The SideWinder APT group, known for its long history of cyber-espionage, is expanding its operations beyond military and government targets. Recent reports indicate that the group is now actively targeting the maritime, nuclear, and IT sectors across South and Southeast Asia, the Middle East, and Africa.
New Targets and Attack Methods
Geographical Expansion
SideWinder has expanded its attacks to countries including Bangladesh, Cambodia, Djibouti, Egypt, the UAE, and Vietnam. These attacks are aimed at critical infrastructure, including nuclear power plants, maritime logistics, and IT service providers. The group has also been observed attacking real estate firms, telecommunications companies, consulting firms, and even hotel chains, indicating a broader strategic interest.
Spear-Phishing as the Primary Attack Vector
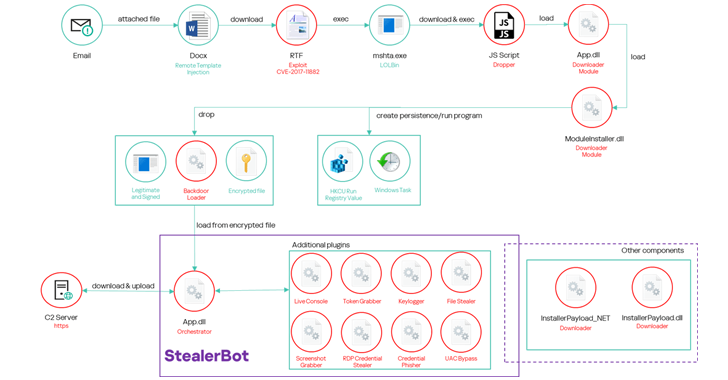
SideWinder continues to rely on spear-phishing emails to gain access to targeted systems. These emails often contain malicious DOCX attachments that use remote template injection to download a secondary RTF file, which exploits the CVE-2017-11882 vulnerability in Microsoft Office’s Equation Editor.
Once the vulnerability is triggered, the attackers execute a multi-stage infection chain, ultimately leading to the deployment of their StealerBot malware, a post-exploitation toolkit that enables remote control, data theft, and further infiltration.
Rapid Adaptation to Security Defenses
One of SideWinder’s key strengths is its ability to rapidly modify its malware in response to detection. Security researchers have observed instances where the group altered file names, changed execution paths, and modified persistence mechanisms within just five hours of a detection event. This high level of adaptability makes traditional signature-based security measures less effective against their attacks.
Why This Matters
The shift toward maritime and nuclear industries suggests that SideWinder is now focusing on disrupting critical infrastructure. This expansion could have significant geopolitical and economic consequences, particularly for nations that rely on maritime trade routes and nuclear energy.
How Organizations Can Protect Themselves
- Patch and Update Systems
Ensure that all software and operating systems are updated to eliminate vulnerabilities like CVE-2017-11882, which SideWinder exploits. - Strengthen Email Security
Implement advanced email filtering and sandboxing technologies to detect and block malicious attachments before they reach users. - User Awareness and Training
Train employees to identify spear-phishing attempts and avoid clicking on suspicious links or opening unknown attachments. - Monitor for Unusual Activity
Use behavioral analytics and intrusion detection systems to spot unusual activity that could indicate malware deployment or unauthorized access. - Develop a Strong Incident Response Plan
Ensure that your security teams have a clear incident response strategy to quickly identify, contain, and mitigate APT attacks before they escalate.