Second Wave of Sha1-Hulud Attack Compromises Over 25,000 npm Repositories
A significant security breach has emerged within the npm ecosystem, as a second wave of the Sha1-Hulud attack has compromised over 25,000 repositories. This sophisticated supply chain attack, reminiscent of the Shai-Hulud incident from September 2025, has been identified by multiple security firms, including Aikido, HelixGuard, JFrog, Koi Security, ReversingLabs, SafeDep, Socket, Step Security, and Wiz. The malicious npm packages were uploaded between November 21 and 23, 2025, affecting popular packages from organizations such as Zapier, ENS Domains, PostHog, and Postman.
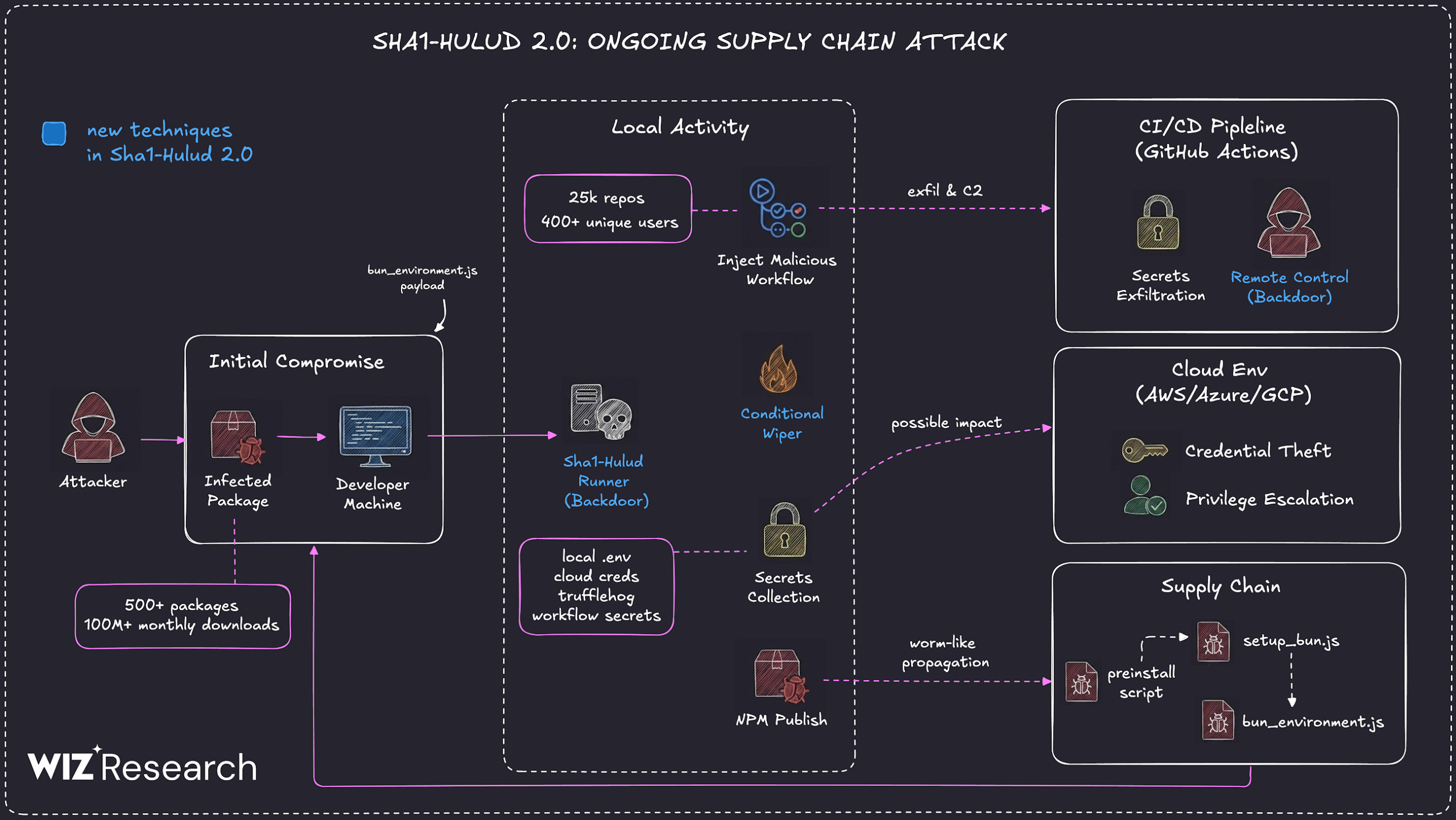
Wiz researchers Hila Ramati, Merav Bar, Gal Benmocha, and Gili Tikochinski highlighted the severity of this campaign, noting that it introduces a new variant that executes malicious code during the preinstall phase, significantly increasing potential exposure in build and runtime environments. This method allows the malware to infiltrate systems during the installation process, making detection and prevention more challenging.
Mechanism of the Attack:
The attackers have embedded a preinstall script named setup_bun.js within the package.json file of the compromised npm packages. This script is designed to stealthily install or locate the Bun runtime and subsequently execute a bundled malicious script called bun_environment.js. Upon execution, the malware performs the following actions:
1. Self-Hosted Runner Registration: The malware registers the infected machine as a self-hosted runner named SHA1HULUD and adds a workflow file (.github/workflows/discussion.yaml) containing an injection vulnerability. This setup allows the attacker to execute arbitrary commands on the infected machines by initiating discussions in the GitHub repository.
2. Credential Exfiltration: The malware exfiltrates all GitHub Actions secrets and uploads them as an artifact named actionsSecrets.json to exfiltration repositories. After downloading this file to the compromised machine, the workflow is deleted to conceal the malicious activity.
HelixGuard’s analysis revealed that the malware downloads and runs TruffleHog, a credential scanner, to search the local machine for sensitive information such as npm tokens, AWS, GCP, and Azure credentials, as well as environment variables.
Scope and Impact:
The automated replication associated with this campaign has led to a vast impact, affecting over 27,000 repositories across approximately 350 unique users. Notably, 1,000 new repositories were being added every 30 minutes during the peak of the attack. The malware is cross-platform, supporting Linux, macOS, and Windows systems, and facilitates cross-victim exfiltration, where one victim’s secrets are pushed to a public repository owned by another, unrelated victim. The exfiltrated data undergoes three layers of Base64 encoding before being uploaded, adding complexity to detection efforts.
Before executing its main payload, the malware searches public GitHub repositories for the beacon phrase Sha1-Hulud: The Second Coming. If found, it reads a stored file containing a GitHub access token, decodes it, and uses the recovered token as the main credential for exfiltration.
Comparative Analysis with Previous Attacks:
The original Shai-Hulud attack in September 2025 involved compromising legitimate npm packages to inject malicious code that searched developer machines for secrets using TruffleHog and transmitted them to an external server controlled by the attacker. These infected packages also had the capability to self-replicate by republishing themselves into other npm packages owned by the compromised maintainer.
In contrast, the current Sha1-Hulud campaign introduces a more aggressive approach by executing malicious code during the preinstall phase, thereby increasing potential exposure in both build and runtime environments. Additionally, the malware exhibits punitive behavior; if it fails to authenticate or establish persistence, it attempts to destroy the victim’s entire home directory, including every writable file owned by the current user under their home folder. This wiper-like functionality is triggered under specific conditions:
– Inability to authenticate to GitHub
– Failure to create a GitHub repository
– Inability to fetch a GitHub token
– Failure to find an npm token
Koi Security researchers Yuval Ronen and Idan Dardikman noted, In other words, if Sha1-Hulud is unable to steal credentials, obtain tokens, or secure any exfiltration channel, it defaults to catastrophic data destruction. This marks a significant escalation from the first wave, shifting the actor’s tactics from purely data-theft to punitive sabotage.
Mitigation Strategies:
To mitigate the risks posed by this threat, organizations are advised to:
– Scan Endpoints: Identify and remove any impacted packages from all endpoints.
– Credential Rotation: Immediately rotate all credentials to prevent unauthorized access.
– Repository Audits: Review repositories for persistence mechanisms by examining .github/workflows/ for suspicious files such as shai-hulud-workflow.yml or unexpected branches.
– Implement Security Measures: Enforce multi-factor authentication (MFA) for all developer accounts and monitor for anomalous network behavior.
This developing situation underscores the critical importance of vigilance and proactive security measures within the software development community to safeguard against increasingly sophisticated supply chain attacks.