Enhancing SOC Maturity Through Effective Threat Hunting
In the ever-evolving landscape of cybersecurity, Security Operations Centers (SOCs) are at the forefront of defending organizations against sophisticated threats. A pivotal component of a mature SOC is proactive threat hunting—actively seeking out potential threats before they manifest into full-blown incidents. However, many SOCs encounter challenges that impede the effectiveness of their threat hunting initiatives, leading to prolonged detection times and increased organizational risk.
The Challenges of Traditional Threat Hunting
Traditional threat hunting often relies on fragmented data sources and outdated intelligence. Analysts may have a solid understanding of attacker techniques, such as those outlined in frameworks like MITRE ATT&CK, but translating this knowledge into scalable and actionable detections proves difficult without comprehensive execution data. Indicators of Compromise (IOCs) are frequently received in isolation, lacking the contextual sequences that reveal the progression of an attack or the specific assets targeted.
This lack of context results in threat hunts that can consume weeks of analyst time, yielding low-confidence outputs. Consequently, leadership may perceive a poor return on investment, as proactive efforts fail to demonstrably reduce incident risks. Delayed threat discovery allows attackers to achieve persistence, steal credentials, or move laterally within networks before detection, escalating incident costs due to broader containment scopes and extended investigations. Additionally, analysts may experience burnout from engaging in low-yield tasks, diverting their focus from high-impact work.
The Role of Sandbox-Derived Threat Intelligence
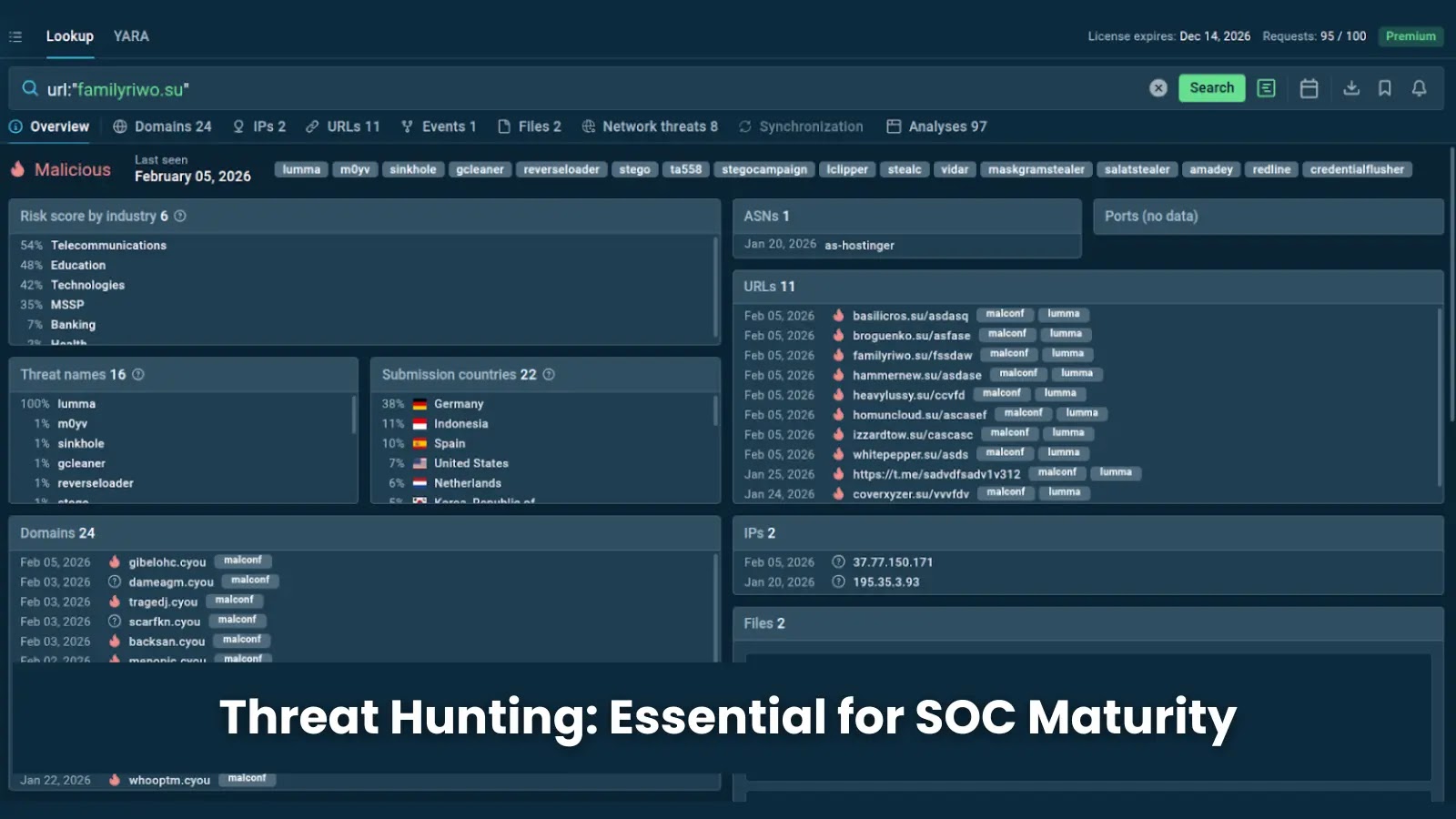
To address these challenges, leading SOCs are turning to threat intelligence derived from live executions rather than static reports. Tools like ANY.RUN’s Threat Intelligence (TI) Lookup exemplify this approach by aggregating data from over 50 million sandbox sessions conducted by more than 15,000 SOC teams and 600,000 analysts. Launched in 2024 and refined through 2025, TI Lookup offers rapid searches across a wide array of indicator types, including IOCs, Indicators of Behavior (IOBs), Indicators of Attack (IOAs), and Tactics, Techniques, and Procedures (TTPs).
The freshness of this data is ensured by processing approximately 16,000 daily threats interactively, capturing evasive malware that static tools might miss. Key features of TI Lookup include API and SDK integrations with Security Information and Event Management (SIEM) systems, Security Orchestration, Automation, and Response (SOAR) platforms, and Threat Intelligence Platforms (TIPs). It also supports YARA rule testing against real samples and offers filters for industry, geography, and timeframes, enhancing the relevance and applicability of the intelligence provided.
Enhancing Threat Hunting with Real-Time Data
Integrating real-time, sandbox-derived threat intelligence into the threat hunting process can significantly improve the efficiency and effectiveness of SOC operations. For instance, when generating hypotheses about potential threats, analysts can validate their assumptions against executions from a vast network of SOCs, providing broader visibility and enabling earlier detections.
During indicator analysis, enriched data with behavioral history from fresh executions allows for a more nuanced understanding of potential threats, reducing false positives and accelerating the triage process. Exploring attacker techniques becomes more concrete when analysts can reference live executions with full context, leading to better coverage of evasive attacks.
Prioritization of threats is also enhanced by filtering intelligence based on active targeting within specific industries or geographies, enabling SOCs to focus on business-relevant threats. Validation of detection rules and response strategies can be conducted pre-deployment using real data and YARA testing, reducing mean time to respond (MTTR) and lowering recovery costs.
Practical Application: MITRE Technique Hunts
Consider the MITRE ATT&CK technique T1036.003 (Masquerading: Rename System Utilities), identified as a prevalent method in 2025 based on sandbox data. Using TI Lookup, analysts can access numerous executions demonstrating instances where processes like svchost.exe are renamed to mimic legitimate tools. This capability allows for the identification of patterns and behaviors associated with specific attack techniques, facilitating the development of more effective detection and response strategies.
Conclusion
Effective threat hunting is essential for the maturity and success of SOCs. By leveraging real-time, sandbox-derived threat intelligence, SOCs can overcome the limitations of traditional threat hunting methods, leading to faster detection, more accurate analysis, and a proactive stance against emerging threats. Tools like ANY.RUN’s TI Lookup provide the necessary context and immediacy, transforming threat hunting from a reactive to a proactive discipline that significantly reduces organizational risk.