Cybersecurity experts have identified a sophisticated campaign utilizing an evolved form of the FileFix social engineering technique to distribute the StealC information-stealing malware. This operation employs a highly convincing, multilingual phishing website, such as a counterfeit Facebook Security page, incorporating advanced obfuscation and anti-analysis methods to evade detection.
The attack sequence begins with the FileFix method, enticing users to execute an initial payload. This payload subsequently downloads seemingly harmless images from a Bitbucket repository, which actually contain the malicious components. By leveraging a reputable source code hosting platform, the attackers exploit the inherent trust associated with such services to bypass security measures.
FileFix, first introduced as a proof-of-concept by security researcher mrd0x in June 2025, differs from the earlier ClickFix technique. Unlike ClickFix, which required users to open the Windows Run dialog and paste an obfuscated command to complete fake CAPTCHA verifications, FileFix manipulates the web browser’s file upload feature. This deception leads users to copy and paste a command into the File Explorer’s address bar, resulting in local execution on the victim’s machine.
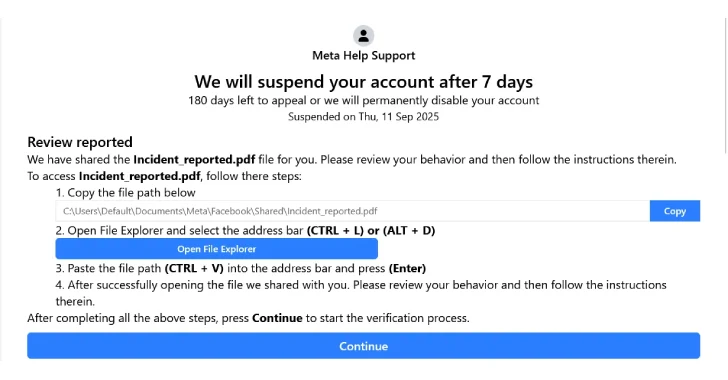
The attack initiates when a victim is redirected to a phishing site, often from an email warning about potential suspension of their Facebook account due to alleged policy violations. The email urges users to appeal the decision by clicking a provided button. The phishing page is heavily obfuscated and employs techniques like junk code and fragmentation to complicate analysis.
Upon clicking the appeal button, the victim is instructed to access a PDF detailing the supposed policy violation by copying and pasting a provided path into the File Explorer’s address bar. While the displayed path appears harmless, clicking the button surreptitiously copies a malicious command to the user’s clipboard. This command is a multi-stage PowerShell script that downloads the aforementioned image, decodes it into the next-stage payload, and ultimately runs a Go-based loader that unpacks shellcode responsible for launching StealC.
FileFix offers a significant advantage over ClickFix by exploiting a commonly used browser feature, rather than relying on the Run dialog or Terminal app, which system administrators might restrict as a security measure. However, this approach also means that the payload is executed by the web browser, making it more likely to be detected during investigations or by security products.
The adversaries behind this attack have demonstrated considerable investment in their methods, meticulously crafting the phishing infrastructure, payload delivery, and supporting elements to maximize both evasion and impact.
This disclosure coincides with reports from Doppel detailing another campaign that combines fake support portals, Cloudflare CAPTCHA error pages, and clipboard hijacking—referred to as ClickFix—to socially engineer victims into executing malicious PowerShell code. This code downloads and runs an AutoHotkey (AHK) script designed to profile the compromised host and deliver additional payloads, including AnyDesk, TeamViewer, information stealers, and clipper malware.
The cybersecurity community continues to observe the rapid evolution of social engineering tactics like FileFix and ClickFix, underscoring the need for heightened vigilance and robust security measures to protect against such sophisticated threats.