Security Operations Centers (SOCs) are the frontline defense against cyber threats, operating in an environment where alerts are incessant, workloads are substantial, and the demand for rapid response is unrelenting. This high-pressure setting often leads to analyst burnout, prolonged incident investigations, and an increased risk of overlooking critical threats. However, by integrating interactive sandboxing and intelligent automation into their workflows, SOCs can enhance efficiency, reduce stress, and improve their ability to neutralize threats promptly.
1. Real-Time Visualization of the Entire Attack Chain
A significant contributor to analyst fatigue is the delay inherent in traditional threat detection tools. These systems can take hours to confirm the legitimacy of an alert, during which time threats may propagate within the network, compounding the workload and stress on the SOC team.
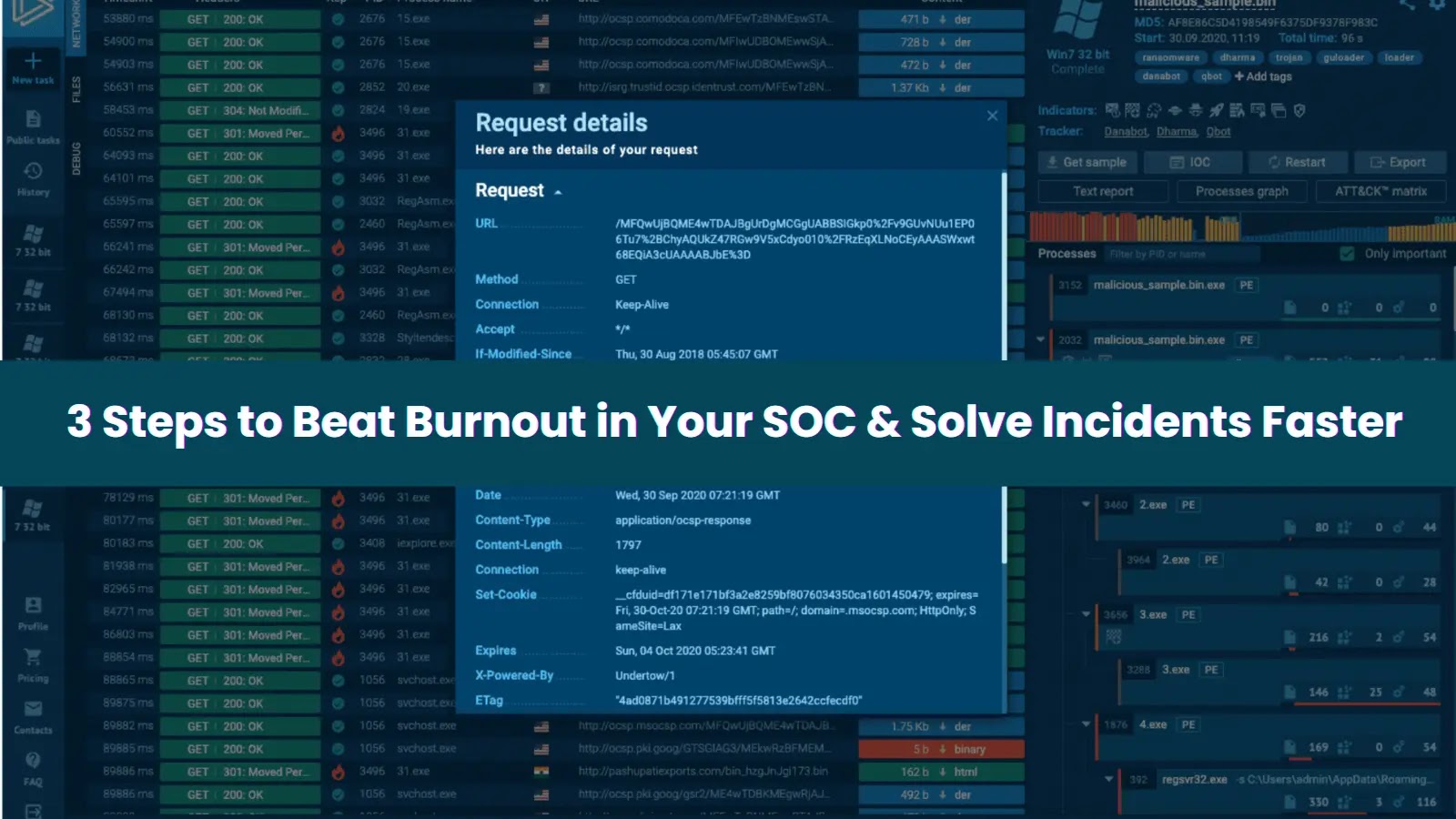
Interactive sandboxes, such as ANY.RUN, offer a transformative solution by allowing analysts to observe attacks as they unfold within a secure virtual environment. Suspicious files, URLs, or scripts are executed immediately, providing a comprehensive view of the attack’s progression—from initial entry to payload delivery—without jeopardizing live systems.
This immediate visibility enables analysts to make swift, informed decisions, often within seconds. For example, an analysis session utilizing ANY.RUN revealed the complete attack chain of a LockBit 5.0 ransomware incident in just 33 seconds.
Organizations employing interactive sandboxing have reported notable improvements:
– 88% of attacks are identified within the first 60 seconds of analysis.
– An average increase of 36% in detection rates.
By reducing investigation times and enhancing detection capabilities, SOCs can manage a higher volume of threats with less strain on their teams.
2. Automated Detection of Evasive Threats
Cyber adversaries often design attacks to evade detection by remaining dormant until specific user actions—such as clicking a link, solving a CAPTCHA, or downloading a file—trigger their execution. Traditional detection tools may struggle to replicate these actions, necessitating manual intervention by analysts, which is both time-consuming and mentally taxing.
ANY.RUN’s interactive sandbox addresses this challenge through its Automated Interactivity feature. This functionality simulates real user behaviors within a controlled virtual machine, automatically performing actions like clicking links, solving CAPTCHAs, opening attachments, and following redirects. As a result, even the most elusive threats are exposed without requiring manual effort from analysts.
For instance, in a recent analysis session, the sandbox autonomously:
– Extracted a malicious link embedded within a QR code.
– Solved a CAPTCHA to access the final phishing page.
– Compiled a detailed report containing Indicators of Compromise (IOCs) and Tactics, Techniques, and Procedures (TTPs).
The implementation of such automation has led to tangible benefits:
– Up to 58% more hidden threats identified compared to traditional methods.
– A 30% reduction in escalations from Tier 1 to Tier 2 analysts, as junior staff can resolve more incidents independently.
By automating routine tasks, SOCs can allocate their human resources more effectively, focusing on complex threats and strategic initiatives.
3. Streamlining Workflows to Mitigate Alert Fatigue
The sheer volume of alerts generated by security systems can overwhelm analysts, leading to alert fatigue—a state where critical threats may be overlooked due to the constant influx of notifications. This not only increases the risk of security breaches but also contributes to analyst burnout.
To combat this, SOCs can implement the following strategies:
– Consolidation of Security Tools: Reducing the number of disparate security tools and adopting unified platforms can decrease alert volumes by 30% while enhancing visibility.
– Automation of Repetitive Tasks: Deploying AI-driven automation for tasks such as log analysis, patch management, and phishing detection can handle 60-70% of routine alerts, allowing analysts to concentrate on high-priority threats.
– Normalization of Mental Health Support: Implementing mandatory stress-management training and providing confidential counseling services can lead to a 40% reduction in turnover within security roles.
– Streamlining Compliance Workflows: Replacing manual audits with continuous compliance platforms can reduce documentation burdens by 50%, preventing “checkbox fatigue.”
– Rotation of On-Call Schedules: Enforcing structured shift rotations to prevent 24/7 availability expectations can result in a 25% improvement in incident response rates.
By adopting these measures, SOCs can create a more sustainable work environment, reducing burnout and enhancing overall operational effectiveness.
Conclusion
The relentless nature of cyber threats necessitates a proactive and efficient approach to security operations. By integrating interactive sandboxing, automating routine tasks, and implementing strategies to reduce alert fatigue, SOCs can alleviate analyst burnout and expedite incident resolution. These steps not only enhance the well-being of security teams but also fortify the organization’s defenses against an ever-evolving threat landscape.