North Korean Hackers Exploit Google’s Find Hub to Remotely Wipe Devices
In a recent cybersecurity development, the North Korean-linked hacking group known as Konni—also referred to as Earth Imp, Opal Sleet, Osmium, TA406, and Vedalia—has been implicated in a series of sophisticated attacks targeting both Android and Windows platforms. These operations are primarily aimed at data exfiltration and remote device control.
According to a detailed report by the Genians Security Center (GSC), the attackers masqueraded as psychological counselors and North Korean human rights activists. They distributed malware camouflaged as stress-relief applications, thereby deceiving unsuspecting users into downloading malicious software.
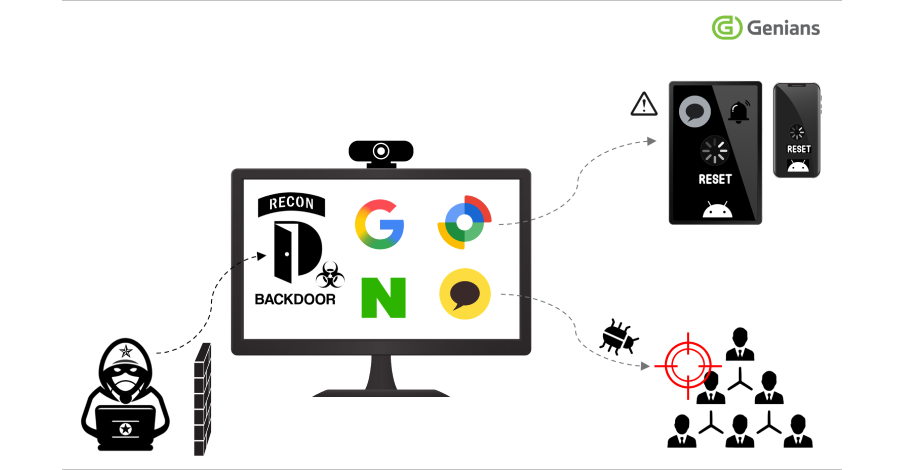
A particularly alarming aspect of these attacks is the exploitation of Google’s asset tracking service, Find Hub (formerly known as Find My Device). The hackers leveraged this legitimate service to remotely reset victim’s devices, resulting in unauthorized deletion of personal data. This activity was first identified in early September 2025.
This marks the first instance where Konni has weaponized legitimate device management functions to execute remote resets on mobile devices. The attack sequence typically begins with spear-phishing emails, where attackers impersonate credible entities such as the National Tax Service. These emails contain malicious attachments designed to deploy remote access trojans like Lilith RAT, enabling the attackers to gain control over compromised systems and deliver additional payloads.
Once the initial intrusion is successful, the attackers maintain a low profile within the compromised system, often remaining undetected for over a year. During this period, they conduct surveillance through webcams and operate the system during the user’s absence. The access obtained allows for extensive system control and information gathering, while evasion tactics ensure prolonged concealment.
The malware deployed on the victim’s computer facilitates internal reconnaissance and monitoring. It also enables the exfiltration of Google and Naver account credentials. With the stolen Google credentials, the attackers log into Google’s Find Hub to initiate remote wipes of the victim’s devices.
In one documented case, the attackers accessed a recovery email account registered with Naver, deleted security alert emails from Google, and emptied the inbox’s trash folder to eliminate evidence of their activities.
The malware is often disseminated via messaging apps in the form of a ZIP archive containing a malicious Microsoft Installer (MSI) package named Stress Clear.msi. This package exploits a valid signature issued to a Chinese company, lending an appearance of legitimacy. Upon execution, it runs a batch script for initial setup and a Visual Basic Script (VB Script) that displays a fake error message about a language pack compatibility issue, while executing malicious commands in the background.
These commands include launching an AutoIt script configured to run every minute through a scheduled task, executing additional commands received from an external server. While the malware shares some characteristics with Lilith RAT, it has been designated as EndRAT (also known as EndClient RAT) due to observed differences.
The supported commands of EndRAT include:
– shellStart: Initiates a remote shell session
– shellStop: Terminates the remote shell
– refresh: Sends system information
– list: Lists drives or root directory
– goUp: Moves up one directory
– download: Exfiltrates a file
– upload: Receives a file
– run: Executes a program on the host
– delete: Deletes a file on the host
Genians reports that Konni APT actors have also utilized an AutoIt script to launch Remcos RAT version 7.0.4, released on September 10, 2025. This indicates the adversary’s active use of newer versions of the trojan in its attacks. Additionally, Quasar RAT and RftRAT, another trojan previously employed by Kimsuky in 2023, have been observed on victim devices.
These findings suggest that the malware is tailored for operations focused on Korea, requiring substantial effort for relevant data acquisition and in-depth analysis.