A newly identified malware campaign, named OBSCURE#BAT, is using fake CAPTCHA pages and trojanized software downloads to trick users into executing malicious scripts. The malware is designed to establish persistence, evade detection, and deploy the r77 rootkit, allowing attackers to maintain deep control over compromised systems.
How the Attack Works
The OBSCURE#BAT campaign uses social engineering techniques to convince users to execute harmful scripts on their own systems. The infection process typically follows these steps:
- Fake CAPTCHA Pages – Users encounter counterfeit CAPTCHA verification pages, designed to look like standard security checks. Instead of verifying user activity, the page copies a malicious command to the clipboard and instructs users to paste it into the Windows Run dialog.
- Trojanized Software Downloads – The malware is also distributed through seemingly legitimate software, such as modified versions of Tor Browser, VoIP apps, and messaging clients. Users who download these altered programs unknowingly execute the malicious script.
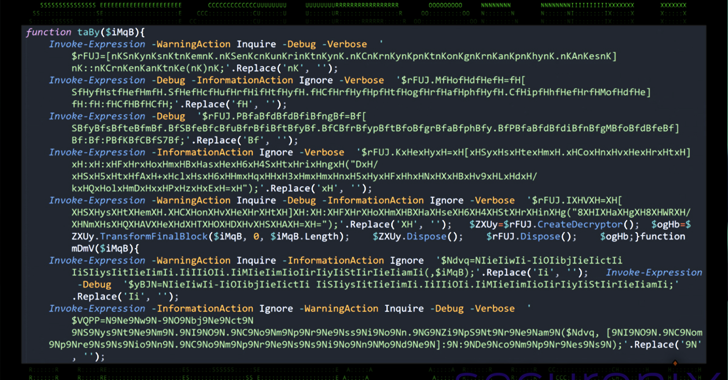
- Execution of Malicious Batch Scripts – The downloaded files include heavily obfuscated batch scripts that invoke PowerShell commands. These scripts download and install additional malware components, modify system settings, and establish a persistent foothold on the device.
Stealth Techniques and Persistence Mechanisms
OBSCURE#BAT employs multiple advanced evasion strategies to avoid detection and removal:
- Rootkit Deployment – The malware installs the r77 rootkit, which hides files, processes, and registry keys associated with the infection. This makes it nearly invisible to traditional system monitoring tools.
- API Hooking – The malware intercepts and modifies system API calls, allowing it to manipulate how the operating system reports active processes and services.
- Obfuscated Batch Files – The scripts used in the attack are designed to be unreadable to standard security tools, making detection more difficult.
- Scheduled Task Persistence – The malware configures Windows Task Scheduler to automatically re-execute itself, ensuring it remains active even after system reboots.
Targeted Regions and Potential Impact
The campaign appears to focus primarily on English-speaking users in the United States, Canada, Germany, and the United Kingdom. The nature of the attack suggests that individuals downloading privacy-focused tools such as Tor Browser may be deliberately targeted.
How to Protect Against OBSCURE#BAT
Users can take several steps to mitigate the risk of infection:
- Be Cautious with CAPTCHA Pages – Avoid interacting with CAPTCHA pages that ask you to copy and paste code into system dialogs. Legitimate CAPTCHA verifications do not require manual script execution.
- Download Software from Official Sources – Only install applications from verified publishers and official websites. Avoid downloading modified versions of security or privacy-focused tools from unknown sources.
- Monitor System Behavior – Unusual system slowdowns, hidden files, and missing processes in Task Manager could indicate a rootkit infection.
- Use Updated Security Software – Antivirus and anti-malware solutions with rootkit detection capabilities can help identify and remove threats like OBSCURE#BAT.
Why This Malware is Dangerous
Unlike traditional malware that relies on exploiting vulnerabilities, OBSCURE#BAT manipulates users into infecting themselves by disguising its malicious actions as routine security verifications. The integration of rootkit technology allows attackers to maintain long-term control over compromised devices without being easily detected.
This campaign underscores the growing trend of social engineering-based malware attacks, where attackers rely on human error rather than software vulnerabilities to breach systems.