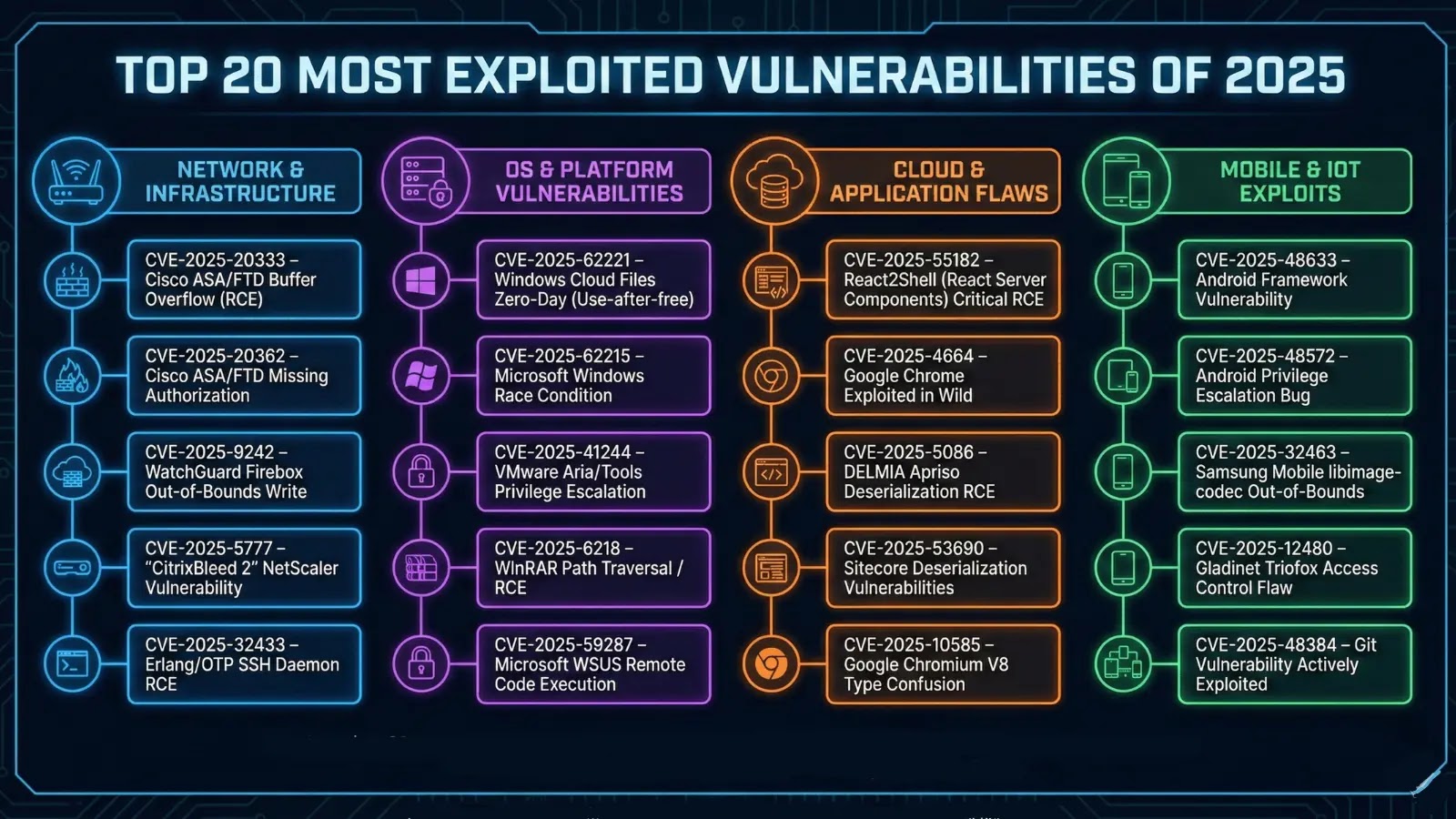
Top 20 Most Exploited Vulnerabilities of 2025: A Comprehensive Analysis
In 2025, the cybersecurity landscape witnessed an unprecedented surge in the exploitation of vulnerabilities, with threat actors targeting critical flaws across enterprise software, cloud infrastructure, and industrial systems. This analysis delves into the twenty most dangerous vulnerabilities exploited during the year, highlighting their technical details, exploitation methods, and the imperative for organizations to prioritize patching and defense strategies.
1. React2Shell – React Server Components Remote Code Execution (CVE-2025-55182)
– CVSS v3.1 Score: 10.0 (Critical)
– Affected Product: React Server Components (Meta)
– Vulnerability Type: Deserialization / Unauthenticated RCE
– Authentication Required: No (Unauthenticated)
– Active Exploitation: Yes – Mesh Agent Malware, Cryptocurrency Miners
– Disclosure Date: December 3, 2025
– CISA KEV Status: Added December 2025
– Primary Attack Vector: Network / Web Application
This critical vulnerability in React Server Components allows unauthenticated remote code execution through deserialization flaws. Exploited by threat actors to deploy Mesh Agent malware and cryptocurrency miners, it underscores the necessity for immediate patching and vigilant monitoring of web applications.
2. Windows Cloud Files Mini Filter Driver Use-After-Free (CVE-2025-62221)
– CVSS v3.1 Score: 7.8 (High)
– Affected Product: Windows Cloud Files Mini Filter Driver
– Vulnerability Type: Use-After-Free / Memory Corruption
– Authentication Required: Yes (Authenticated Local)
– Active Exploitation: Yes – Patch Tuesday December 2025
– Disclosure Date: December 9, 2025
– CISA KEV Status: Added December 2025
– Primary Attack Vector: Local System Access
This vulnerability involves a use-after-free condition in the Windows Cloud Files Mini Filter Driver, leading to memory corruption. Exploited locally by authenticated users, it emphasizes the importance of applying Microsoft’s Patch Tuesday updates promptly to mitigate potential privilege escalation attacks.
3. WinRAR Path Traversal Remote Code Execution (CVE-2025-6218)
– CVSS v3.1 Score: 7.8 (High)
– Affected Product: WinRAR 7.11 and earlier
– Vulnerability Type: Path Traversal / Arbitrary File Extraction
– Authentication Required: No (Unauthenticated – Archive File)
– Active Exploitation: Yes – APT-C-08, GOFFEE, Bitter Groups
– Disclosure Date: March 2025 / June 2025 Patch
– CISA KEV Status: Added December 2025
– Primary Attack Vector: User Interaction (Archive File)
A path traversal flaw in WinRAR versions 7.11 and earlier allows attackers to execute arbitrary code by tricking users into opening malicious archive files. Exploited by advanced persistent threat groups, this vulnerability highlights the need for caution when handling untrusted archives and the importance of keeping software updated.
4. Android Framework Information Disclosure (CVE-2025-48633)
– CVSS v3.1 Score: High (Not Specified)
– Affected Product: Android 13-16 Framework
– Vulnerability Type: Information Disclosure / Sandbox Bypass
– Authentication Required: No (Malicious App)
– Active Exploitation: Yes – State Actors (Limited Targeted)
– Disclosure Date: December 2, 2025
– CISA KEV Status: Added December 2025
– Primary Attack Vector: Mobile Application / Malicious App
This vulnerability in the Android framework allows malicious applications to bypass sandbox protections, leading to unauthorized information disclosure. Exploited by state actors in targeted attacks, it underscores the necessity for users to download apps only from trusted sources and for developers to adhere to secure coding practices.
5. Android Framework Privilege Escalation (CVE-2025-48572)
– CVSS v3.1 Score: High (Not Specified)
– Affected Product: Android 13-16 Framework
– Vulnerability Type: Privilege Escalation / Unauthorized Activity
– Authentication Required: No (Malicious App)
– Active Exploitation: Yes – State Actors (Limited Targeted)
– Disclosure Date: December 2, 2025
– CISA KEV Status: Added December 2025
– Primary Attack Vector: Mobile Application / Malicious App
Similar to CVE-2025-48633, this flaw allows malicious apps to escalate privileges, enabling unauthorized activities on affected devices. The exploitation by state actors highlights the critical need for robust app vetting processes and timely security updates for mobile devices.
6. CitrixBleed 2 – Citrix NetScaler Memory Disclosure (CVE-2025-5777)
– CVSS v3.1 Score: 9.3 (Critical)
– Affected Product: Citrix NetScaler ADC/Gateway
– Vulnerability Type: Out-of-Bounds Read / Session Hijacking
– Authentication Required: No (Unauthenticated)
– Active Exploitation: Yes – RansomHub, Multiple Threat Groups
– Disclosure Date: June 17, 2025
– CISA KEV Status: Added July 2025 (24-hr deadline)
– Primary Attack Vector: Network / VPN Gateway
This critical vulnerability in Citrix NetScaler allows unauthenticated attackers to read out-of-bounds memory, potentially leading to session hijacking. Exploited by multiple threat groups, it emphasizes the importance of securing VPN gateways and applying patches without delay.
7. Git Arbitrary File Write on Non-Windows Systems (CVE-2025-48384)
– CVSS v3.1 Score: 8.0-8.1 (High)
– Affected Product: Git on macOS and Linux
– Vulnerability Type: Arbitrary File Write / Git Hook Execution
– Authentication Required: No (Unauthenticated – Repository Clone)
– Active Exploitation: Yes – Sophisticated Social Engineering
– Disclosure Date: July 8, 2025
– CISA KEV Status: Added August 2025
– Primary Attack Vector: Network / Git Repository
This vulnerability allows attackers to write arbitrary files on non-Windows systems by exploiting Git repository clones. Leveraged through sophisticated social engineering tactics, it highlights the need for caution when interacting with untrusted repositories and the importance of verifying sources.
8. VMware Aria Tools Local Privilege Escalation (CVE-2025-41244)
– CVSS v3.1 Score: 7.8 (High)
– Affected Product: VMware Aria Operations, VMware Tools
– Vulnerability Type: Untrusted Search Path / Local Privilege Escalation
– Authentication Required: Yes (Local User)
– Active Exploitation: Yes – State Actor UNC5174 (Chinese APT)
– Disclosure Date: September 29, 2025
– CISA KEV Status: State Actor Exploitation (Not KEV)
– Primary Attack Vector: Local System Access
This flaw in VMware Aria Tools allows local users to escalate privileges through untrusted search path vulnerabilities. Exploited by state actors, it underscores
Article X Post:
Hashtags:
Article Key Phrase:
Category: Security News