OWASP Unveils 2025 Top 10: Addressing Emerging Software Security Threats
The Open Web Application Security Project (OWASP) has released the 2025 edition of its renowned OWASP Top 10, marking the eighth iteration of this critical resource for developers and security professionals. This latest version introduces significant updates, including two new categories, reflecting the evolving landscape of software security threats.
Key Changes in the 2025 Edition
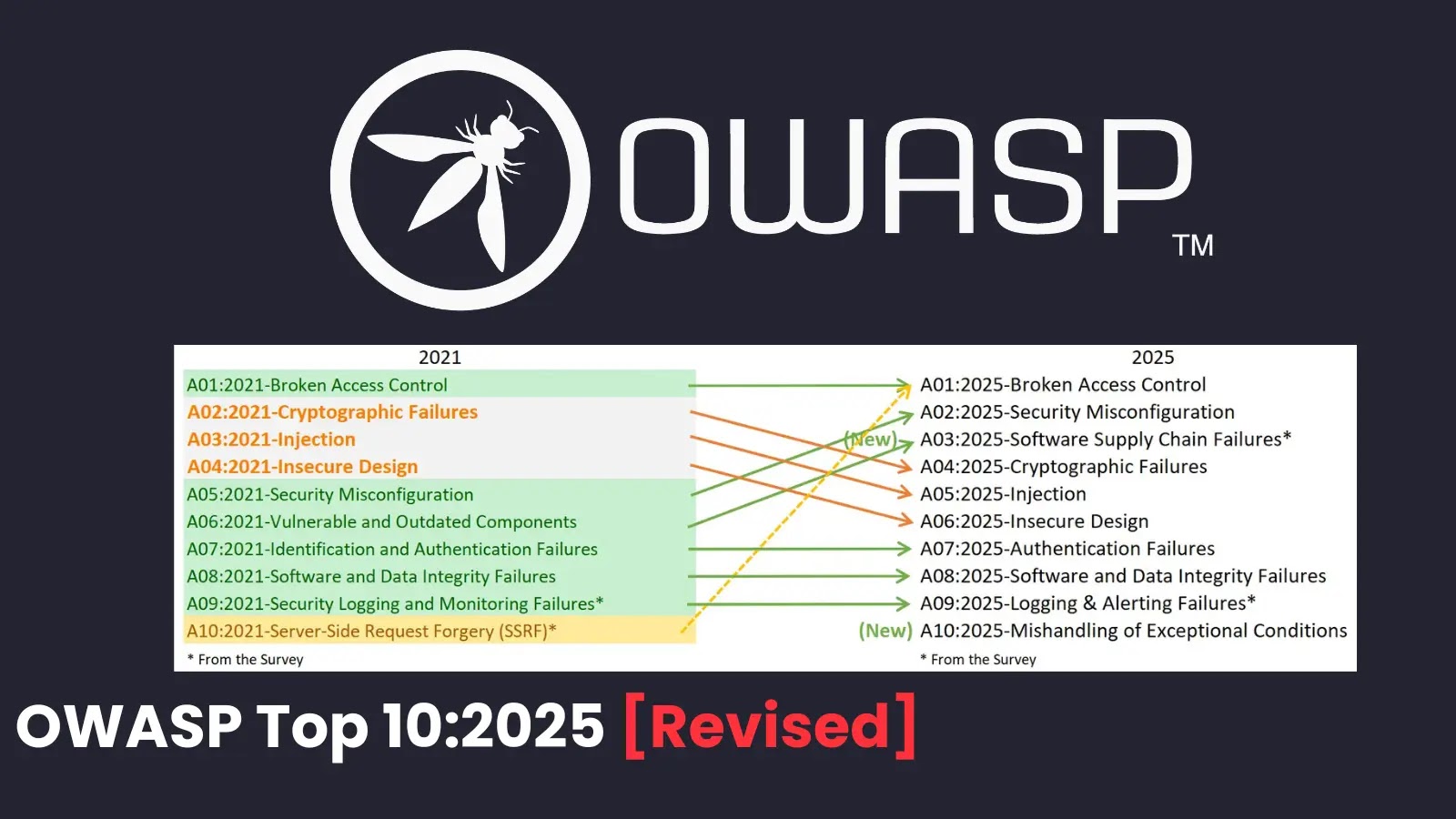
The 2025 OWASP Top 10 introduces two new categories:
1. A03:2025 – Software Supply Chain Failures: This category expands upon the 2021’s Vulnerable and Outdated Components, encompassing broader ecosystem risks such as dependencies, build systems, and distribution infrastructure. It includes five Common Weakness Enumerations (CWEs) and has been highlighted due to its high exploit and impact potential from Common Vulnerabilities and Exposures (CVEs).
2. A10:2025 – Mishandling of Exceptional Conditions: This addition focuses on improper error handling, logical flaws, and insecure failure states, such as failing open during abnormal conditions. Previously scattered under poor code quality, this category addresses how mishandled exceptions can expose sensitive data or enable denial-of-service attacks.
Additionally, the category Server-Side Request Forgery (SSRF) from the 2021 list has been merged into A01:2025 – Broken Access Control, which retains its top position with 40 CWEs affecting 3.73% of tested applications on average.
Detailed Overview of the Top Vulnerabilities
1. A01:2025 – Broken Access Control: Flaws that allow attackers to bypass authorization mechanisms and gain unauthorized access to data or functions. This category includes 40 CWEs and affects approximately 3.73% of tested applications.
2. A02:2025 – Security Misconfiguration: Weak default settings, exposed services, or inconsistent security controls across environments. This category impacts 3.00% of applications and has moved up from the fifth position in 2021 due to increased configuration complexity.
3. A03:2025 – Software Supply Chain Failures: Vulnerabilities in dependencies, continuous integration/continuous deployment (CI/CD) systems, build processes, and distribution infrastructure. This new category covers five CWEs with high exploit scores.
4. A04:2025 – Cryptographic Failures: Insecure or outdated encryption practices leading to sensitive data exposure or system compromise. This category includes 32 CWEs and affects 3.80% of applications, dropping from the second position in 2021.
5. A05:2025 – Injection: Input validation flaws such as SQL, OS command, or cross-site scripting (XSS) injections. Associated with 38 CWEs and numerous CVEs, this category has dropped from the third position in 2021.
6. A06:2025 – Insecure Design: Risks arising from poor architectural decisions or inadequate threat modeling during the design phase. This category has dropped from the fourth position in 2021, indicating industry improvements in secure design practices.
7. A07:2025 – Authentication Failures: Issues in login mechanisms, password policies, or session handling that enable unauthorized access. This category covers 36 CWEs and maintains its seventh position, renamed from Identification and Authentication Failures.
8. A08:2025 – Software or Data Integrity Failures: Failures to verify the integrity of software, code, or data, allowing tampering. This category maintains its eighth position with a minor focus on integrity verification.
9. A09:2025 – Logging & Alerting Failures: Gaps in monitoring, logging, or alerting that hinder the detection and response to security incidents. This category emphasizes actionable alerts over mere monitoring.
10. A10:2025 – Mishandling of Exceptional Conditions: Improper error handling, logical flaws, and insecure failure states that can expose sensitive data or enable denial-of-service attacks. This new category includes 24 CWEs focused on these issues.
Real-World Impacts
The OWASP Top 10 is informed by real-world incidents and emerging trends. For instance, in 2024 alone, over $1.42 billion was lost across 149 documented incidents due to vulnerabilities such as access control flaws ($953M), logic errors ($63M), and reentrancy attacks ($35M). These figures underscore the urgent need for robust security practices in software development.
Conclusion
The OWASP Top 10 2025 serves as a critical resource for developers, security professionals, and organizations aiming to prioritize web application risks. By understanding and addressing these top vulnerabilities, stakeholders can enhance the security posture of their applications and protect against emerging threats.