Critical SmarterMail Vulnerability Exploited Just Days After Patch Release
A significant security flaw in SmarterTools’ SmarterMail email software has been actively exploited in the wild, merely two days following the release of a patch intended to address the issue. This vulnerability, identified by watchTowr Labs as WT-2026-0001, was patched on January 15, 2026, with Build 9511, after being responsibly disclosed on January 8, 2026.
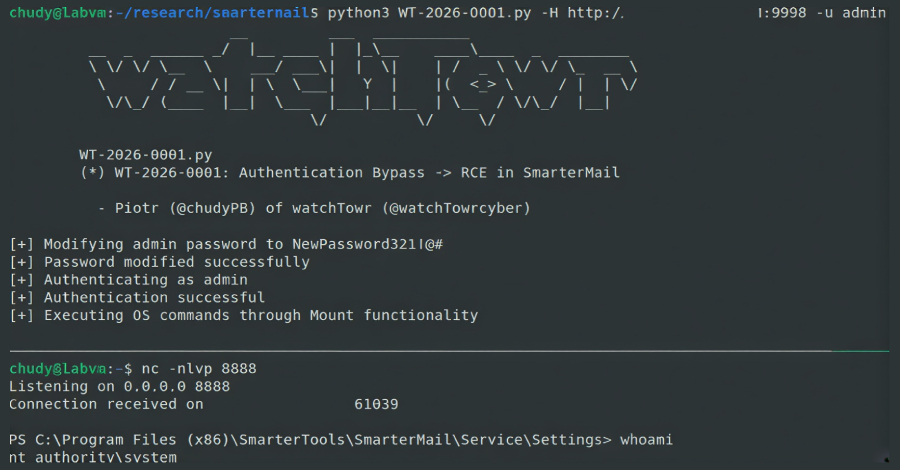
The flaw is an authentication bypass that allows any user to reset the system administrator’s password by sending a specially crafted HTTP request to the /api/v1/auth/force-reset-password endpoint. This vulnerability is particularly concerning because it enables attackers to execute operating system commands directly, leading to potential remote code execution (RCE).
Technical Details:
The vulnerability resides in the function SmarterMail.Web.Api.AuthenticationController.ForceResetPassword. This function permits unauthenticated access to the password reset endpoint and utilizes a boolean flag named IsSysAdmin to determine if the user is a system administrator. If this flag is set to true, the function:
1. Retrieves the configuration for the specified username.
2. Creates a new system administrator entry with the provided password.
3. Updates the administrator account with the new password.
This design flaw allows an attacker, who knows an existing administrator’s username, to reset the administrator’s password and gain elevated access.
Exploitation and Remote Code Execution:
Beyond unauthorized access, this vulnerability facilitates remote code execution. Once an attacker gains administrative privileges, they can exploit a feature that allows system administrators to execute operating system commands. By navigating to the Settings page, creating a new volume, and entering arbitrary commands in the Volume Mount Command field, these commands are executed by the host’s operating system, potentially granting the attacker a SYSTEM-level shell.
Incident Timeline:
– January 8, 2026: watchTowr Labs responsibly discloses the vulnerability to SmarterTools.
– January 15, 2026: SmarterTools releases Build 9511 to patch the vulnerability.
– January 17, 2026: Reports emerge of active exploitation, with attackers using the force-reset-password endpoint to change administrator passwords.
This rapid exploitation suggests that attackers quickly reverse-engineered the patch to identify and exploit the vulnerability.
Transparency and Communication Concerns:
SmarterTools’ release notes for Build 9511 vaguely mention IMPORTANT: Critical security fixes without detailing the specific issues addressed. This lack of transparency has raised concerns within the cybersecurity community. In response, SmarterTools CEO Tim Uzzanti indicated plans to improve communication by sending emails whenever a new CVE is discovered and when a build is released to resolve the issue.
Recommendations:
Given the severity of this vulnerability and its active exploitation, it is imperative for SmarterMail users to:
1. Update Immediately: Ensure that SmarterMail is updated to the latest version to mitigate this vulnerability.
2. Monitor Systems: Review system logs for any unauthorized access or unusual activities, especially related to password resets and command executions.
3. Enhance Security Measures: Implement additional security controls, such as multi-factor authentication and network segmentation, to limit potential attack vectors.
Staying vigilant and proactive is crucial in safeguarding systems against such vulnerabilities and potential exploits.