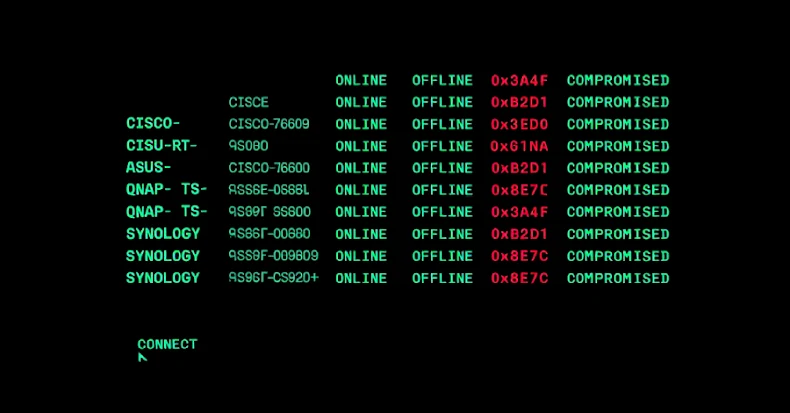
A sophisticated malware campaign known as PolarEdge has been actively targeting edge devices from major manufacturers, including Cisco, ASUS, QNAP, and Synology, since late 2023. This campaign aims to incorporate these devices into a botnet, exploiting critical vulnerabilities to gain unauthorized access and control.
Exploitation of CVE-2023-20118
Central to the PolarEdge campaign is the exploitation of CVE-2023-20118, a critical security flaw in Cisco Small Business routers. This vulnerability allows attackers to execute arbitrary commands on affected devices. Notably, these routers have reached their end-of-life status and no longer receive security updates, leaving them particularly susceptible to such attacks. Cisco has recommended mitigating this flaw by disabling remote management and blocking specific ports; however, many devices remain unpatched and vulnerable.
Deployment of the PolarEdge Backdoor
Upon successful exploitation of the vulnerability, attackers deploy a previously undocumented implant—a TLS backdoor—onto the compromised device. This backdoor is delivered through a shell script named q, which is downloaded via FTP. Once executed, the backdoor enables attackers to perform various malicious actions, including:
– Log File Manipulation: Cleaning up log files to remove traces of the attack.
– Process Termination: Ending suspicious processes that might detect or interfere with the malware.
– Payload Download and Execution: Retrieving and executing additional malicious payloads, such as a binary named cipher_log.
– Establishing Persistence: Modifying system startup scripts to ensure the backdoor runs upon device reboot.
The backdoor operates by entering an infinite loop, establishing a TLS session, and spawning child processes to manage incoming client connections and execute commands. It communicates with a command-and-control (C2) server, reporting successful infections and transmitting device details like IP addresses and port pairings.
Targeting Multiple Manufacturers
While initial reports focused on Cisco devices, further analysis has revealed that PolarEdge also targets devices from ASUS, QNAP, and Synology. These devices are infected through similar methods, with the payloads traced to an IP address hosted on Huawei Cloud. The botnet has compromised over 2,000 unique IP addresses worldwide, with infections reported across multiple countries, including the United States, Russia, Taiwan, and Brazil.
Technical Analysis of the Backdoor
The PolarEdge backdoor is a 64-bit ELF executable, statically linked and stripped of debugging symbols, indicating an intent to resist analysis. It functions as a custom TLS server, implemented using mbedTLS v2.8.0, capable of receiving commands and executing them directly on the infected host. The backdoor’s primary function is to send a host fingerprint to its C2 server and then listen for commands over the built-in TLS server.
Upon startup, the backdoor performs filesystem manipulation, such as moving and deleting certain files, likely to prevent other threat actors from accessing the systems with the same vulnerabilities. It also employs various anti-analysis techniques, including process name randomization and obfuscation of ELF section names, to evade detection.
Notably, while the backdoor does not maintain persistence after a reboot, it spawns a child watchdog process that checks every 30 seconds whether the parent process still exists. If the parent process has terminated, the child process executes a shell command to relaunch the backdoor, ensuring continued operation.
Potential Implications and Threats
The exact purpose of the PolarEdge botnet remains unclear. However, researchers speculate that it could be used to control compromised devices for launching larger-scale cyberattacks, such as distributed denial-of-service (DDoS) attacks. The complexity of PolarEdge and its ability to exploit various vulnerabilities across different systems demonstrate the sophistication of the operation. The malware’s deployment and persistence mechanisms highlight the advanced skills of the attackers behind it, suggesting a well-organized cybercrime group.
The widespread infections underscore the significant risks faced by edge devices, especially those that are no longer receiving security updates. This operation serves as a warning of the increasing threats targeting vulnerable devices globally.
Mitigation and Recommendations
To protect against threats like PolarEdge, it is crucial for organizations and individuals to:
– Apply Security Updates: Regularly update device firmware and software to patch known vulnerabilities.
– Disable Unnecessary Services: Turn off remote management features if they are not essential.
– Implement Network Segmentation: Isolate critical devices from the internet and untrusted networks.
– Monitor Network Traffic: Regularly inspect network logs for unusual activities that may indicate compromise.
– Replace End-of-Life Devices: Consider upgrading devices that no longer receive security updates to ensure continued protection.
By taking these proactive measures, users can reduce the risk of their devices being compromised by malware campaigns like PolarEdge.