A newly identified security vulnerability, termed Pixnapping, poses a significant risk to Android devices by enabling malicious applications to covertly extract sensitive on-screen information. This includes two-factor authentication (2FA) codes, private messages, and other confidential data, all without requiring special permissions or alerting the user.
Understanding Pixnapping
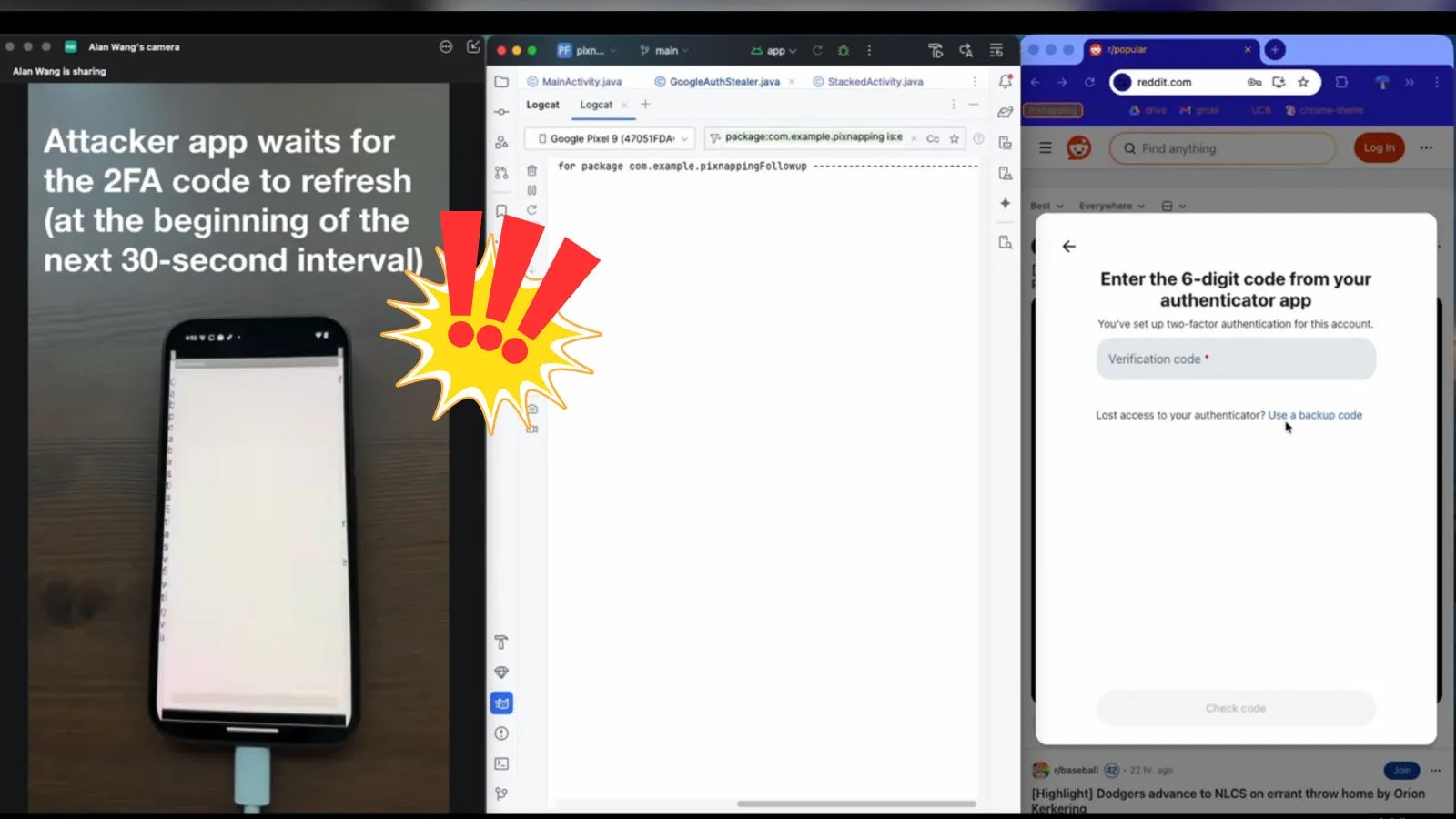
Pixnapping is a side-channel attack that exploits Android’s core application programming interfaces (APIs) and inherent hardware vulnerabilities in graphics processing units (GPUs). By leveraging these weaknesses, a malicious app can reconstruct on-screen content pixel by pixel, effectively capturing information displayed by other applications. This method allows attackers to access data such as 2FA codes from Google Authenticator in under 30 seconds, as well as messages from secure communication apps like Signal.
Mechanism of the Attack
The attack initiates when a user unknowingly installs a malicious application. This app doesn’t require any special permissions, making it difficult to detect during installation. Once installed, the app employs Android’s intent system to launch the target application, such as Google Authenticator. It then overlays semi-transparent windows over specific screen areas to isolate and manipulate individual pixels.
By applying graphical operations like blur effects through Android’s SurfaceFlinger, the attack induces timing variations in the rendering process. These variations, influenced by the GPU’s data compression behavior (known as GPU.zip), allow the malicious app to infer pixel colors based on rendering delays. This process is repeated across the screen to reconstruct the displayed content without the user’s knowledge.
Demonstrated Impact
Researchers have successfully demonstrated Pixnapping on devices including Google Pixel models 6 through 9 and the Samsung Galaxy S25, running Android versions 13 to 16. The attack has been used to extract sensitive data from widely used applications and services, such as:
– Google Authenticator: Retrieving 2FA codes in under 30 seconds.
– Signal: Accessing private messages.
– Venmo: Obtaining transaction details.
– Gmail: Reading email content.
– Google Maps: Viewing location histories.
This broad applicability underscores the severity of the vulnerability, as it affects both native applications and web content accessed through Android browsers.
Technical Details
The Pixnapping attack comprises several key steps:
1. Invocation of Target Application: The malicious app uses Android intents to launch the target application, bringing sensitive information into the rendering pipeline.
2. Overlay and Pixel Isolation: It overlays semi-transparent activities over specific screen regions to isolate pixels of interest.
3. Induction of Graphical Operations: The app applies graphical effects, such as blur, to these pixels, inducing rendering operations.
4. Measurement of Rendering Time: By measuring the time taken to render these operations, the app infers pixel colors, as rendering time varies with pixel content due to GPU compression behaviors.
5. Reconstruction of Content: This process is repeated across the screen, allowing the app to reconstruct the entire displayed content.
This method effectively bypasses Android’s security model, which traditionally prevents apps from accessing each other’s data without explicit permissions.
Response and Mitigation Efforts
The research team disclosed the Pixnapping vulnerability to Google in February 2025. Google assigned it a high-severity rating (CVE-2025-48561) and released a partial patch in September 2025. However, researchers identified a workaround that bypasses this patch, prompting Google to plan an additional fix in the December 2025 Android security bulletin.
As of October 2025, no evidence suggests that Pixnapping has been exploited in the wild. Nonetheless, users are advised to:
– Keep Devices Updated: Install Android patches as soon as they become available to protect against known vulnerabilities.
– Exercise Caution with App Installations: Only download applications from trusted sources and be wary of apps requesting unnecessary permissions.
– Monitor Device Behavior: Stay alert to unusual device behavior, such as unexpected app launches or overlays, which may indicate malicious activity.
Broader Implications
The discovery of Pixnapping highlights the evolving nature of cyber threats targeting mobile devices. It underscores the need for continuous vigilance and proactive security measures from both users and developers. The attack’s reliance on hardware-level vulnerabilities also points to the importance of collaboration between software developers and hardware manufacturers to address security flaws comprehensively.
In conclusion, Pixnapping represents a significant advancement in side-channel attacks, capable of extracting sensitive information from Android devices without user consent or awareness. While mitigation efforts are underway, users must remain proactive in updating their devices and practicing safe app installation habits to safeguard their personal information.