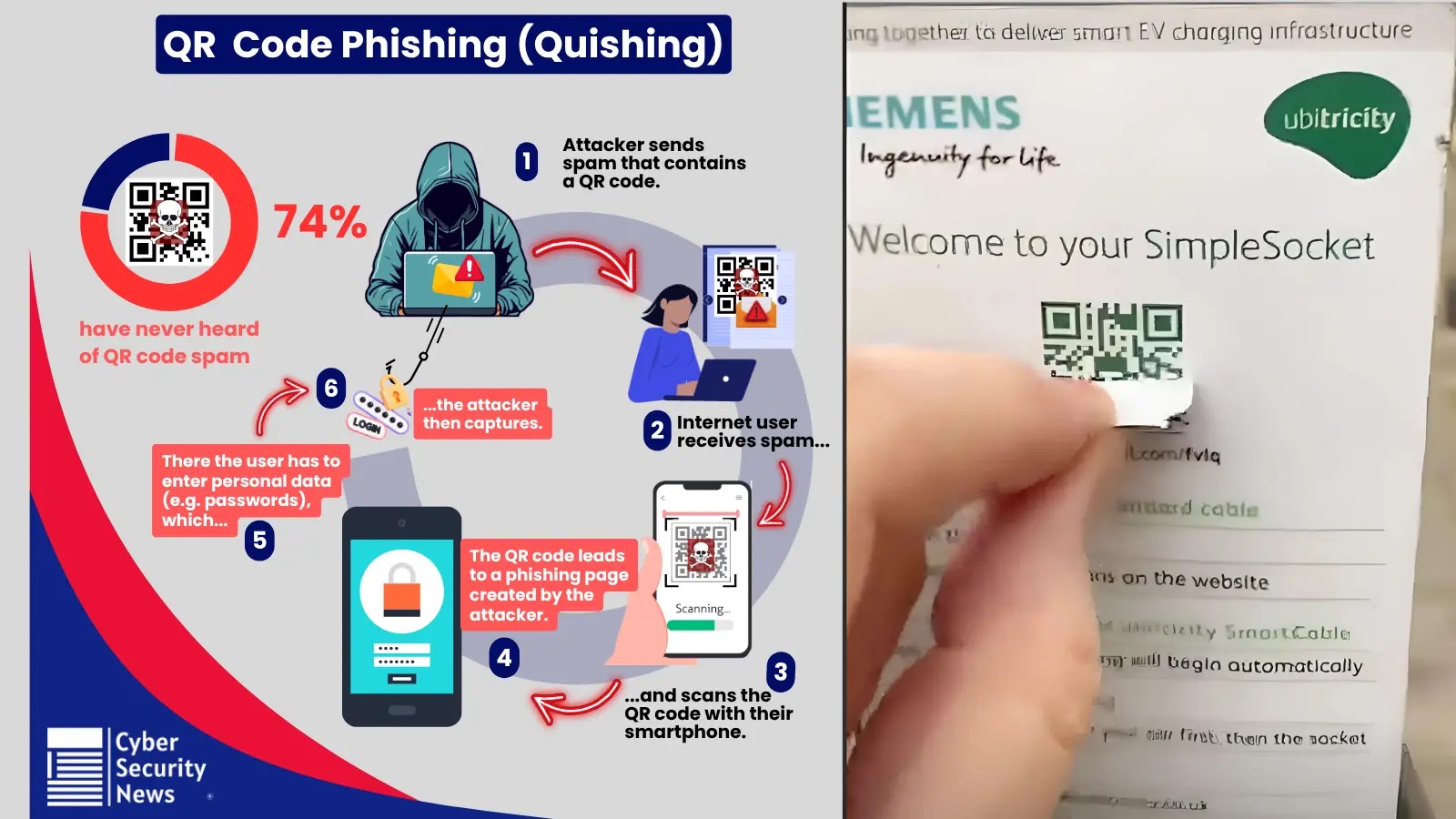
In recent years, QR codes have transitioned from being simple tools for quick information access to becoming sophisticated vectors for cyberattacks. This evolution has introduced a new form of phishing known as quishing, where malicious links are embedded within QR codes, making it challenging for traditional security measures to detect and mitigate these threats.
Understanding Quishing
Quishing, or QR code phishing, involves embedding harmful URLs within QR codes that, when scanned, redirect users to fraudulent websites designed to steal sensitive information or deploy malware. These attacks often target mobile devices, which may operate outside the protective perimeter of corporate networks, thereby evading standard security protocols.
Challenges in Detecting Quishing
Traditional security tools face significant hurdles in identifying quishing attempts due to several factors:
– Absence of Clickable Links: Since the malicious link is encapsulated within a QR code image, secure email gateways and URL filters lack direct access to analyze the link’s content.
– Lack of Obvious Indicators: Content inspection tools and heuristic engines may not recognize the embedded threat, as the QR code appears as a benign image without overt signs of malicious intent.
– Limited Telemetry: When users scan QR codes using personal mobile devices, these actions often occur outside the visibility of corporate monitoring systems, leaving security teams unaware of potential breaches.
The Role of Interactive Sandboxes in Mitigating Quishing
To effectively combat quishing, Security Operations Centers (SOCs) are increasingly turning to interactive sandbox environments like ANY.RUN. These platforms offer a controlled setting to safely analyze and decode QR codes, providing comprehensive insights into potential threats without exposing the organization to risk.
Advantages of Using Interactive Sandboxes
– Automated QR Code Detection and Decoding: The sandbox environment automatically identifies and deciphers QR codes embedded in various formats, such as emails, PDFs, and images, eliminating the need for manual extraction.
– Isolated Analysis Environment: By executing the decoded URLs within a virtual machine, the sandbox ensures that any malicious activity is contained, preventing it from affecting the actual network.
– Comprehensive Attack Context: Analysts gain a full view of the attack chain, including payload delivery mechanisms and network interactions, enabling a thorough understanding of the threat.
Case Study: Rapid Identification of a Voicemail Scam
Consider a scenario where an employee receives an email claiming a missed voicemail, accompanied by a QR code to listen to the message. By uploading this email to the ANY.RUN sandbox, the system automatically detects and decodes the QR code, revealing a malicious URL. Within approximately 60 seconds, the sandbox provides a detailed analysis, including:
– Identification of Malicious URL: The system displays the harmful link extracted from the QR code.
– Execution of Controlled Browser Session: The sandbox initiates a browser session to observe the behavior of the malicious site safely.
– Generation of Detailed Reports: Analysts receive structured reports outlining the attack’s tactics, techniques, and procedures (TTPs), along with indicators of compromise (IOCs) and network activity logs.
Benefits for SOC Analysts
Implementing interactive sandbox solutions like ANY.RUN offers several advantages for SOC teams:
– Accelerated Threat Detection: The sandbox can uncover hidden payloads and phishing schemes in under a minute, significantly reducing the time required for threat analysis.
– Unified Analytical Interface: Analysts have access to a consolidated view of process trees, network traffic, and decoded URLs, streamlining the investigative process.
– Automated Evidence Collection: Each analysis session generates exportable IOCs, network indicators, and visual evidence, facilitating efficient documentation and reporting.
– Enhanced Detection Engineering: Verified TTPs and IOCs can be directly transformed into new detection rules, bolstering the organization’s defensive capabilities.
– Secure Analysis Environment: All potentially harmful activities are confined within the sandbox’s virtual machine, ensuring that analysts remain protected while observing real-world attack behaviors.
– Collaborative Workflows: The platform supports sharing analysis sessions across teams and integration with existing security information and event management (SIEM), security orchestration, automation, and response (SOAR), or ticketing systems, enhancing collaborative incident response efforts.
Transforming Quishing Detection
Quishing attacks not only challenge an organization’s security defenses but also test the efficiency of its response mechanisms. By adopting interactive sandbox solutions, SOCs can shift from time-consuming manual decoding processes to rapid, automated validation of threats. This transition leads to:
– Increased Threat Identification: Organizations report identifying up to 58% more threats, including those that bypass conventional filters and static analysis methods.
– Faster Triage Processes: With automated IOC collection and ready-to-share reports, 94% of users experience accelerated triage times.
– Expedited Investigations: By connecting decoded URLs, network traffic, and threat behaviors within a single workflow, 95% of SOC teams enhance their investigative speed.
In conclusion, as quishing attacks become more prevalent and sophisticated, it is imperative for SOCs to adopt advanced tools like interactive sandboxes to effectively detect, analyze, and mitigate these threats, thereby safeguarding organizational assets and data.