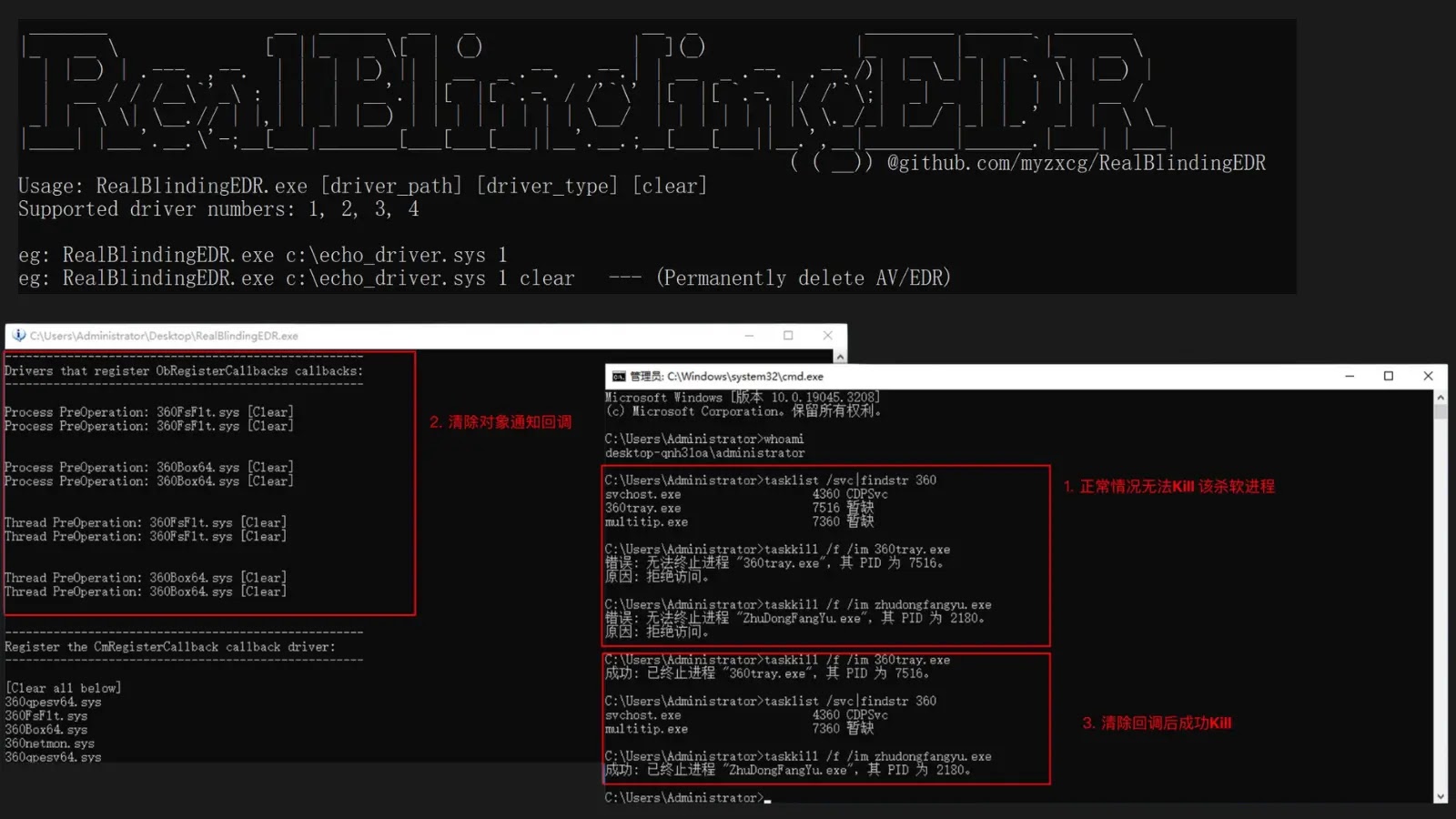
In late 2023, a tool named RealBlindingEDR emerged on GitHub, offering the capability to disable antivirus (AV) and endpoint detection and response (EDR) systems on Windows platforms by manipulating kernel callbacks. This open-source utility has since been co-opted by cybercriminal groups, notably the ransomware collective Crypto24, to neutralize security defenses during their attacks.
Understanding RealBlindingEDR’s Functionality
RealBlindingEDR operates by exploiting signed drivers to perform arbitrary memory read and write operations, effectively bypassing Windows’ Kernel Patch Protection, commonly known as PatchGuard. By targeting six primary kernel callback types, the tool can:
– Monitor process creation
– Track thread activity
– Oversee image loading
– Observe registry modifications
– Supervise file operations
– Manage object handles
By clearing these callbacks, RealBlindingEDR effectively blinds security software, rendering it incapable of detecting or responding to malicious activities.
Technical Mechanisms and Deployment
The tool leverages vulnerable drivers, such as `echo_driver.sys` or `dbutil_2_3.sys`, to gain kernel-level access without immediate detection. Users can execute commands like `RealBlindingEDR.exe c:\echo_driver.sys 1` to initiate blinding mode or other variants for different operations. Demonstrations have shown the tool’s ability to remove callbacks in real-time, allowing actions like file deletions and process terminations that AV tools would typically block.
RealBlindingEDR systematically erases callbacks registered via functions such as:
– `CmRegisterCallback(Ex)`
– `ObRegisterCallbacks`
– `PsSetCreateProcessNotifyRoutine(Ex)`
– `PsSetCreateThreadNotifyRoutine(Ex)`
– `PsSetLoadImageNotifyRoutine(Ex)`
– MiniFilter drivers
These mechanisms allow AV/EDR solutions to monitor various system activities. For instance, removing `ObRegisterCallbacks` eliminates handle protection, enabling users with administrative privileges to terminate EDR processes that would otherwise resist termination.
Implications for Cybersecurity
While RealBlindingEDR was ostensibly developed for research purposes, its adoption by malicious actors like the Crypto24 ransomware group underscores its potential for misuse. By integrating this tool into their attack strategies, these groups can impair security defenses before deploying ransomware, increasing the likelihood of successful infections.
Recommendations for Mitigation
To counteract the threats posed by tools like RealBlindingEDR, organizations should consider the following measures:
1. Monitor for Vulnerable Driver Loads: Regularly inspect systems for the presence of known vulnerable drivers that could be exploited to gain kernel-level access.
2. Implement Advanced EDR Solutions: Deploy endpoint detection and response systems equipped with behavioral analytics to detect anomalies indicative of kernel-level manipulations.
3. Enforce Driver Signature Policies: Utilize tools like Driver Signature Enforcement Overrider to ensure that only trusted drivers are loaded, reducing the risk of exploitation.
4. Review Endpoint Logs: Conduct regular audits of endpoint logs to identify unusual access patterns to system files, which may indicate attempts to disable security mechanisms.
5. Adopt Least-Privilege Principles: Limit administrative privileges to essential personnel and processes, minimizing the potential impact of compromised accounts.
By proactively implementing these strategies, organizations can enhance their resilience against sophisticated threats that seek to disable security defenses through kernel-level exploits.