Emerging Reynolds Ransomware Integrates BYOVD Tactics to Evade EDR Systems
Cybersecurity experts have recently identified a new ransomware variant named Reynolds, which uniquely incorporates a Bring Your Own Vulnerable Driver (BYOVD) strategy directly within its payload to circumvent Endpoint Detection and Response (EDR) mechanisms.
The BYOVD technique involves attackers exploiting legitimate drivers that contain known vulnerabilities to escalate privileges and disable security tools, thereby allowing malicious activities to proceed undetected. Historically, this method has been employed by various ransomware groups to enhance their attack efficacy.
Traditionally, the BYOVD component is deployed as a separate tool prior to the ransomware payload to neutralize security defenses. However, in the case of Reynolds, the vulnerable driver—specifically, the NsecSoft NSecKrnl driver—is embedded within the ransomware itself. This integration streamlines the attack process and reduces the likelihood of detection.
Broadcom’s cybersecurity teams have observed similar tactics in the past, notably in a Ryuk ransomware attack in 2020 and an incident involving the Obscura ransomware family in August 2025. In the Reynolds campaign, the ransomware deploys the compromised NSecKrnl driver to terminate processes associated with various security programs, including those from Avast, CrowdStrike Falcon, Palo Alto Networks Cortex XDR, Sophos (along with HitmanPro.Alert), and Symantec Endpoint Protection.
The NSecKrnl driver is known to be vulnerable due to a security flaw (CVE-2025-68947, CVSS score: 5.7) that allows for the termination of arbitrary processes. This vulnerability has previously been exploited by the threat actor Silver Fox to disable endpoint security tools before deploying the ValleyRAT malware.
Over the past year, Silver Fox has utilized multiple legitimate but flawed drivers, such as truesight.sys and amsdk.sys, in BYOVD attacks to disable security programs. By integrating defense evasion and ransomware capabilities into a single component, Reynolds complicates detection and mitigation efforts, eliminating the need for attackers to deploy separate tools for each function.
Notably, a suspicious side-loaded loader was detected on the target’s network several weeks prior to the deployment of the Reynolds ransomware. Additionally, the GotoHTTP remote access program was installed a day after the ransomware attack, suggesting that the attackers aimed to maintain persistent access to the compromised systems.
The BYOVD approach is favored by attackers due to its effectiveness and reliance on legitimate, signed files, which are less likely to trigger security alerts. Embedding the defense evasion component within the ransomware payload allows for a more discreet attack, as no separate external files are dropped on the victim’s network.
This development coincides with several recent ransomware-related incidents:
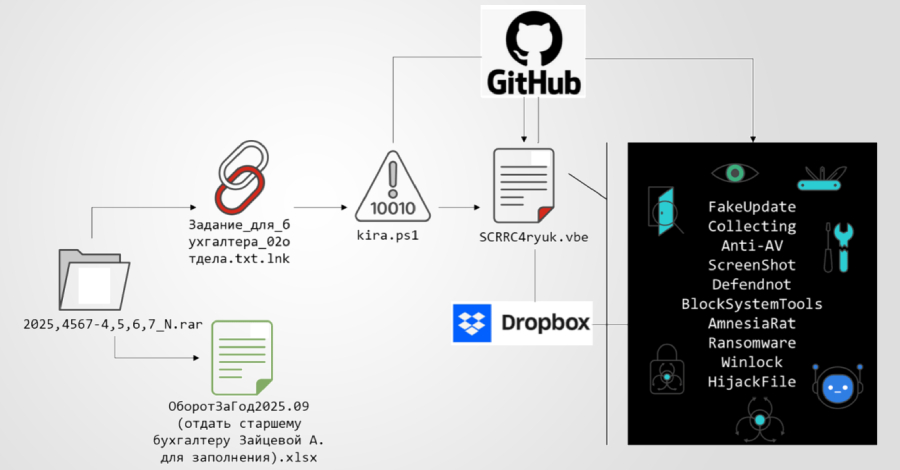
– A high-volume phishing campaign utilized emails with Windows shortcut (LNK) attachments to execute PowerShell code that downloads a Phorpiex dropper, subsequently delivering the GLOBAL GROUP ransomware. This ransomware operates entirely on the compromised system, making it compatible with air-gapped environments and does not involve data exfiltration.
– The WantToCry group exploited virtual machines provisioned by ISPsystem, a legitimate virtual infrastructure management provider, to host and distribute malicious payloads at scale.
– Ransomware operators have increasingly targeted cloud storage services, particularly misconfigured Amazon Web Services (AWS) S3 buckets. These attacks leverage native cloud features to delete or overwrite data, suspend access, or extract sensitive content while remaining undetected.
According to data from Cyble, GLOBAL GROUP is among several ransomware groups that emerged in 2025, including Devman, DireWolf, NOVA, J group, Warlock, BEAST, Sinobi, NightSpire, and The Gentlemen. In the fourth quarter of 2025, Sinobi’s data leak site listings increased by 306%, making it the third-most active ransomware group after Qilin and Akira, as reported by ReliaQuest.
The resurgence of LockBit 5.0 was a significant development in the fourth quarter, marked by a late-quarter surge that saw the group list 110 organizations in December alone. This activity indicates a group capable of rapidly scaling operations, converting intrusions into impactful attacks, and maintaining an affiliate network capable of operating at high volumes.
The emergence of new ransomware groups, coupled with collaborations between existing ones, has led to a spike in ransomware activity. Ransomware actors claimed a total of 4,737 attacks during 2025, up from 4,701 in 2024. Attacks that do not involve encryption and rely solely on data theft to exert pressure reached 6,182 during the same period, a 23% increase from 2024.
The average ransom payment in the fourth quarter of 2025 was $591,988, a 57% increase from the third quarter, driven by a small number of large settlements. Coveware’s quarterly report suggests that threat actors may return to data encryption tactics to more effectively leverage ransoms from victims.