Pakistan-Linked Cyber Espionage Campaigns Target Indian Government Entities
In a series of sophisticated cyber espionage campaigns, threat actors linked to Pakistan have intensified their efforts to infiltrate Indian government entities. Cybersecurity researchers have identified two notable operations, codenamed Gopher Strike and Sheet Attack, which employ advanced tactics to compromise sensitive systems within India’s defense and aerospace sectors.
Gopher Strike: A Deceptive Phishing Operation
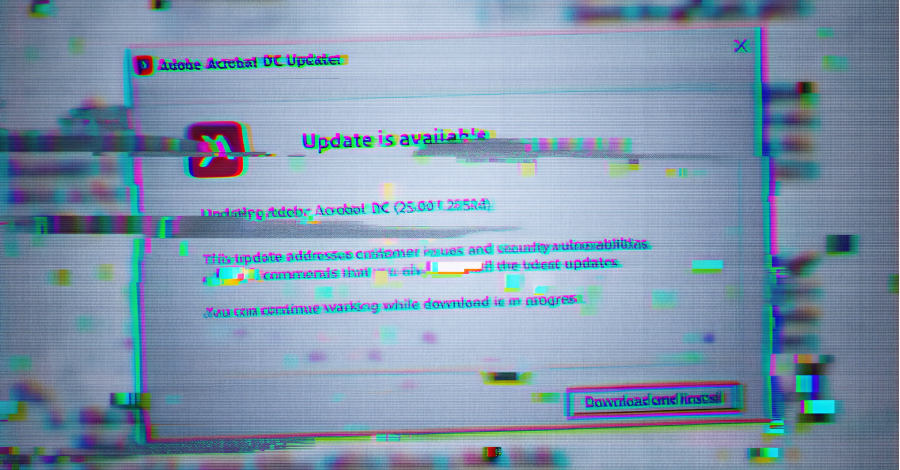
The Gopher Strike campaign, detected in September 2025, utilizes phishing emails to deliver malicious PDF documents. These documents display a blurred image overlaid with a prompt urging recipients to download an update for Adobe Acrobat Reader DC. This deceptive tactic is designed to convince users of the necessity to install the update to view the document’s contents.
Upon clicking the Download and Install button, an ISO image file is downloaded, but only if the request originates from an Indian IP address and the user is operating a Windows system. This geo-targeting strategy ensures that the malicious payload reaches only the intended victims, thereby evading detection by automated analysis tools.
The ISO file contains a Golang-based downloader named GOGITTER, which creates a Visual Basic Script (VBScript) file in specific directories. This script fetches commands from pre-configured command-and-control (C2) servers every 30 seconds, establishing a persistent backdoor into the compromised system. Additionally, GOGITTER checks for the presence of a file named adobe_update.zip and, if absent, downloads it from a private GitHub repository. This archive contains edgehost.exe, a lightweight Golang-based backdoor called GITSHELLPAD, which leverages GitHub repositories for C2 communication.
Sheet Attack: Exploiting Legitimate Services
The Sheet Attack campaign employs legitimate services such as Google Sheets, Firebase, and email for C2 operations. This approach allows the attackers to blend their malicious activities with normal network traffic, making detection more challenging. The campaign’s specifics remain under investigation, but it underscores the evolving tactics of threat actors in utilizing trusted platforms to conduct cyber espionage.
APT36: A Persistent Threat
These campaigns exhibit similarities with the Pakistan-linked Advanced Persistent Threat (APT) group known as APT36, also referred to as Transparent Tribe. Active since at least 2013, APT36 has a history of targeting Indian military, government, and defense-related sectors. The group is notorious for using spear-phishing emails laced with malware disguised as official documents, such as fake Indian Army recruitment forms or COVID-19 advisories.
APT36’s primary tool is the Crimson Remote Access Trojan (RAT), which enables surveillance through file theft, screen capture, and keystroke logging. The group has also deployed Android malware, including CapraRAT, via fake dating and chat apps to infiltrate mobile devices of military personnel and activists. These persistent and stealthy operations highlight APT36’s adaptability and commitment to refining its tactics to avoid detection.
Exploiting Real-World Events
APT36 has a track record of exploiting real-world events to enhance the effectiveness of their campaigns. For instance, following the Pahalgam terror attack, the group launched a cyber attack campaign spoofing India’s Ministry of Defence and disseminated Pahalgam Terror Attack themed documents to distribute malware. These phishing documents were disguised as official government briefings and internal response reports, crafted to resemble legitimate communications. The malicious files contained links leading victims to fake login portals designed to steal government credentials.
Advanced Tactics and Tools
In their recent campaigns, APT36 has demonstrated advanced operational security measures, including geo-filtering to ensure payload delivery exclusively to Indian targets. They have also abused legitimate services like GitHub, Google Sheets, and Firebase to evade detection. The group employs custom Golang-based malware, such as GOGITTER and GITSHELLPAD, with persistence mechanisms enabling prolonged system access. These tactics represent a significant escalation in regional cyber espionage activities.
Targeting Defense and Aerospace Sectors
The primary targets of these campaigns are India’s defense and aerospace sectors. APT36 has been known to target employees in defense establishments, especially those under the Department of Defence Production, using phishing emails with malicious attachments. The group has also targeted prestigious educational institutions like the Indian Institutes of Technology (IITs) and National Institutes of Technology (NITs). These attacks aim to steal classified military intelligence, troop movements, operational plans, and gain access to communications within the Indian Air Force, Army, and Navy.
Social Media Amplification and Disinformation
In addition to direct cyber attacks, APT36 has been linked to social media accounts that amplify unverified cyberattack claims. Accounts like P@kistanCyberForce and CyberLegendX have targeted entities such as Bharti Airtel and the Manohar Parrikar Institute for Defence Studies, often framing their actions as retaliation for geopolitical events. These claims are part of a broader narrative to project cyber prowess, despite lacking evidence of significant impact.
Conclusion
The detection of the Gopher Strike and Sheet Attack campaigns underscores the persistent and evolving threat posed by Pakistan-linked cyber espionage groups like APT36. Their sophisticated tactics, including the use of legitimate services for C2 operations and geo-targeting strategies, highlight the need for robust cybersecurity measures within Indian government entities. Continuous vigilance, advanced threat detection, and comprehensive security protocols are essential to counteract these persistent cyber threats.