Urgent Alert: Phishing Scam Targets LastPass Users with Fake Maintenance Emails
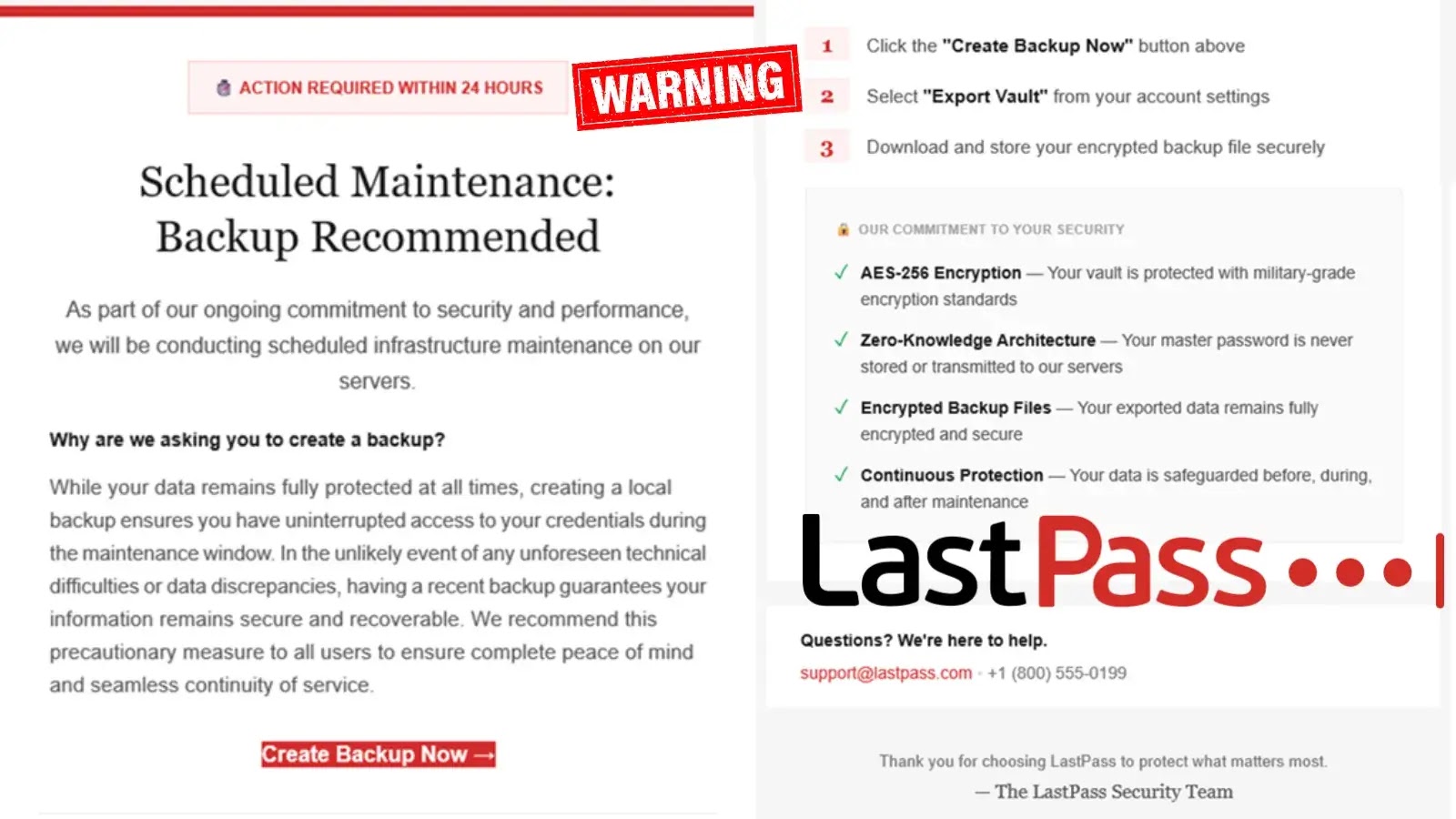
On January 19, 2026, a sophisticated phishing campaign was launched, targeting LastPass users by impersonating the company’s support team. The attackers sent fraudulent emails claiming that urgent maintenance required users to back up their vaults within 24 hours, aiming to steal master passwords.
These deceptive emails employed social engineering tactics to create a false sense of urgency, pressuring recipients to act quickly. LastPass has confirmed that it never requests master passwords or immediate vault backups via email.
The timing of the attack was strategic, coinciding with the U.S. holiday weekend to exploit reduced security staffing and delayed incident response. This period often sees an increase in cyberattacks due to decreased vigilance.
The phishing infrastructure involved two main components: an initial redirect hosted on compromised AWS S3 infrastructure and a spoofed domain designed to mimic legitimate LastPass services.
Users are advised to delete any emails claiming to require LastPass maintenance immediately. Legitimate communications from LastPass will never request master passwords, vault backups, or urgent action via unsolicited emails.
Organizations should implement email security controls to block messages from identified sender addresses and educate staff on phishing indicators, such as artificially urgent language and requests for sensitive credentials.
LastPass is working with third-party partners to dismantle the malicious infrastructure. Users who received these emails are encouraged to report them directly to [email protected] for analysis and tracking.