PLUGGYAPE Malware Exploits Signal and WhatsApp to Infiltrate Ukrainian Defense Systems
Between October and December 2025, the Computer Emergency Response Team of Ukraine (CERT-UA) identified a series of cyber attacks targeting the nation’s defense forces. These attacks were orchestrated using a sophisticated malware known as PLUGGYAPE. The perpetrators have been tentatively linked to a Russian hacking group referred to as Void Blizzard, also known by aliases such as Laundry Bear or UAC-0190. This group has been active since at least April 2024.
Attack Methodology:
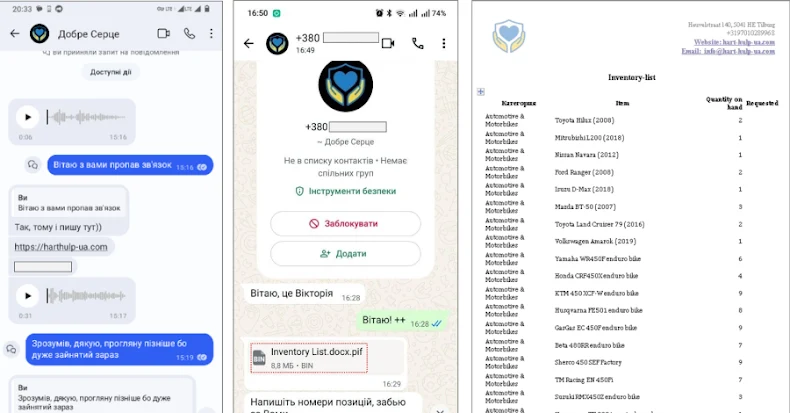
The attackers employed popular messaging platforms, Signal and WhatsApp, as primary vectors for distributing the malware. By impersonating reputable charity organizations, they deceived targets into clicking on seemingly benign links, such as harthulp-ua[.]com or solidarity-help[.]org. These links led to the download of password-protected archives containing malicious executables crafted with PyInstaller. Once executed, these files deployed the PLUGGYAPE malware onto the victim’s system.
Evolution of PLUGGYAPE:
Over time, PLUGGYAPE has undergone significant enhancements to evade detection and analysis. The malware now incorporates advanced obfuscation techniques and anti-analysis mechanisms designed to prevent execution within virtual environments, complicating efforts by cybersecurity professionals to dissect and understand its operations.
Technical Specifications:
Developed in Python, PLUGGYAPE establishes communication with remote servers using protocols like WebSocket and, more recently, Message Queuing Telemetry Transport (MQTT). This communication framework grants attackers the capability to execute arbitrary code on compromised systems. Notably, support for MQTT was integrated into the malware’s architecture in December 2025, indicating ongoing development and adaptation by its creators.
Command-and-Control Infrastructure:
To maintain operational security and resilience, the malware retrieves command-and-control (C2) server addresses from external paste services, including rentry[.]co and pastebin[.]com. These addresses are stored in a base64-encoded format, allowing attackers to dynamically update C2 servers in real-time. This strategy ensures continued control over infected systems, even if original infrastructure components are identified and neutralized.
Sophisticated Social Engineering Tactics:
The initial phases of these cyber attacks are characterized by advanced social engineering techniques. Attackers utilize legitimate accounts and phone numbers from Ukrainian mobile operators, communicate fluently in Ukrainian, and engage in audio and video interactions. They often possess detailed knowledge about their targets, including personal information and organizational operations, enhancing the credibility of their deceptive communications.
Broader Cyber Threat Landscape:
CERT-UA has also reported on other cyber threats targeting Ukrainian entities:
– UAC-0239 Campaign: This campaign involved phishing emails sent from UKR[.]net and Gmail addresses. These emails contained links to Virtual Hard Disk (VHD) files or direct attachments that deployed a Go-based stealer named FILEMESS. FILEMESS is designed to collect files with specific extensions and exfiltrate them via Telegram. Additionally, the campaign utilized an open-source command-and-control framework called OrcaC2, enabling system manipulation, file transfers, keylogging, and remote command execution. The primary targets were Ukrainian defense forces and local government bodies.
– UAC-0241 Campaign: This spear-phishing initiative targeted educational institutions and state authorities. It employed ZIP archives containing Windows shortcut (LNK) files. When opened, these shortcuts triggered the execution of an HTML Application (HTA) via mshta.exe. The HTA payload launched JavaScript designed to download and execute a PowerShell script, which subsequently delivered tools like LaZagne for password recovery and a Go backdoor named GAMYBEAR. GAMYBEAR can receive and execute commands from a server and transmit results back in Base64-encoded form over HTTP.
Implications and Recommendations:
The utilization of widely-used messaging platforms like Signal and WhatsApp as delivery channels for malware underscores the evolving nature of cyber threats. These platforms, integral to both personal and professional communication, are increasingly being exploited to disseminate malicious software.
To mitigate such threats, it is imperative for organizations and individuals to:
1. Exercise Caution with Unsolicited Communications: Be wary of messages from unknown sources, especially those containing links or attachments, even if they appear to originate from legitimate organizations.
2. Verify Authenticity: Before interacting with links or downloading files, verify the authenticity of the sender and the content. Contact organizations directly through official channels to confirm the legitimacy of communications.
3. Implement Robust Security Measures: Utilize comprehensive security solutions that include real-time threat detection, email filtering, and endpoint protection to identify and block malicious activities.
4. Educate and Train Personnel: Regularly conduct cybersecurity awareness training to equip individuals with the knowledge to recognize and respond to phishing attempts and other social engineering tactics.
5. Maintain Updated Systems: Ensure that all software, including operating systems and applications, are regularly updated to patch vulnerabilities that could be exploited by attackers.
By adopting these proactive measures, organizations can enhance their resilience against sophisticated cyber threats like PLUGGYAPE and safeguard their critical assets and information.