CastleLoader Malware: A Stealthy Threat to U.S. Government Agencies
In early 2025, cybersecurity experts identified a sophisticated malware loader named CastleLoader, which has since emerged as a significant threat to U.S. government agencies and critical infrastructure. This stealthy malware has been instrumental in coordinated attacks targeting federal agencies, IT firms, logistics companies, and essential infrastructure providers across North America and Europe.
CastleLoader operates as a multi-stage loader, delivering secondary payloads directly into system memory. This method makes detection by traditional security defenses particularly challenging. Its primary function is to establish an initial foothold on compromised systems, subsequently deploying more dangerous tools such as information stealers and remote access trojans (RATs). These tools grant attackers complete control over infected networks. The loader’s universal nature and high infection rate have made it a preferred tool among threat actors aiming to compromise high-value targets while evading detection systems.
Infection Vectors and Techniques
CastleLoader employs sophisticated social engineering techniques to infiltrate systems. One prevalent method is the ClickFix phishing technique, where victims encounter fake software update prompts or system verification messages. When users comply with these deceptive requests, they unknowingly execute malicious commands that deliver CastleLoader as the second stage of the attack chain. This approach effectively bypasses user awareness training and initial security controls.
Another distribution method involves fake GitHub repositories that mimic legitimate tools. For instance, a repository may pose as SQL Server Management Studio (SSMS-lib), exploiting developers’ trust in GitHub. Users who unknowingly download and execute these malicious installers compromise their machines with malware. This technique capitalizes on developers’ tendency to run installation commands from repositories that appear reputable.
Technical Sophistication and Evasion Mechanisms
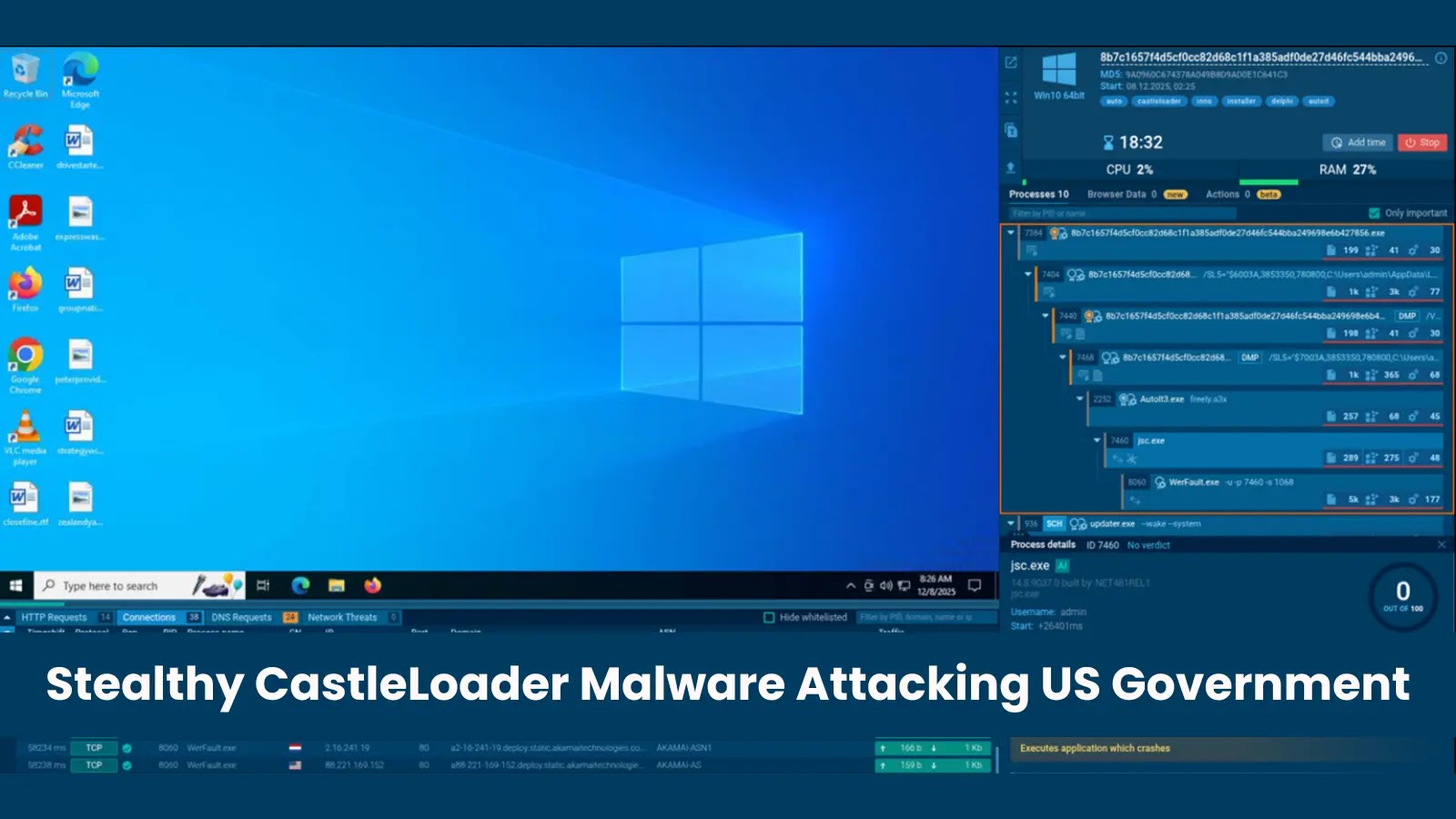
CastleLoader’s infection mechanism is a masterclass in stealth and obfuscation. The malware arrives packaged as an Inno Setup installer file containing multiple components, including AutoIt3.exe and a compiled AutoIt script stored as freely.a3x. Upon execution, the AutoIt script initiates the next phase by launching the jsc.exe process (a legitimate JScript.NET compiler) with the CREATE_SUSPENDED flag, pausing the process immediately after creation.
Instead of executing in this suspended state, the malware employs a refined process hollowing technique, injecting a fully functional PE executable directly into the jsc.exe memory space. This method allows the malware to distribute its malicious activity across multiple legitimate-looking processes, effectively hiding in plain sight.
Further analysis reveals that CastleLoader does not operate as a simple executable but relies on a complex layered approach, making each stage appear relatively benign upon initial inspection. This strategy enables the malware to evade modern security tools effectively.
Impact and Reach
Since May 2025, CastleLoader campaigns have leveraged seven distinct command-and-control (C2) servers, with over 1,634 infection attempts recorded during this period. Analysis of its C2 infrastructure and web-based panel—which is used to oversee and manage the infections—shows that as many as 469 devices were compromised, resulting in an infection rate of 28.7%.
The malware’s modular structure allows it to act as both a delivery mechanism and a staging utility, enabling threat actors to separate initial infection from payload deployment. This separation complicates attribution and response because it decouples the infection vector from the eventual malware behavior, giving attackers more flexibility in adapting campaigns over time.
Payloads and Secondary Infections
CastleLoader’s versatility is evident in its ability to deploy a range of secondary payloads, including:
– Information Stealers: Tools like StealC, RedLine, and DeerStealer focus on harvesting credentials, browser data, and cryptocurrency wallets.
– Remote Access Trojans (RATs): NetSupport RAT and SectopRAT provide backdoor access for persistent control over infected systems.
– Other Loaders: HijackLoader, another loader, further extends the attack chain, amplifying CastleLoader’s versatility.
These payloads serve different malicious purposes, from credential harvesting and cryptocurrency wallet theft to establishing persistent backdoor access for continued system control.
Recommendations for Mitigation
Given the sophisticated nature of CastleLoader and its evolving techniques, organizations are advised to implement the following measures:
1. User Education: Conduct regular training sessions to raise awareness about phishing techniques and the risks associated with executing commands from unverified sources.
2. Email Filtering: Implement advanced email filtering solutions to detect and block phishing attempts before they reach end-users.
3. Endpoint Detection and Response (EDR): Deploy EDR solutions capable of identifying and responding to suspicious activities indicative of malware infections.
4. Regular Software Updates: Ensure all software and systems are up-to-date with the latest security patches to mitigate vulnerabilities that malware like CastleLoader may exploit.
5. Network Segmentation: Implement network segmentation to limit the spread of malware within an organization, reducing the potential impact of an infection.
By adopting these proactive measures, organizations can enhance their defenses against CastleLoader and similar sophisticated malware threats.