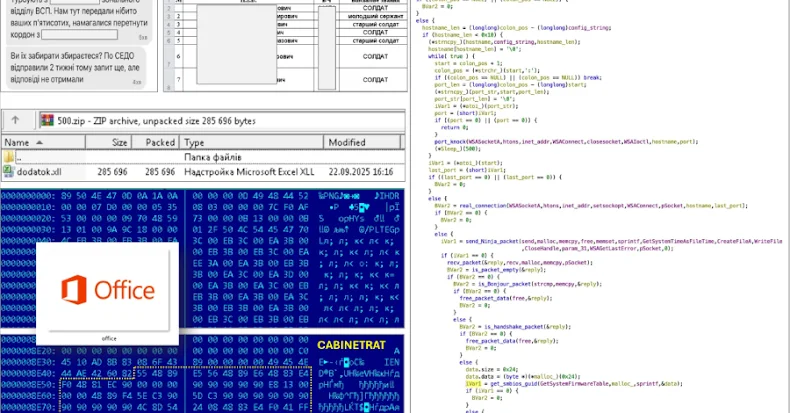
In September 2025, the Computer Emergency Response Team of Ukraine (CERT-UA) identified a series of targeted cyber attacks employing a backdoor named CABINETRAT. These incidents have been linked to a threat group designated as UAC-0245. The attacks were first detected through the discovery of malicious software masquerading as Microsoft Excel add-ins, known as XLL files. These add-ins are typically used to enhance Excel’s functionality with custom features.
Distribution Method:
The malicious XLL files were disseminated via ZIP archives shared on the Signal messaging application. These archives were cleverly disguised as documents related to the detention of individuals attempting to cross the Ukrainian border, thereby increasing the likelihood of recipients opening the files.
Execution and Persistence:
Upon execution, the XLL files initiate the creation of several components on the compromised system:
– An executable file placed in the Startup folder to ensure the malware runs upon system boot.
– An XLL file named BasicExcelMath.xll located in the %APPDATA%\Microsoft\Excel\XLSTART\ directory, which allows it to load automatically when Excel starts.
– A PNG image titled Office.png that contains embedded malicious code.
To maintain persistence, the malware modifies the Windows Registry. It then launches the Excel application in a hidden mode using the /e (/embed) parameter, which facilitates the execution of the XLL add-in. The primary function of this add-in is to parse and extract shellcode from the Office.png file, leading to the deployment of the CABINETRAT backdoor.
Evasion Techniques:
Both the XLL payload and the extracted shellcode incorporate multiple anti-analysis and anti-virtual machine (VM) techniques to evade detection:
– Verification that the system has at least two processor cores and a minimum of 3GB of RAM.
– Detection of virtualization tools such as VMware, VirtualBox, Xen, QEMU, Parallels, and Hyper-V.
These measures are designed to prevent the malware from executing in controlled environments typically used by security researchers.
Capabilities of CABINETRAT:
CABINETRAT is a comprehensive backdoor written in the C programming language, equipped with functionalities that include:
– Collecting detailed system information.
– Listing installed applications.
– Capturing screenshots.
– Enumerating directory contents.
– Deleting specific files or directories.
– Executing arbitrary commands.
– Facilitating file uploads and downloads.
The backdoor communicates with a remote command-and-control (C2) server over a TCP connection, allowing attackers to remotely control the compromised system.
Context and Related Incidents:
This disclosure follows closely on the heels of warnings from Fortinet FortiGuard Labs about attacks targeting Ukraine. In these incidents, attackers impersonated the National Police of Ukraine in a fileless phishing campaign. The campaign aimed to deploy Amatera Stealer and PureMiner malware, designed to harvest sensitive data and mine cryptocurrency on infected systems.
The emergence of CABINETRAT underscores the evolving tactics of cyber adversaries targeting Ukraine. The use of legitimate communication platforms like Signal to distribute malware highlights the need for heightened vigilance and robust cybersecurity measures.