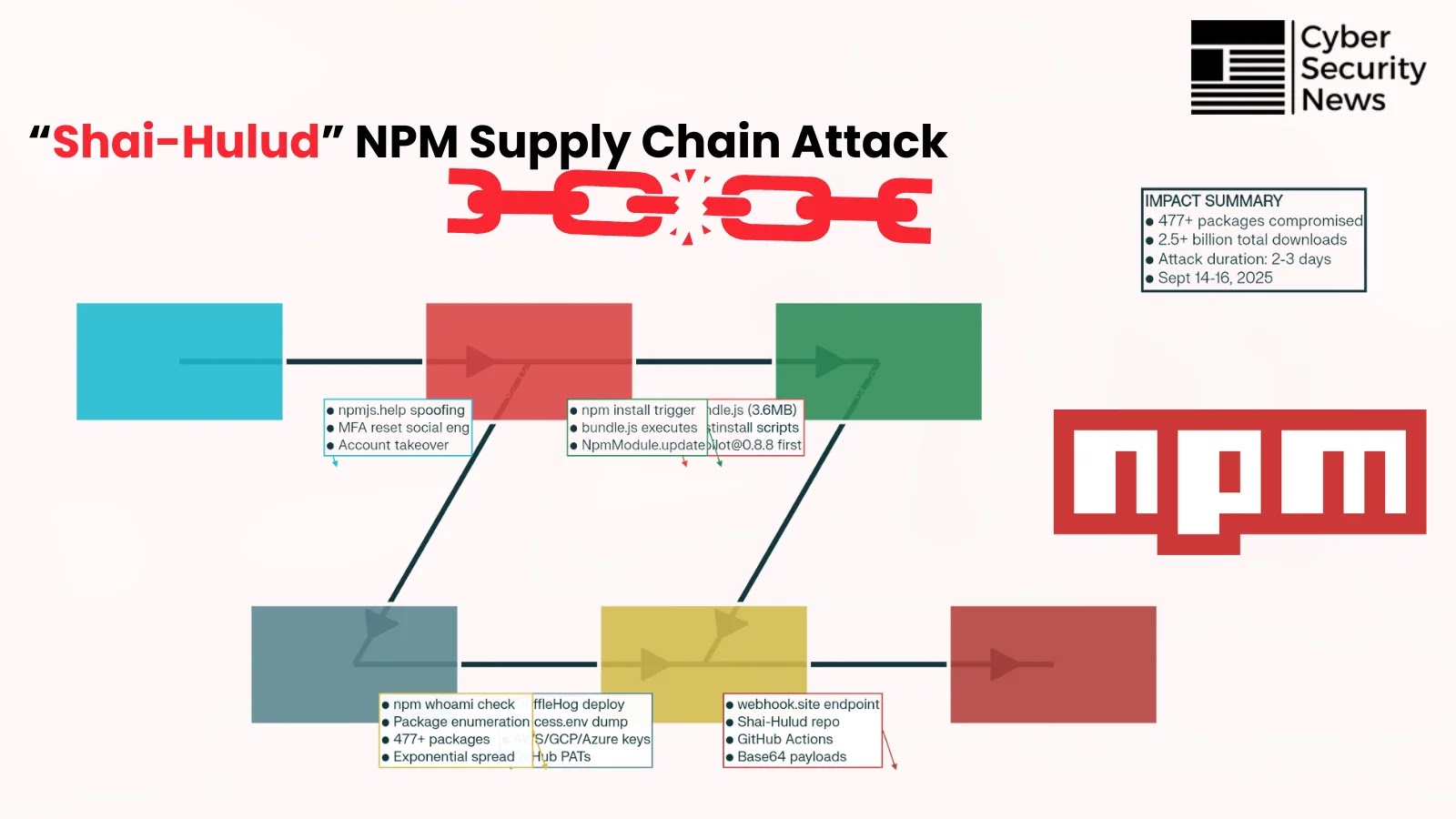
In September 2025, the JavaScript community faced an unprecedented supply chain attack when a self-replicating malware, dubbed Shai-Hulud, infiltrated the npm ecosystem. This sophisticated worm compromised over 477 npm packages, marking a significant evolution in the landscape of software supply chain threats.
The Genesis of the Attack
The Shai-Hulud campaign commenced with a targeted phishing operation aimed at npm package maintainers. Attackers crafted convincing emails from a fraudulent domain, npmjs[.]help, closely resembling the legitimate npmjs[.]com. These emails urged maintainers to update their multi-factor authentication credentials, exploiting the trust between developers and the npm platform. This social engineering tactic effectively deceived numerous maintainers, granting attackers access to their accounts.
Mechanics of the Self-Replicating Malware
Once inside, the attackers deployed the Shai-Hulud malware, a worm capable of autonomously propagating across the npm ecosystem. The malware utilized the `NpmModule.updatePackage` function to identify and infect additional packages maintained by compromised developers. The propagation process involved:
1. Downloading existing package tarballs.
2. Modifying `package.json` files to inject malicious `postinstall` scripts.
3. Embedding a minified `bundle.js` payload.
4. Repackaging the archives.
5. Republishing them to the npm registry.
This automated approach enabled the malware to spread rapidly, escalating from a few compromised packages to over 477 within approximately 72 hours.
Execution and Payload
Upon installation of an infected package via `npm install`, the `postinstall` script triggered the execution of the `bundle.js` payload. This script performed comprehensive system reconnaissance, including:
– Extracting environment variables to capture sensitive credentials.
– Deploying TruffleHog, an open-source secret scanning tool, to scan the local filesystem for various types of credentials.
– Validating credentials using `npm whoami` commands.
– Exfiltrating validated credentials to attacker-controlled servers.
The malware’s design ensured persistence by leveraging legitimate maintainer credentials, effectively turning trusted developers into unwitting vectors for malware distribution.
Credential Harvesting and Data Exfiltration
Shai-Hulud implemented a comprehensive credential harvesting strategy targeting multiple credential types and storage locations. The malware prioritized high-value credentials, including npm publishing tokens, GitHub Personal Access Tokens (PATs), and cloud service credentials for AWS, Google Cloud Platform, and Microsoft Azure.
The systematic approach included scanning `.npmrc` files for npm registry tokens, extracting SSH private keys (`id_rsa`) from default locations, and parsing Git configuration files (`.git/config`) for embedded credentials. The malware also targeted environment-specific credential storage, including `.env` files commonly used in development environments and CI/CD pipeline configurations. This comprehensive approach ensured maximum credential exposure across different development workflows and deployment scenarios.
The attack employed a dual-channel exfiltration strategy to ensure data persistence and accessibility. Primary exfiltration occurred through webhook endpoints at `webhook.site`, providing immediate access to stolen credentials via HTTP POST requests containing JSON-encoded credential data. The secondary exfiltration method involved creating public GitHub repositories named Shai-Hulud within compromised accounts, where complete credential dumps were stored as base64-encoded files.
The malware also established persistence through GitHub Actions workflows, injecting `.github/workflows/shai-hulud-workflow.yml` files that execute on code pushes and automatically exfiltrate repository secrets using the `toJSON(secrets)` function. This persistence mechanism ensured continued data collection even after the initial infection was removed from development machines.
Impact on High-Profile Packages
The Shai-Hulud attack’s reach extended to high-profile libraries and tools, amplifying its impact. Notably, packages from CrowdStrike, a leading cybersecurity firm, were among those compromised. The affected packages included multiple versions of `@crowdstrike/commitlint`, `@crowdstrike/glide-core`, `@crowdstrike/logscale-dashboard`, and others. The compromise of such packages underscored the attack’s severity and the potential risks to enterprise environments.
Mitigation Strategies
In response to the Shai-Hulud attack, several mitigation strategies have been recommended:
– Lock Dependency Versions: Pin to specific package versions and avoid wide semantic versioning ranges to prevent automatic inclusion of compromised updates.
– Rotate Secrets: Revoke and regenerate any exposed API tokens, SSH keys, and environment variables to mitigate the risk of unauthorized access.
– Audit Dependencies: Utilize tools like `npm audit`, Snyk, or OWASP Dependency-Check to identify and address vulnerabilities in project dependencies.
– Implement Runtime Monitoring: Deploy monitoring tools such as Sysmon on Windows or auditd on Linux to detect unexpected network calls or execution of malicious scripts.
Lessons Learned
The Shai-Hulud attack serves as a stark reminder of the evolving nature of supply chain threats. It highlights the importance of:
– Vigilant Credential Management: Ensuring that credentials are securely stored and regularly rotated to minimize the risk of compromise.
– Enhanced Developer Awareness: Educating developers about phishing tactics and the importance of verifying the authenticity of communications.
– Robust Security Practices: Implementing comprehensive security measures, including dependency management, code reviews, and continuous monitoring, to safeguard the software supply chain.
As open-source ecosystems remain prime targets, securing the software supply chain through rigorous validation and continuous monitoring is more critical than ever.