Harnessing Threat Intelligence Feeds to Rapidly Counteract Malware Attacks
Article Text:
In today’s digital landscape, organizations are under constant siege from a myriad of malware threats, including ransomware, phishing schemes, and zero-day exploits. The rapid evolution of these threats necessitates a proactive and informed defense strategy. Threat intelligence feeds have emerged as a pivotal tool, offering real-time, actionable data that empowers security teams to identify and neutralize attacks before they inflict significant damage.
Understanding Threat Intelligence Feeds
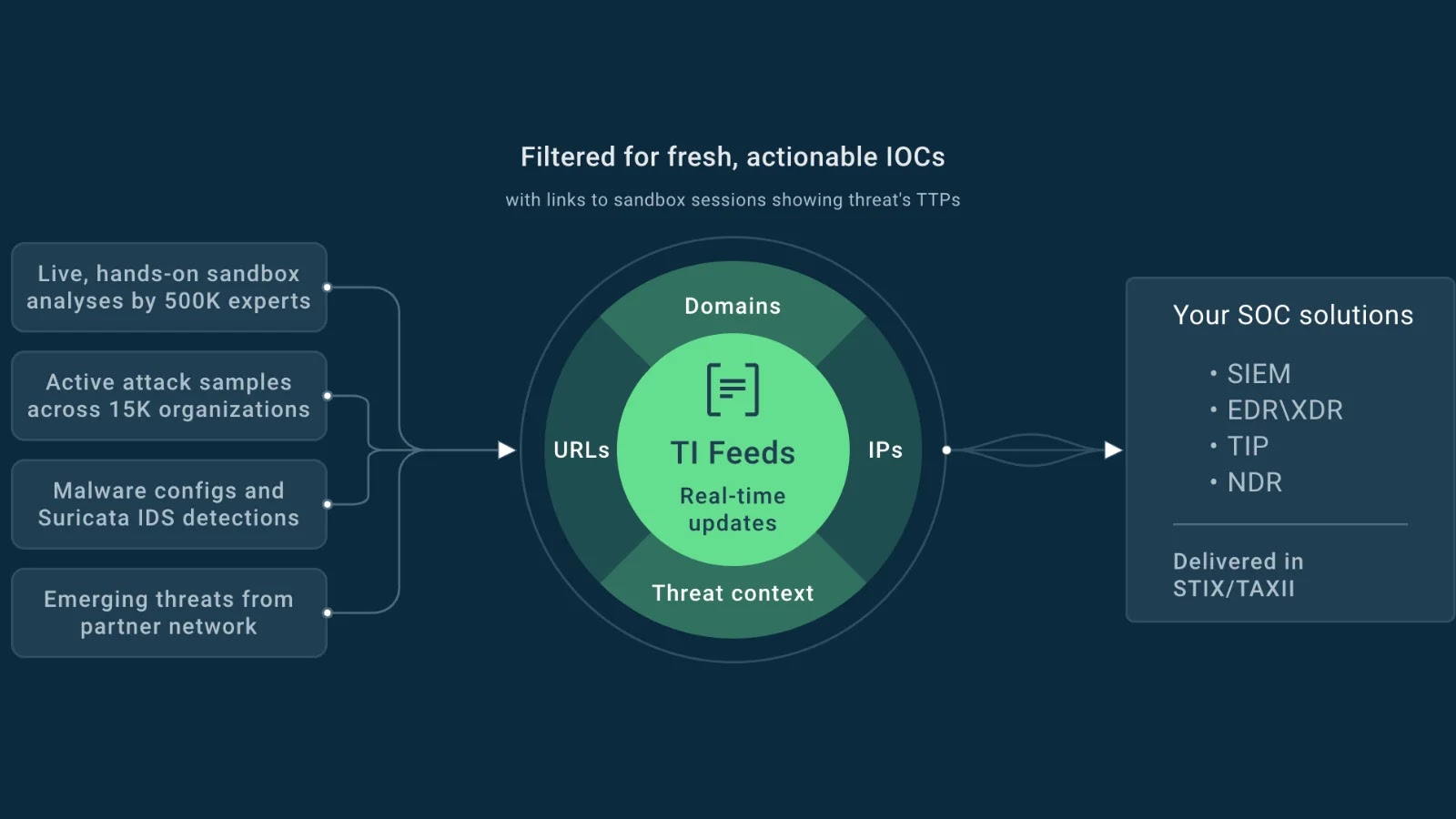
Threat intelligence feeds are curated streams of data that aggregate indicators of compromise (IOCs) such as malicious IP addresses, domains, URLs, and file hashes from a multitude of global sources. These feeds are enriched with contextual information, including malware family classifications and severity assessments, providing a comprehensive view of potential threats. By integrating this intelligence into Security Operations Centers (SOCs), organizations can transition from a reactive stance to a proactive defense posture, thereby mitigating the impact of potential breaches.
The Role of ANY.RUN in Threat Intelligence
ANY.RUN, a prominent provider of malware analysis solutions, exemplifies the effective utilization of threat intelligence feeds through its cloud-based sandbox platform. With a community comprising over 500,000 analysts and 15,000 enterprises submitting more than 16,000 tasks daily, ANY.RUN processes a vast array of indicators. Employing proprietary algorithms, the platform meticulously filters out false positives, ensuring the reliability of the intelligence provided. These feeds, available in standardized formats such as STIX or MISP, are updated in near real-time and include detailed information like timestamps, related objects, and external references to sandbox sessions. This structured approach facilitates seamless integration with existing security infrastructures, including SIEM, SOAR, and firewall systems, thereby automating threat enrichment and response processes.
Enhancing Incident Triage with Threat Intelligence Feeds
During the critical phase of incident triage, where security teams are inundated with alerts, threat intelligence feeds serve as a vital tool to distinguish genuine threats from false alarms. By correlating incoming alerts with known IOCs, analysts can validate true positives and prioritize high-risk events effectively. For instance, if an intrusion detection system flags a suspicious IP address, the threat intelligence feed can reveal its association with a known ransomware command-and-control server, complete with campaign details and initial detection dates. This contextual information enables immediate actions such as isolating affected endpoints, thereby reducing the mean time to detect and minimizing resource expenditure on false alarms.
Real-World Application: A Financial Institution’s Experience
Consider a scenario where a financial institution detects an outbound connection to an unfamiliar IP address. By cross-referencing this IP with a threat intelligence feed, the security team confirms its malicious nature, linked to a known ransomware group. Promptly escalating the alert and blocking the connection, the team successfully averts a potential data breach within minutes. Such capabilities not only enhance compliance with regulations like the General Data Protection Regulation (GDPR) but also safeguard revenue by preventing costly operational disruptions.
Proactive Threat Hunting and Post-Incident Analysis
Beyond incident triage, threat intelligence feeds are instrumental in proactive threat hunting. Analysts can utilize these feeds to navigate through network logs and endpoint data, correlating IOCs with known tactics, techniques, and procedures (TTPs) to uncover hidden anomalies. For example, a retail company might use feed data on a new ransomware payload to scan logs, identifying and quarantining a compromised endpoint before the infection spreads, thereby protecting customer data and maintaining brand trust.
In post-incident analysis, threat intelligence feeds assist in reconstructing attack narratives by mapping incidents to global threat trends. Following a manufacturing breach via spear-phishing, a security team can trace the incident to a nation-state actor exploiting unpatched vulnerabilities with custom scripts. Insights from the feed prompt the implementation of patches, development of new detection rules, and targeted training, thereby reducing recovery time and fortifying defenses against similar future threats.
Broader Benefits of Threat Intelligence Feeds
The adoption of threat intelligence feeds offers organizations several overarching advantages:
– Early Detection of Emerging Malware: By providing timely information on new threats, organizations can implement preventive measures before attacks materialize.
– Accelerated Response Times: Automated integration of threat intelligence into security systems enables swift identification and mitigation of threats, reducing potential damage.
– Data-Driven Decision Making: Access to comprehensive threat data allows organizations to align their security strategies with business objectives, ensuring resources are allocated effectively.
– Cost Reduction: Automating the ingestion of IOCs lowers remediation costs by decreasing the need for manual intervention and reducing downtime.
– Enhanced Uptime: Proactive threat management ensures continuous operation of critical systems, maintaining business continuity.
– Proactive Security Posture: Regular updates from threat intelligence feeds keep security teams informed about the latest threats, fostering a culture of vigilance and preparedness.
Conclusion
In an era where cyber threats are becoming increasingly sophisticated and pervasive, the integration of threat intelligence feeds into organizational security frameworks is not merely advantageous—it is imperative. By leveraging real-time, actionable data, organizations can detect and neutralize malware attacks swiftly, thereby protecting their assets, reputation, and operational continuity. As the cyber threat landscape continues to evolve, staying ahead requires a commitment to proactive defense strategies, with threat intelligence feeds playing a central role in this endeavor.