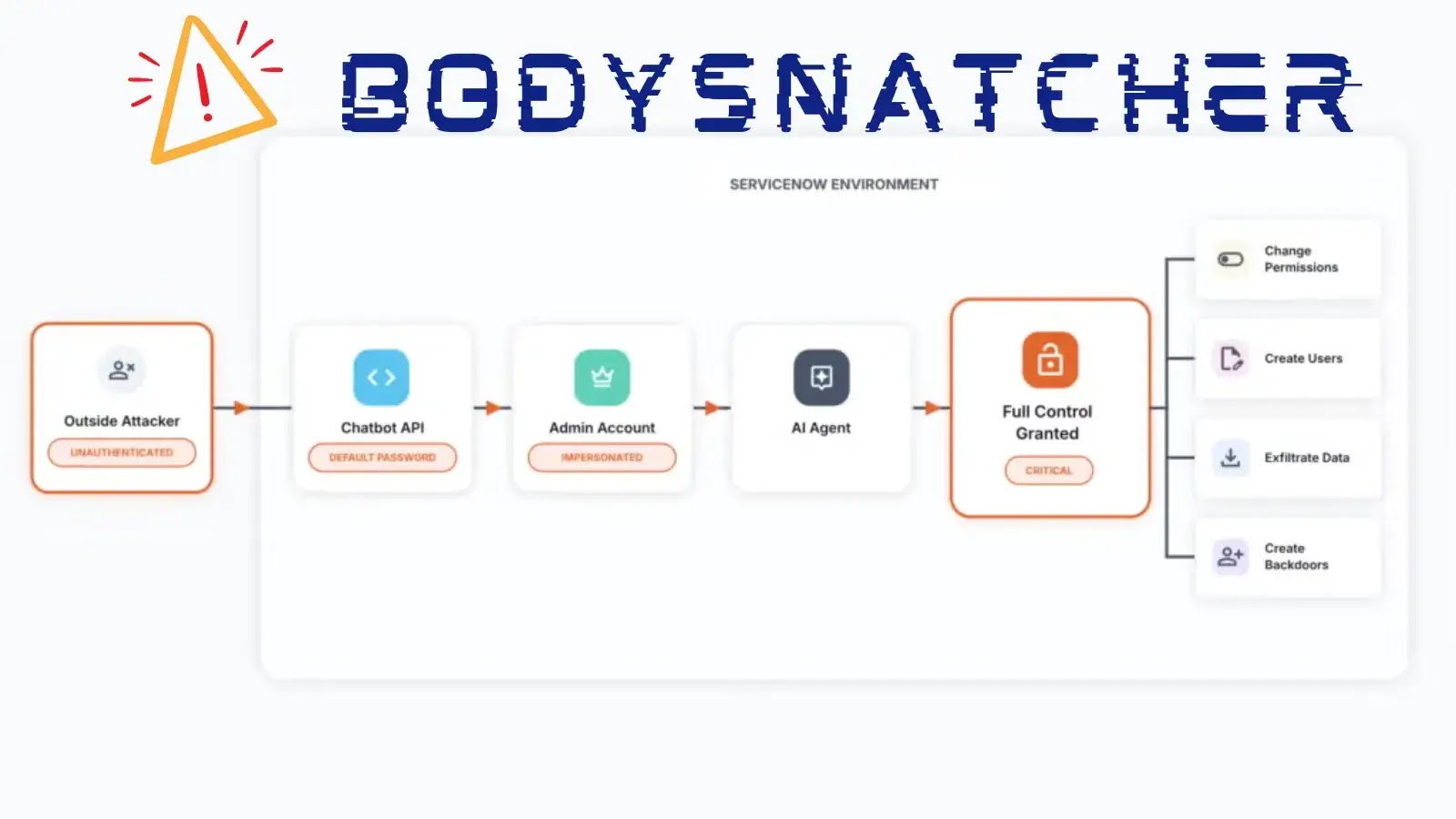
In a significant cybersecurity development, a sophisticated mobile ad fraud operation known as IconAds has been dismantled. This operation involved 352 Android applications designed to display intrusive advertisements and conceal their presence on users’ devices, complicating detection and removal efforts.
The Mechanics of IconAds
The IconAds scheme was engineered to generate revenue through deceptive means. Users would unknowingly download Android applications masquerading as legitimate tools—such as flashlights, file scanners, and photo editors. Once installed, these apps would hide their icons on the device’s home screen, making them difficult to locate and uninstall. Simultaneously, they would display ads on users’ screens, even when the apps were not actively in use.
At its peak, the IconAds operation was responsible for approximately 1.2 billion ad bid requests daily. The majority of this fraudulent traffic originated from Brazil, Mexico, and the United States. The financial impact of this scheme is estimated to be in the seven-figure range, underscoring the substantial economic consequences of such fraudulent activities.
Detection and Disruption
The cybersecurity firm HUMAN played a pivotal role in uncovering the IconAds operation. Their Satori Threat Intelligence and Research Team identified the malicious apps and alerted Google, leading to the removal of all 352 applications from the Google Play Store. This action highlights the importance of collaboration between cybersecurity entities and platform providers in mitigating digital threats.
Evolving Tactics of Ad Fraud
IconAds is a variant of a broader category of threats tracked by various cybersecurity vendors under names like HiddenAds and Vapor. These malicious applications have been infiltrating the Google Play Store since at least 2019, continually evolving to evade detection.
Common characteristics of these apps include:
– Obfuscation Techniques: Concealing device information during network communications to avoid detection.
– Command-and-Control (C2) Domain Patterns: Utilizing consistent naming conventions for C2 domains to maintain control over the apps.
– Activity Alias Declaration: Replacing the default MAIN/LAUNCHER activity by declaring an alias, which allows the app to hide its icon and name from the home screen, complicating uninstallation efforts.
Some iterations of IconAds apps have gone a step further by impersonating legitimate applications like the Google Play Store. In these cases, clicking on the app redirects the user to the official application, while malicious activities occur in the background.
Broader Implications and Related Threats
The disruption of IconAds sheds light on the persistent and evolving nature of mobile ad fraud. Similar operations, such as Kaleidoscope, have been identified, employing tactics like the evil twin technique. In this method, cybercriminals create two nearly identical versions of an app: a harmless decoy twin available on Google Play and a malicious evil twin distributed through third-party app stores. The evil twin generates intrusive ads to fraudulently earn advertising revenue.
These developments underscore the need for continuous vigilance and adaptive security measures to combat the ever-changing landscape of cyber threats.
Protecting Yourself from Ad Fraud
To safeguard against such fraudulent applications, users are advised to:
– Download Apps from Trusted Sources: Stick to official app stores and verify the credibility of the app and its developer.
– Review App Permissions: Be cautious of apps requesting unnecessary permissions that could indicate malicious intent.
– Monitor Device Behavior: Stay alert to unusual device behavior, such as unexpected ads or rapid battery drain, which could signal the presence of malicious apps.
– Utilize Security Software: Employ reputable mobile security applications to detect and remove potential threats.
By adopting these practices, users can enhance their defense against deceptive applications and contribute to a more secure digital environment.