Unveiling APT-C-35’s Stealth Tactics: Apache HTTP Response Indicators as Detection Tools
In the ever-evolving landscape of cyber threats, the Advanced Persistent Threat group APT-C-35, also known as DoNot, has maintained a persistent presence, particularly targeting regions in South Asia. Recent analyses have shed light on the group’s infrastructure, revealing unique Apache HTTP response characteristics that can serve as critical indicators for detection and monitoring.
Background on APT-C-35
APT-C-35 is an India-based threat actor recognized for its state-sponsored cyber espionage activities. The group has a history of targeting government, defense, and diplomatic sectors, employing sophisticated methods to infiltrate and exfiltrate sensitive information. Their operations are characterized by a consistent and methodical approach, making them a significant concern for cybersecurity professionals.
Discovery of Unique Infrastructure Indicators
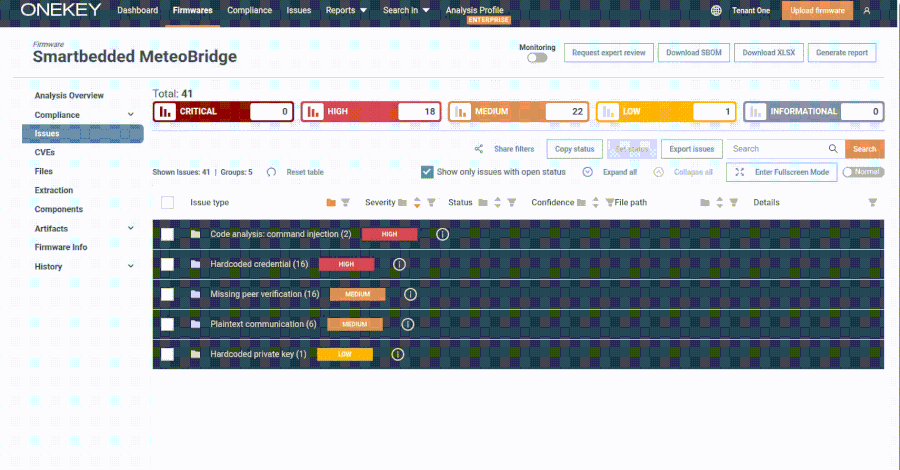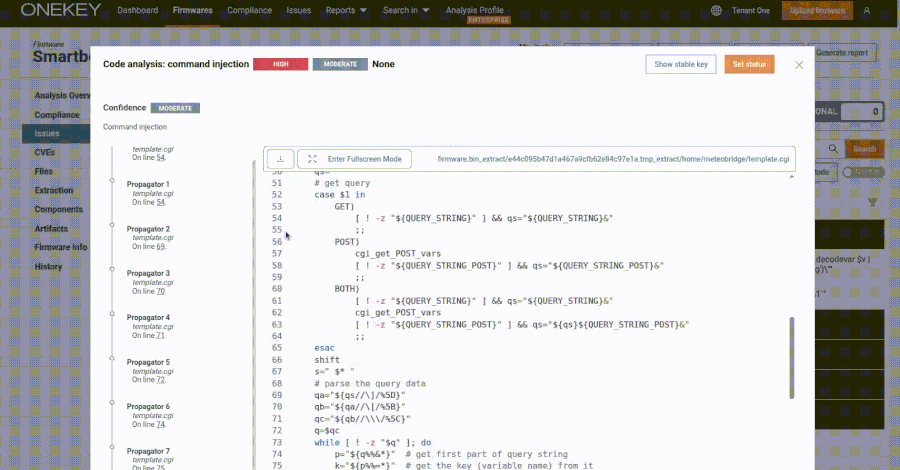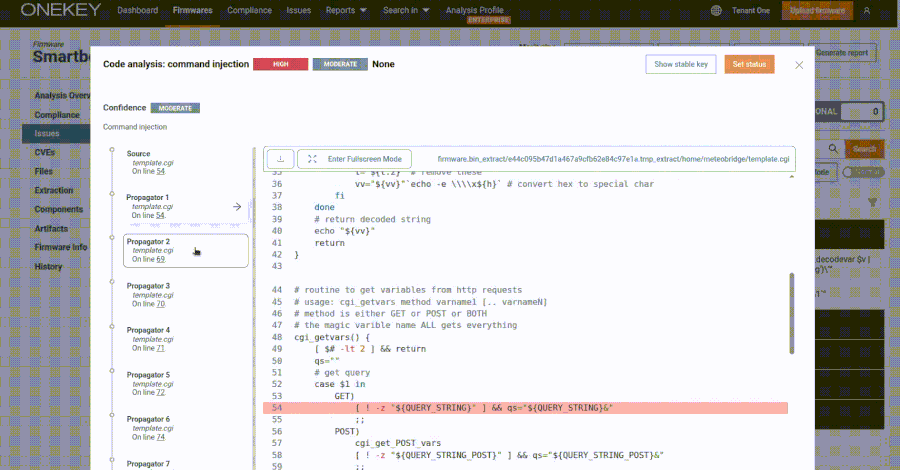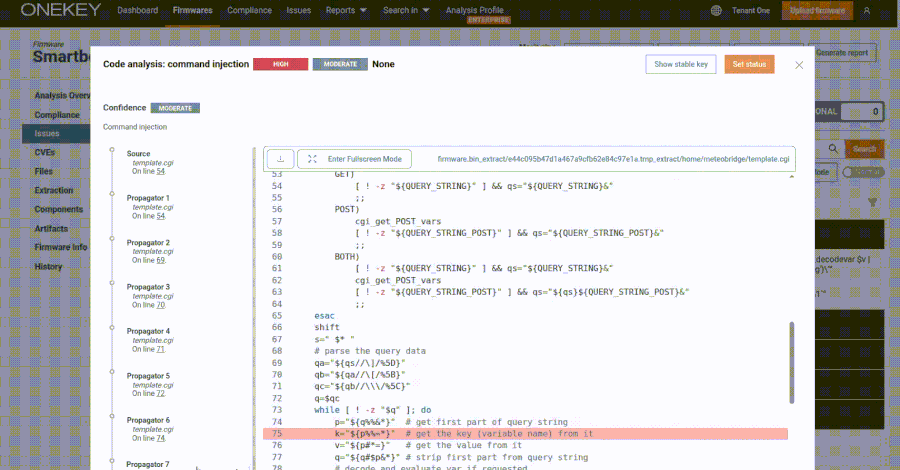
Security researchers have identified specific technical markers within APT-C-35’s web servers that distinguish them from legitimate servers. These markers are primarily found in the HTTP response headers of the group’s infrastructure. By analyzing these unique characteristics, security teams can effectively track and monitor APT-C-35’s activities.
Methodology for Detection
The detection process involves a structured analysis of Apache HTTP response headers combined with an examination of Autonomous System Number (ASN) 399629. Researchers discovered that servers associated with APT-C-35 consistently returned specific HTTP headers, including standardized expiration dates and content-length values. For instance, HTTP responses with Expires: Thu, 19 Nov 1981 08:52:00 GMT paired with HTTP/1.1 200 OK status codes were prevalent across ASN 399629.
Key Findings
– Infrastructure Clusters: Approximately 73 results representing 36 unique IP addresses were identified within the infrastructure cluster.
– Primary Server Identification: The server gilbertfix.info, hosted on IP 149.248.76.43 in Wyoming, exhibited typical cache control headers such as Cache-Control: no-store, no-cache, must-revalidate.
– Defensive Measures: The identified headers suggest that the infrastructure is designed to prevent caching, thereby securing sensitive communications and evading detection.
Implications for Cybersecurity
The identification of these unique HTTP response indicators provides cybersecurity teams with valuable tools for proactive threat detection. By monitoring for these specific patterns, organizations can correlate network indicators of compromise with known APT-C-35 infrastructure, thereby accelerating incident response times and improving the accuracy of threat characterization.
Conclusion
The continuous monitoring and analysis of threat actor infrastructure are paramount in the fight against cyber espionage. The recent findings on APT-C-35’s use of specific Apache HTTP response indicators underscore the importance of detailed technical analysis in uncovering and mitigating advanced persistent threats.