Phishing attacks have evolved, employing increasingly sophisticated methods to deceive users and bypass security measures. A recent tactic involves the use of Scalable Vector Graphics (SVG) files, which, while typically harmless, can be manipulated to carry out malicious activities. This article delves into the mechanics of such attacks, provides insights into their detection, and offers strategies for mitigation.
Understanding the Threat: Malicious SVGs in Phishing
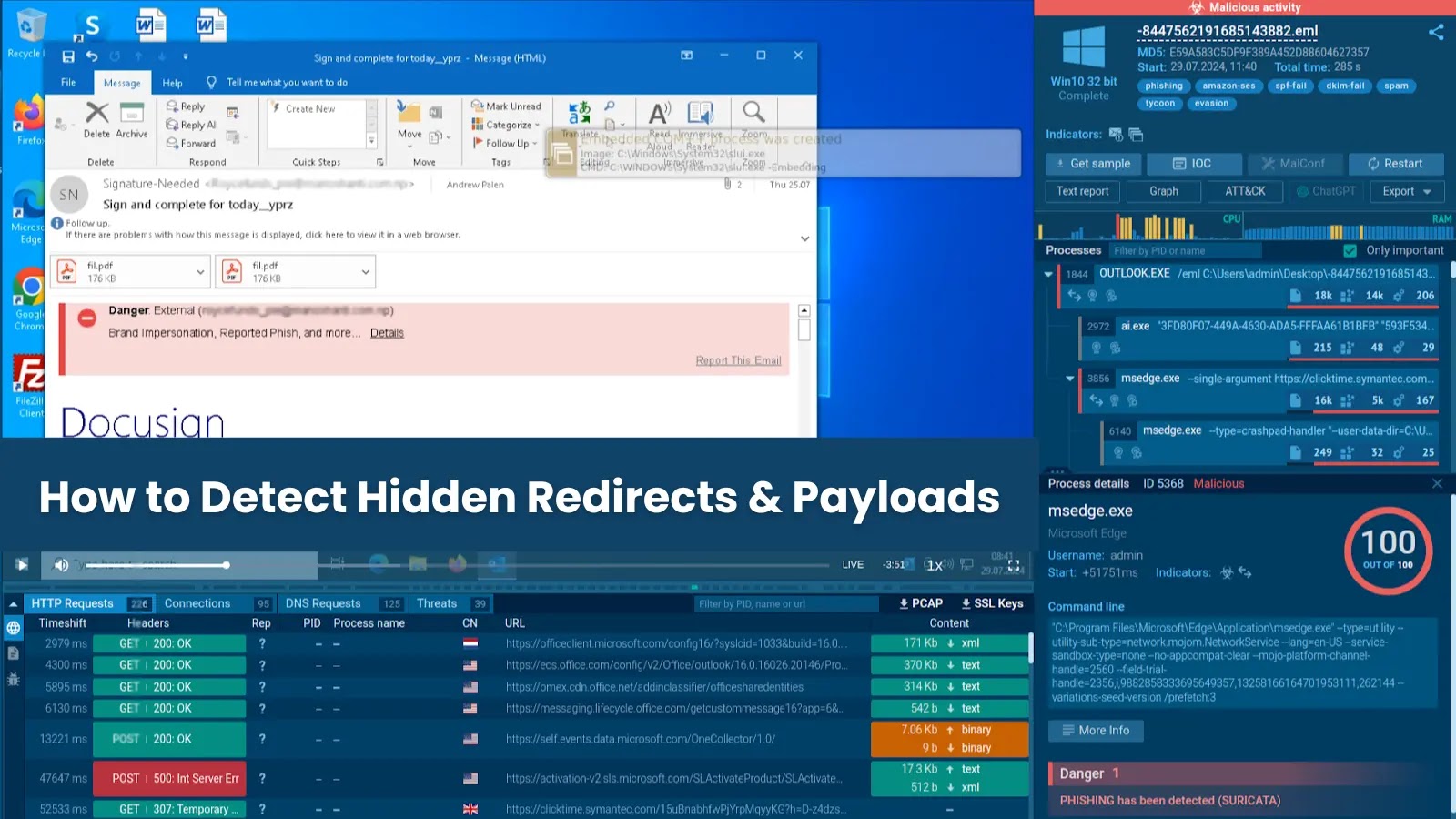
SVG files are XML-based image formats that support interactivity and animation. Their versatility allows for the embedding of scripts, a feature that cybercriminals exploit to execute malicious code. In recent phishing campaigns, attackers have disguised SVG files as legitimate documents, such as PDFs, to trick users into opening them. Once accessed, these files can initiate a series of redirects leading to credential-harvesting sites or deploy malware onto the victim’s system.
Case Study: Anatomy of an SVG-Based Phishing Attack
A notable instance of this tactic was observed in a campaign where malicious SVG files were distributed via phishing emails. These emails contained attachments that appeared to be standard PDF documents but were, in fact, SVG files with embedded JavaScript. Upon opening the attachment in a browser, the following sequence unfolded:
1. Deceptive Prompt: The SVG file displayed a message indicating that the document was protected, urging the user to click or wait, thereby engaging in social engineering to prompt further interaction.
2. Script Execution: Embedded JavaScript within the SVG executed an XOR decoding routine, reconstructing and executing a hidden redirect script.
3. Layered Redirects: The decoded script navigated the browser through multiple intermediary domains, obfuscating the attack’s origin and intent.
4. Credential Harvesting: The final destination was a phishing page mimicking a legitimate Microsoft login portal, complete with elements like Cloudflare’s Turnstile widget to enhance credibility. Unsuspecting users who entered their credentials had their information captured and transmitted to attacker-controlled infrastructure.
Detection and Analysis: Leveraging Sandbox Environments
Identifying and analyzing such sophisticated attacks necessitate advanced tools. Interactive sandbox environments, such as those provided by cybersecurity platforms, play a crucial role in this process. By executing the suspicious file in a controlled setting, analysts can observe the full attack chain in real-time, including:
– Redirects and HTTP Transactions: Monitoring the sequence of redirects and network communications initiated by the malicious SVG.
– Decoded Scripts: Examining the reconstructed JavaScript to understand its functionality and intent.
– Runtime Artifacts: Capturing any files or processes spawned during the attack for further analysis.
These insights enable security teams to extract Indicators of Compromise (IOCs) and integrate them into existing security information and event management (SIEM) systems, enhancing detection capabilities and response times.
Mitigation Strategies: Strengthening Defenses Against SVG-Based Phishing
To protect against such threats, organizations and individuals should adopt a multi-layered security approach:
1. Email Filtering: Implement advanced email security solutions capable of detecting and quarantining emails with suspicious attachments or links.
2. User Education: Conduct regular training sessions to raise awareness about phishing tactics, emphasizing caution with unexpected attachments, even those appearing as common file types.
3. Attachment Analysis: Utilize sandboxing technologies to analyze attachments in a controlled environment before they reach the end-user.
4. Regular Updates: Keep all software, especially email clients and web browsers, updated to patch vulnerabilities that could be exploited by malicious scripts.
5. Restrict Script Execution: Configure browsers and email clients to limit or disable the execution of scripts within SVG files, reducing the risk of automatic code execution.
Conclusion
The exploitation of SVG files in phishing campaigns underscores the need for vigilance and advanced security measures. By understanding the mechanisms of such attacks and implementing robust detection and mitigation strategies, organizations can better protect themselves against these evolving threats.