In recent times, a new form of cyberattack known as ClickFix has emerged, posing significant threats to users and organizations alike. This method involves deceiving individuals into executing malicious commands on their devices by copying and pasting code provided by attackers. Understanding the mechanics and effectiveness of ClickFix attacks is crucial for developing strategies to mitigate their impact.
What is ClickFix?
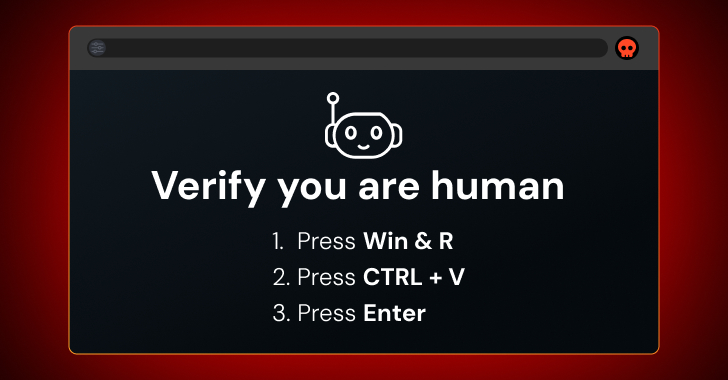
ClickFix attacks, also referred to as FileFix or fake CAPTCHA attacks, manipulate users into interacting with malicious scripts within their web browsers. Typically, these attacks present users with a prompt to solve a problem or complete a challenge, such as a CAPTCHA or fixing a webpage error. The critical aspect of these attacks is that they trick users into copying malicious code from the webpage’s clipboard and executing it locally on their devices.
This technique has been employed by various threat actors, including the Interlock ransomware group and state-sponsored Advanced Persistent Threats (APTs). Notable data breaches linked to ClickFix-style tactics include incidents at Kettering Health, DaVita, the City of St. Paul in Minnesota, and the Texas Tech University Health Sciences Centers.
Three Factors Contributing to the Effectiveness of ClickFix Attacks
1. Lack of User Preparedness
Traditional cybersecurity awareness programs have primarily focused on educating users about the dangers of clicking on suspicious links, downloading unverified files, and entering credentials on untrusted websites. However, these programs often do not address the risks associated with executing commands manually. ClickFix attacks exploit this gap by instructing users to perform actions that seem legitimate, such as copying and pasting commands, which are not typically flagged as suspicious.
Moreover, the malicious clipboard copying is often executed automatically through JavaScript, without explicit user consent. This automation reduces the likelihood of users questioning the legitimacy of the action. As ClickFix sites become more sophisticated and legitimate-looking, users are more likely to comply with the instructions provided.
2. Evasion of Detection Mechanisms
ClickFix attacks employ various techniques to evade detection by security tools. These include:
– Domain Camouflage and Rotation: Attackers frequently change domains and use legitimate-looking URLs to avoid being blacklisted.
– Bot Protection: Implementing measures to prevent automated analysis by security tools.
– Content Obfuscation: Heavily obfuscating page content to prevent detection signatures from triggering.
Additionally, by utilizing delivery vectors beyond email, such as search engine optimization (SEO) poisoning and malvertising, attackers bypass traditional email-based detection systems. This diversification makes it more challenging for security tools to identify and block malicious content.
3. Exploitation of Trusted Platforms
Attackers leverage trusted platforms and services to host and distribute ClickFix attacks, enhancing their credibility and effectiveness. For instance:
– Compromised Websites: Infecting legitimate websites to serve malicious content.
– Malvertising: Using legitimate advertising networks to display malicious ads that lead to ClickFix pages.
– SEO Poisoning: Manipulating search engine results to direct users to malicious sites.
By exploiting these trusted platforms, attackers increase the likelihood of users encountering and interacting with ClickFix lures.
Mitigation Strategies
To combat the threat posed by ClickFix attacks, organizations and individuals should consider the following strategies:
– Enhanced User Education: Expand cybersecurity training programs to include awareness of social engineering tactics that involve manual command execution.
– Technical Controls: Implement security solutions capable of detecting and blocking obfuscated scripts and monitoring for unusual clipboard activities.
– Monitoring and Response: Establish robust monitoring systems to detect signs of compromise and develop incident response plans to address potential breaches promptly.
By understanding the factors contributing to the success of ClickFix attacks and implementing comprehensive mitigation strategies, organizations can better protect themselves against this evolving threat landscape.