Sophisticated Phishing Campaign Targets Russian Users with Amnesia RAT and Ransomware
A recent multi-stage phishing campaign has been identified, specifically targeting users in Russia with a combination of ransomware and a remote access trojan (RAT) known as Amnesia RAT. This campaign employs advanced social engineering tactics and leverages multiple public cloud services to distribute its malicious payloads, making detection and mitigation more challenging.
Initial Attack Vector:
The attack begins with phishing emails containing business-themed documents designed to appear routine and harmless. These documents serve as decoys, diverting the victim’s attention while malicious scripts execute in the background. The use of familiar business contexts increases the likelihood of the recipient opening the document and inadvertently initiating the infection process.
Payload Distribution via Cloud Services:
A notable aspect of this campaign is its strategic use of public cloud services to distribute different components of the malware. Scripts are primarily hosted on GitHub, while binary payloads are staged on Dropbox. This separation not only complicates takedown efforts but also enhances the campaign’s resilience by distributing the attack infrastructure across multiple platforms.
Disabling Security Measures:
To facilitate the infection process, the attackers employ a tool called Defendnot to disable Microsoft Defender, the built-in antivirus program on Windows systems. Defendnot tricks Defender into believing that another antivirus product is already installed, thereby deactivating its protective features. This tactic allows the malware to operate undetected and increases the likelihood of a successful attack.
Execution Process:
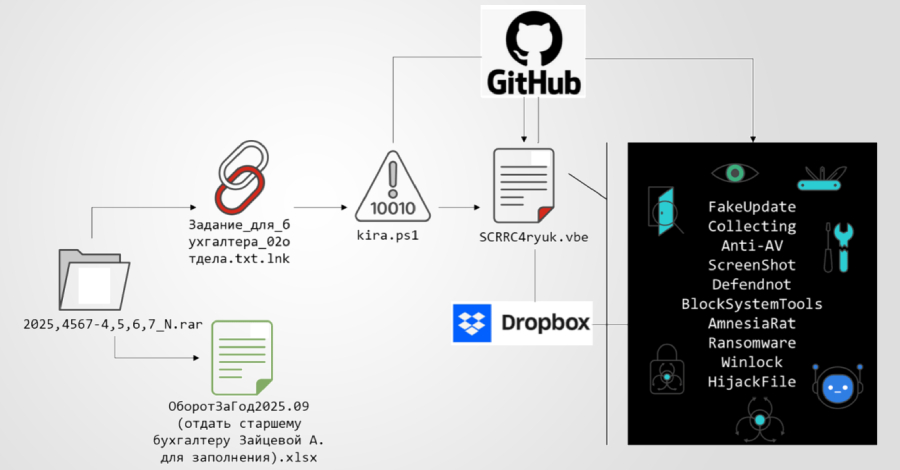
The infection chain involves several steps:
1. Delivery of Malicious Archive: The victim receives a compressed archive containing multiple decoy documents and a malicious Windows shortcut (LNK) file with a Russian-language filename. The LNK file uses a double extension (e.g., Задание_для_бухгалтера_02отдела.txt.lnk) to masquerade as a text file.
2. PowerShell Command Execution: When the LNK file is executed, it runs a PowerShell command that retrieves a first-stage PowerShell script from a GitHub repository. This script establishes a foothold on the system and prepares it for subsequent stages of the attack.
3. Decoy Document Display: To maintain the illusion of legitimacy, the script generates and opens a decoy text document, keeping the victim unaware of the malicious activities occurring in the background.
4. Communication with Attackers: The script sends a message to the attackers via the Telegram Bot API, notifying them of the successful execution of the first stage.
5. Execution of Visual Basic Script: After a deliberate delay, the PowerShell script runs a highly obfuscated Visual Basic Script (VBS) hosted on the same GitHub repository. This VBS acts as a controller, assembling the next-stage payload directly in memory to avoid leaving artifacts on disk.
6. Privilege Escalation: The final-stage script checks if it has elevated privileges. If not, it repeatedly displays a User Account Control (UAC) prompt to the victim, attempting to gain the necessary permissions.
Final Payload Deployment:
Once elevated privileges are obtained, the malware performs several actions to ensure its success:
– Disabling Security Features: The malware configures Microsoft Defender exclusions to prevent scanning of critical directories such as ProgramData, Program Files, Desktop, Downloads, and the system temporary directory.
– System Reconnaissance: It conducts reconnaissance to gather information about the system, which can be used to tailor the attack or for further exploitation.
– Inhibiting Recovery: The malware takes steps to inhibit system recovery options, making it more difficult for the victim to restore their system to a previous state.
– Deploying Main Payloads: Finally, the malware deploys its main payloads, which include the Amnesia RAT and ransomware. The Amnesia RAT provides the attackers with remote access to the compromised system, allowing them to execute commands, exfiltrate data, and perform other malicious activities. The ransomware component encrypts the victim’s files, rendering them inaccessible and demanding a ransom payment for their release.
Implications and Recommendations:
This campaign underscores the evolving sophistication of phishing attacks and the importance of robust cybersecurity measures. Organizations and individuals should be vigilant when receiving unsolicited emails, especially those containing attachments or links. Implementing multi-layered security solutions, regularly updating software, and educating users about phishing tactics are crucial steps in mitigating such threats.
Additionally, monitoring for unusual system behavior, such as unexpected UAC prompts or the sudden disabling of security features, can help in early detection of an ongoing attack. Employing endpoint detection and response (EDR) solutions can provide visibility into malicious activities and facilitate prompt remediation.
As cyber threats continue to evolve, staying informed about the latest attack vectors and maintaining a proactive security posture are essential in defending against sophisticated campaigns like this one.