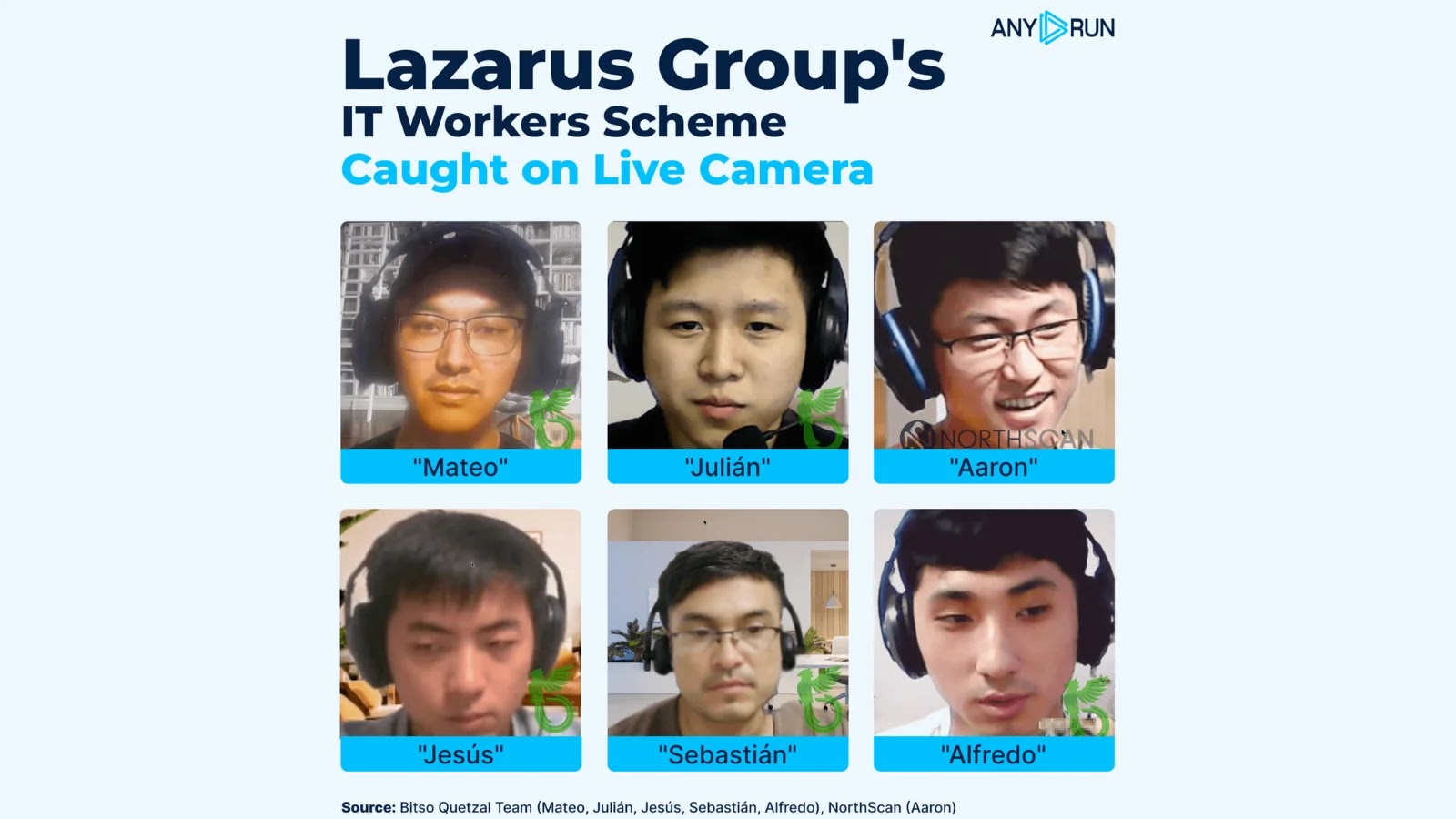
Unmasking the Lazarus Group’s IT Worker Deception: A Live Surveillance Breakthrough
In a groundbreaking investigation, cybersecurity researchers have unveiled the intricate tactics employed by North Korea’s infamous Lazarus Group, specifically its Chollima unit, to infiltrate Western financial and cryptocurrency sectors. By setting up sophisticated virtual environments, the researchers captured live operations of the group’s remote IT worker scheme, shedding light on their methods of identity theft and covert integration into targeted organizations.
The Deceptive Recruitment Process
The operation commenced when Heiner García of NorthScan posed as a U.S.-based developer who had been approached on GitHub by a recruiter using the aliases Aaron and Blaze. This recruiter was promoting a job hunting business and sought individuals willing to front technical interviews. In exchange for a portion of the salary, the recruiter requested full access to the individual’s laptop, Social Security Number, bank accounts, and identity documents, assuring that his team of developers would handle the actual work behind the scenes.
This approach aligns with a broader pattern observed in the Chollima unit’s operations, where North Korean operatives either steal resumes outright or persuade junior engineers to rent their identities. This strategy enables North Korean personnel to clandestinely embed themselves within U.S. finance, cryptocurrency, healthcare, and even civil engineering firms.
Setting the Trap: Virtual Surveillance Environments
Instead of providing real machines, Mauro Eldritch of BCA LTD, in collaboration with sandbox provider ANY.RUN, established a laptop farm consisting of extended-runtime virtual machines. Each virtual machine was meticulously crafted to resemble a heavily used developer notebook based in the United States.
These analysis environments operated on Windows 10 and 11, featuring realistic usage histories, pre-installed Integrated Development Environments (IDEs), and browser profiles. They were routed through U.S. residential proxies to meet the recruiters’ requirement for American-based talent. This setup allowed the research team to monitor live screens, file operations, and network flows. Additionally, they could induce system crashes, revert to restore points, and cut internet access to contain the operators and prevent them from pivoting to real targets.
Live Capture of Lazarus Group’s Operations
Upon receiving AnyDesk details and a pre-agreed password, the recruiter, Blaze, connected to the fake laptops. He promptly executed tools like DxDiag and systeminfo to verify hardware specifications and checked the browser for location data to confirm the host appeared to be in the U.S. Traffic analysis revealed connections originating from IP addresses associated with Astrill VPN, a service previously linked to Lazarus Group activities, highlighting the group’s reliance on consumer VPN endpoints to obscure their origins.
As the researchers induced system crashes and network disruptions, Blaze left pleading messages for the persona Andy, enlisted a colleague known as Assassin, and spent considerable time trapped in CAPTCHA loops and failed logins, all while his actions were meticulously recorded.
Insights into the Chollima Unit’s Toolkit
When Blaze synchronized his Chrome profile, the investigators gained unprecedented visibility into the Chollima unit’s toolkit, which heavily relies on AI-driven job automation tools rather than custom malware. The installed extensions included:
– Simplify Copilot, AiApply, and Final Round AI: These tools automate job applications and generate real-time interview responses.
– OTP.ee and Authenticator.cc: These extensions capture and replay one-time passwords after stealing or renting a victim’s identity.
Additionally, Blaze deployed Google Remote Desktop via PowerShell with a fixed PIN, layering it on top of AnyDesk. This setup provided his team with persistent access to employee laptops, a method nearly indistinguishable from standard remote-work tools to unsuspecting employers.
Contextualizing the Findings
This operation occurs amid sustained U.S. law enforcement efforts to dismantle North Korea’s remote IT worker schemes. In June 2025, a case detailed over 100 infiltrated companies, more than 80 stolen U.S. identities, and searches of numerous physical laptop farms on American soil. Subsequent actions in late 2025 sought over $15 million in penalties related to these activities.
The Lazarus Group’s tactics are not isolated incidents. They have a history of exploiting professional networks and software repositories to achieve their objectives. For instance, the group has been known to target organizations through LinkedIn recruiting scams, aiming to capture credentials and deliver malware. These operations often involve enticing job offers in decentralized cryptocurrency exchanges, luring individuals into downloading malicious code. ([cybersecuritynews.com](https://cybersecuritynews.com/beware-of-lazarus-linkedin-recruiting-scam/?utm_source=openai))
Furthermore, the Lazarus Group has expanded its cyber warfare tactics by introducing malicious npm packages with advanced obfuscation techniques. These packages are designed to evade detection systems and manual code audits, marking a significant evolution in the group’s approach to cyber espionage and financial theft. ([cybersecuritynews.com](https://cybersecuritynews.com/lazarus-adds-new-malicious-npm-packages/?utm_source=openai))
The group’s activities also include exploiting vulnerabilities in widely used software. For example, they have been observed exploiting flaws in ManageEngine to deploy malware, targeting critical infrastructure and healthcare sectors. ([cybersecuritynews.com](https://cybersecuritynews.com/lazarus-exploiting-manageengine/?utm_source=openai))
Implications and Recommendations
The Lazarus Group’s sophisticated infiltration tactics underscore the critical need for organizations to implement robust cybersecurity measures. Employers should exercise heightened vigilance during the hiring process, especially when engaging with remote candidates. Verifying the authenticity of applicants and being cautious of unsolicited job offers can mitigate the risk of infiltration.
Additionally, organizations should monitor for unusual remote access patterns and implement multi-factor authentication to enhance security. Regular audits of remote access tools and protocols can help identify and address potential vulnerabilities.
By understanding and anticipating the evolving tactics of groups like Lazarus, organizations can better protect themselves against sophisticated cyber threats.